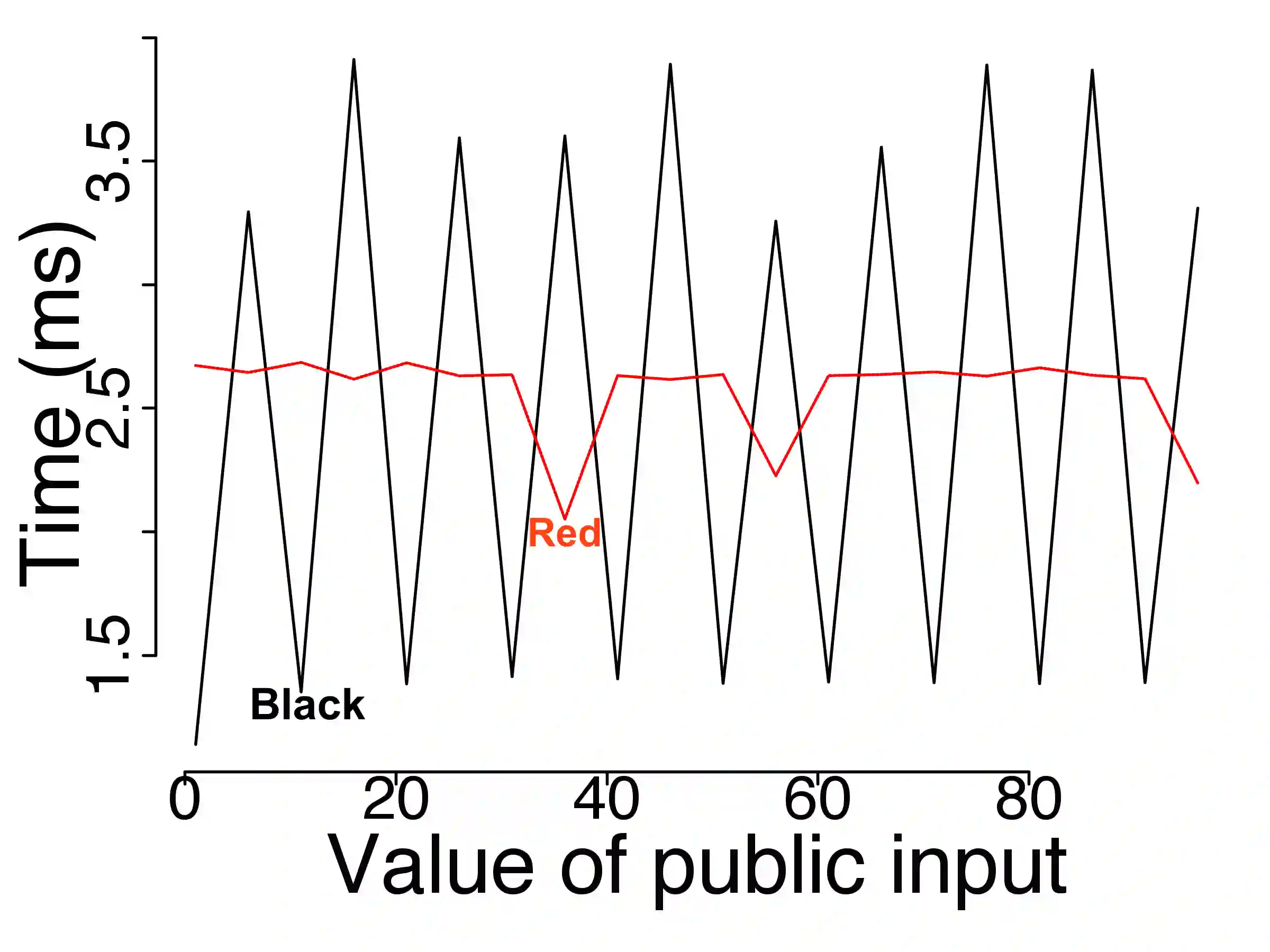
