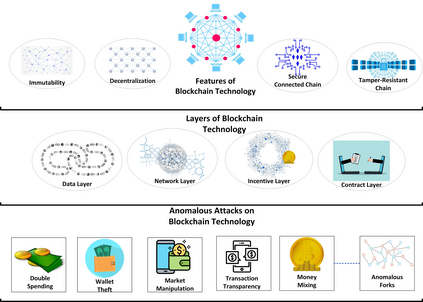
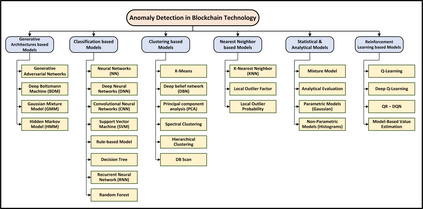
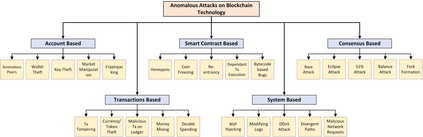
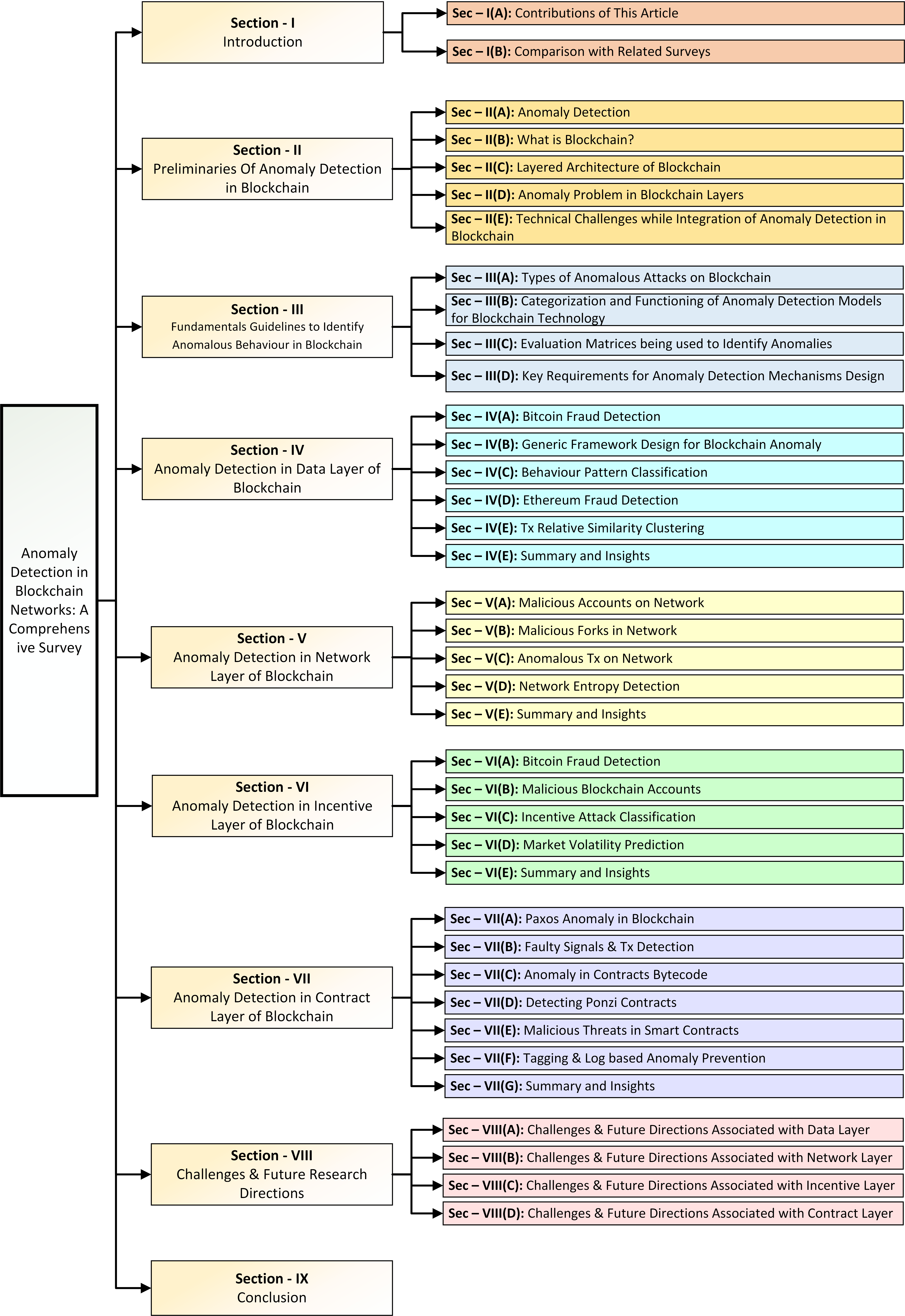
Over the past decade, blockchain technology has attracted a huge attention from both industry and academia because it can be integrated with a large number of everyday applications of modern information and communication technologies (ICT). Peer-to-peer (P2P) architecture of blockchain enhances these applications by providing strong security and trust-oriented guarantees, such as immutability, verifiability, and decentralization. Despite these incredible features that blockchain technology brings to these ICT applications, recent research has indicated that the strong guarantees are not sufficient enough and blockchain networks may still be prone to various security, privacy, and reliability issues. In order to overcome these issues, it is important to identify the anomalous behaviour within the actionable time frame. In this article, we provide an in-depth survey regarding integration of anomaly detection models in blockchain technology. For this, we first discuss how anomaly detection can aid in ensuring security of blockchain based applications. Then, we demonstrate certain fundamental evaluation metrics and key requirements that can play a critical role while developing anomaly detection models for blockchain. Afterwards, we present a thorough survey of various anomaly detection models from the perspective of each layer of blockchain. Finally, we conclude the article by highlighting certain important challenges alongside discussing how they can serve as future research directions for new researchers in the field.
翻译:过去十年来,供应链技术吸引了产业和学术界的极大关注,因为它可以与现代信息和通信技术(信通技术)的大量日常应用结合起来。 供应链的同侪(P2P)结构通过提供强有力的安全和以信任为导向的保障,例如不流动、可核查和权力下放,加强了这些应用。尽管供应链技术给这些信通技术应用带来了这些令人难以置信的特征,但最近的研究表明,强有力的保障不够充分,而供应链网络可能仍然容易出现各种安全、隐私和可靠性问题。为了解决这些问题,必须在可操作的时间框架内查明异常行为。在本篇文章中,我们深入调查将异常检测模型纳入闭塞技术的情况。为此,我们首先讨论异常检测如何有助于确保以链为基础的应用程序的安全。然后,我们展示某些基本的评估指标和关键要求,这些评估指标和关键要求可以发挥关键作用,同时为障碍链开发异常检测模型。我们从每个链层的角度对各种异常检测模型进行彻底调查。我们必须从可操作的时间框架内找出这些异常现象。我们提供深入的调查,关于将异常检测模型纳入闭塞技术中的深度调查。在这方面,我们首先讨论异常检测异常现象如何使研究人员了解未来研究成为重要的实地。我们的结论。