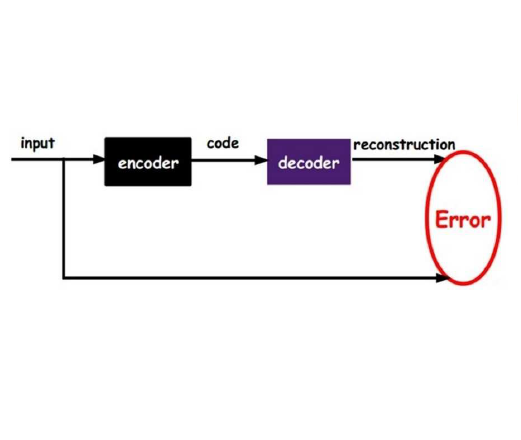
This paper highlights vulnerabilities of deep learning-driven semantic communications to backdoor (Trojan) attacks. Semantic communications aims to convey a desired meaning while transferring information from a transmitter to its receiver. An encoder-decoder pair that is represented by two deep neural networks (DNNs) as part of an autoencoder is trained to reconstruct signals such as images at the receiver by transmitting latent features of small size over a limited number of channel uses. In the meantime, another DNN of a semantic task classifier at the receiver is jointly trained with the autoencoder to check the meaning conveyed to the receiver. The complex decision space of the DNNs makes semantic communications susceptible to adversarial manipulations. In a backdoor (Trojan) attack, the adversary adds triggers to a small portion of training samples and changes the label to a target label. When the transfer of images is considered, the triggers can be added to the images or equivalently to the corresponding transmitted or received signals. In test time, the adversary activates these triggers by providing poisoned samples as input to the encoder (or decoder) of semantic communications. The backdoor attack can effectively change the semantic information transferred for the poisoned input samples to a target meaning. As the performance of semantic communications improves with the signal-to-noise ratio and the number of channel uses, the success of the backdoor attack increases as well. Also, increasing the Trojan ratio in training data makes the attack more successful. In the meantime, the effect of this attack on the unpoisoned input samples remains limited. Overall, this paper shows that the backdoor attack poses a serious threat to semantic communications and presents novel design guidelines to preserve the meaning of transferred information in the presence of backdoor attacks.
翻译:本文强调了深学习驱动的语义通信到后门( Trojan) 攻击的弱点。 语义通信的目的是在将信息从发报器传输到接收器时传达一个理想的含义。 由两个深神经网络( DNN)作为自动编码器一部分的编码解码对配方, 训练其通过在有限的频道用途中传输小尺寸的图像来重建接收器图像等信号。 与此同时, 接收器中另一个语义任务分类器的DNN与自动编码器共同培训, 以检查向接收器传递的含义。 DNNNs 复杂的决定空间使得语义通信容易受到对立的操纵。 在后门( Trojan) 攻击中, 鼠标添加了一小部分训练样本, 并将标签改为目标标签。 当考虑图像传输时, 触发器可以添加到纸面或相应的向后门发送或收到的攻击信号。 在测试期间, 敌人启动这些非语义的触发器, 提供有毒的样本, 作为向严重电路标( or decoder) 发送的电路路路路路段设计指令时, 将有效使用Seal 向后传送数据, 。 状态的信号显示性变变换成Semar 。 状态数据, 状态变变变变换为Semarde 。 。 此变换成Stor 。 向后变现显示, 性演变变变变变变变变变变变变 。 。