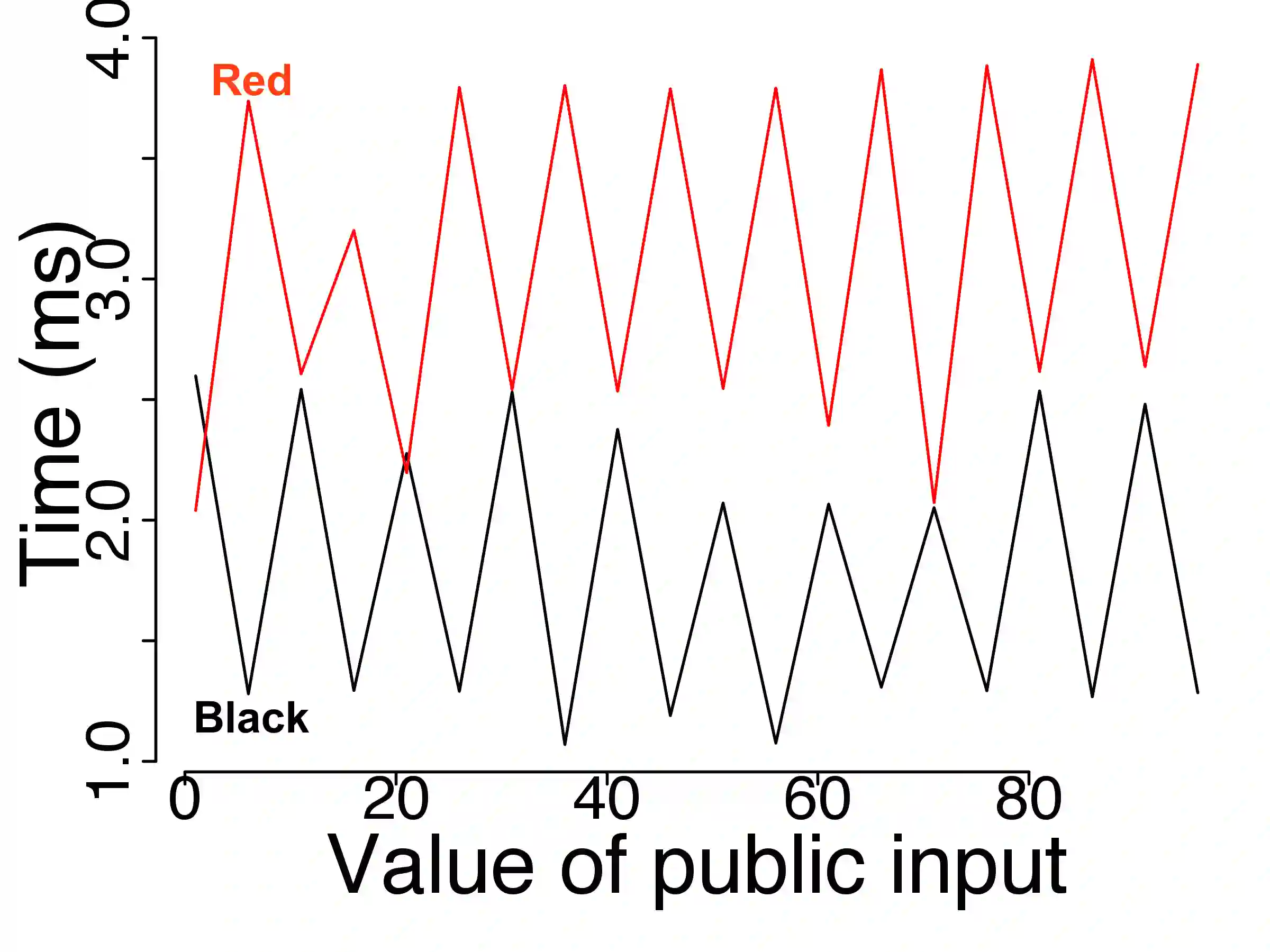
