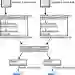
The success of quantum circuits in providing reliable outcomes for a given problem depends on the gate count and depth in near-term noisy quantum computers. Quantum circuit compilers that decompose high-level gates to native gates of the hardware and optimize the circuit play a key role in quantum computing. However, the quality and time complexity of the optimization process can vary significantly especially for practically relevant large-scale quantum circuits. As a result, third-party (often less-trusted/untrusted) compilers have emerged, claiming to provide better and faster optimization of complex quantum circuits than so-called trusted compilers. However, untrusted compilers can pose severe security risks, such as the theft of sensitive intellectual property (IP) embedded within the quantum circuit. We propose an obfuscation technique for quantum circuits using randomized reversible gates to protect them from such attacks during compilation. The idea is to insert a small random circuit into the original circuit and send it to the untrusted compiler. Since the circuit function is corrupted, the adversary may get incorrect IP. However, the user may also get incorrect output post-compilation. To circumvent this issue, we concatenate the inverse of the random circuit in the compiled circuit to recover the original functionality. We demonstrate the practicality of our method by conducting exhaustive experiments on a set of benchmark circuits and measuring the quality of obfuscation by calculating the Total Variation Distance (TVD) metric. Our method achieves TVD of up to 1.92 and performs at least 2X better than a previously reported obfuscation method. We also propose a novel adversarial reverse engineering (RE) approach and show that the proposed obfuscation is resilient against RE attacks. The proposed technique introduces minimal degradation in fidelity (~1% to ~3% on average).
翻译:量子电路的成功解决给定问题的能力依赖于量子电路中门的数量和深度,近期被噪声干扰的量子计算机中的原生门需要高水平门的分解和优化。量子电路编译器将高级门分解成硬件原生门并优化电路,在量子计算中扮演着关键角色。然而,编译的优化质量和时间复杂度可以因实际使用的大型量子电路而有很大区别。作为结果,出现了第三方编译器(通常是不受信任的)声称能够提供比所谓的可信编译器更好和更快的大型量子电路的优化。但是,不受信任的编译器可能会对量子电路中嵌入的敏感知识产权(IP)造成严重的安全风险。我们提出了一种使用随机可逆门对量子电路进行混淆的技术,以在编译期间保护电路。这个想法是将一个小的随机电路插入原始电路中,并将其发送到不受信任的编译器。由于电路的功能已被破坏,攻击者可能会获取不正确的IP。然而,用户也可能在编译后得到不正确的输出。为了解决这个问题,我们在编译后的电路中连接随机电路的逆来恢复原始功能。我们通过在一组基准电路上进行彻底的实验,并通过计算总差距度量(TVD)来测量混淆质量,展示了我们方法的实用性。我们的方法达到了最大1.92的TVD,并且至少比以前报告的混淆方法好2倍。我们还提出了一种新的对抗性反向工程(RE)方法,并展示了所提出的混淆对于RE攻击的强韧性。所提出的方法对于多数情况而言引入的保真度损耗最小(平均为1%到3%)。