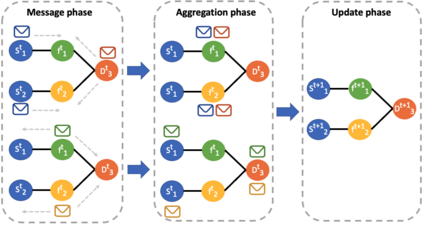
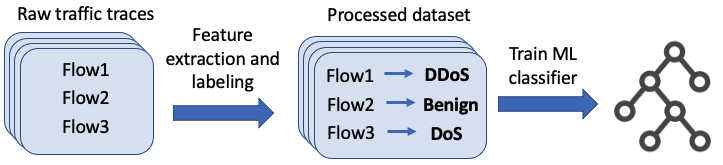
The last few years have seen an increasing wave of attacks with serious economic and privacy damages, which evinces the need for accurate Network Intrusion Detection Systems (NIDS). Recent works propose the use of Machine Learning (ML) techniques for building such systems (e.g., decision trees, neural networks). However, existing ML-based NIDS are barely robust to common adversarial attacks, which limits their applicability to real networks. A fundamental problem of these solutions is that they treat and classify flows independently. In contrast, in this paper we argue the importance of focusing on the structural patterns of attacks, by capturing not only the individual flow features, but also the relations between different flows (e.g., the source/destination hosts they share). To this end, we use a graph representation that keeps flow records and their relationships, and propose a novel Graph Neural Network (GNN) model tailored to process and learn from such graph-structured information. In our evaluation, we first show that the proposed GNN model achieves state-of-the-art results in the well-known CIC-IDS2017 dataset. Moreover, we assess the robustness of our solution under two common adversarial attacks, that intentionally modify the packet size and inter-arrival times to avoid detection. The results show that our model is able to maintain the same level of accuracy as in previous experiments, while state-of-the-art ML techniques degrade up to 50% their accuracy (F1-score) under these attacks. This unprecedented level of robustness is mainly induced by the capability of our GNN model to learn flow patterns of attacks structured as graphs.
翻译:近些年来,以ML为基础的NIDS几乎无法抵御共同的对抗性攻击,这些攻击限制了其对真实网络的适用性。这些解决办法的一个基本问题是它们独立地处理和分类流动。相比之下,我们在本文件中认为,不仅需要精确的网络入侵探测系统(NIDS),而且需要集中关注攻击的结构模式,不仅要捕捉个别流动特征,还要捕捉不同流动(例如,它们共享的源/目的地主机)之间的关系。为此,我们使用图表显示,保存流动记录及其关系,并提出一个新的图表神经网络模型,以便处理和学习这些图表结构化信息。在我们的评估中,我们首先显示,拟议的GNNN模型在众所周知的CIC-IDS-2017模型中取得了最先进的状态结果,同时通过两个众所周知的CIC-IDS-2017模型,以及不同流动(例如,它们共享的源/目的地主机体)之间的关系,建议使用机器学习技术来建立这种系统化技术来建立这些系统(GNNN) 。此外,我们用图表表示,我们这个模型的精确性模型的精确性是用来在常规攻击的模型中学习我们共同的精确度, 的模型中,我们用这种精确性模型来测量的模型来显示。