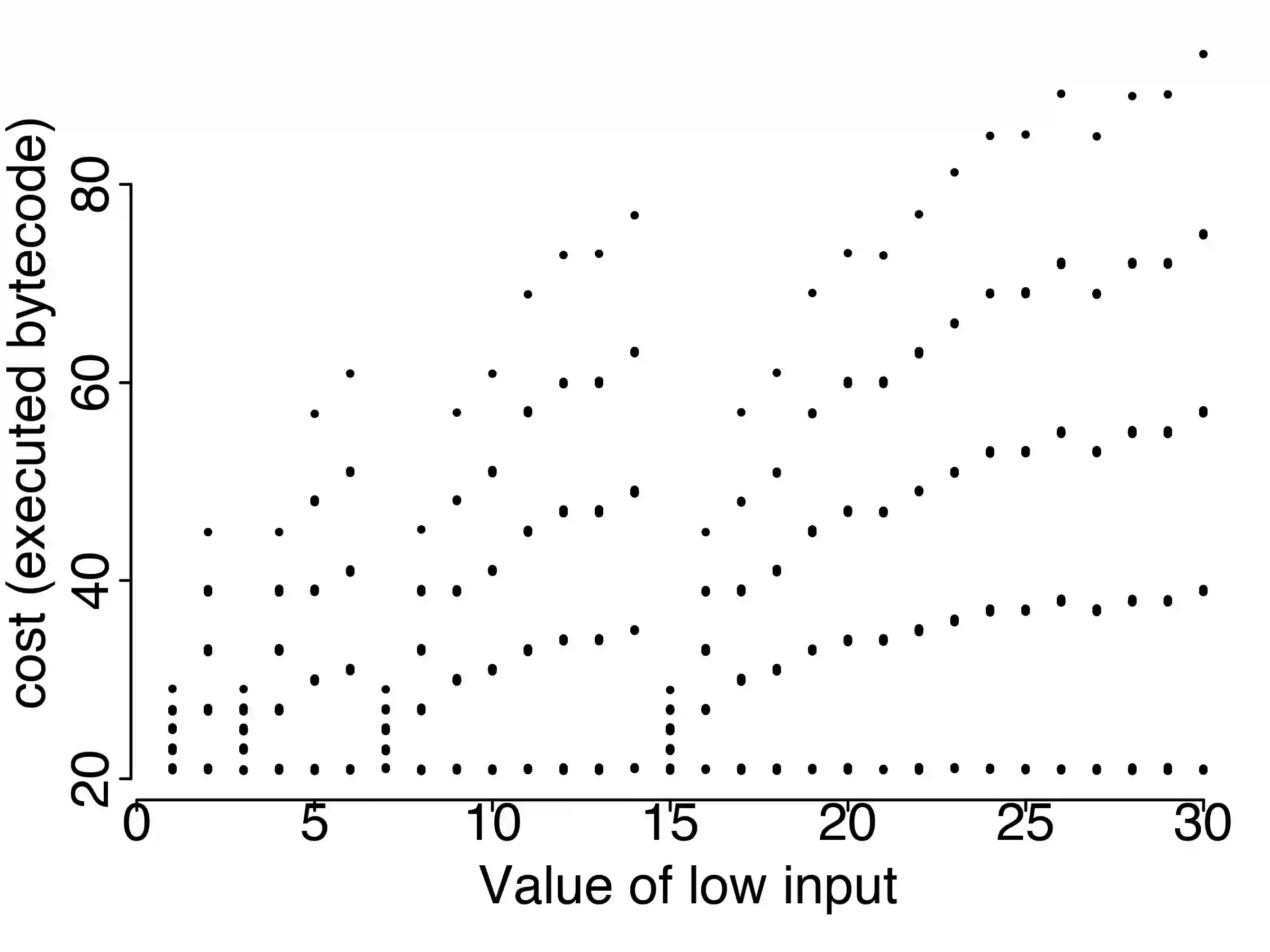
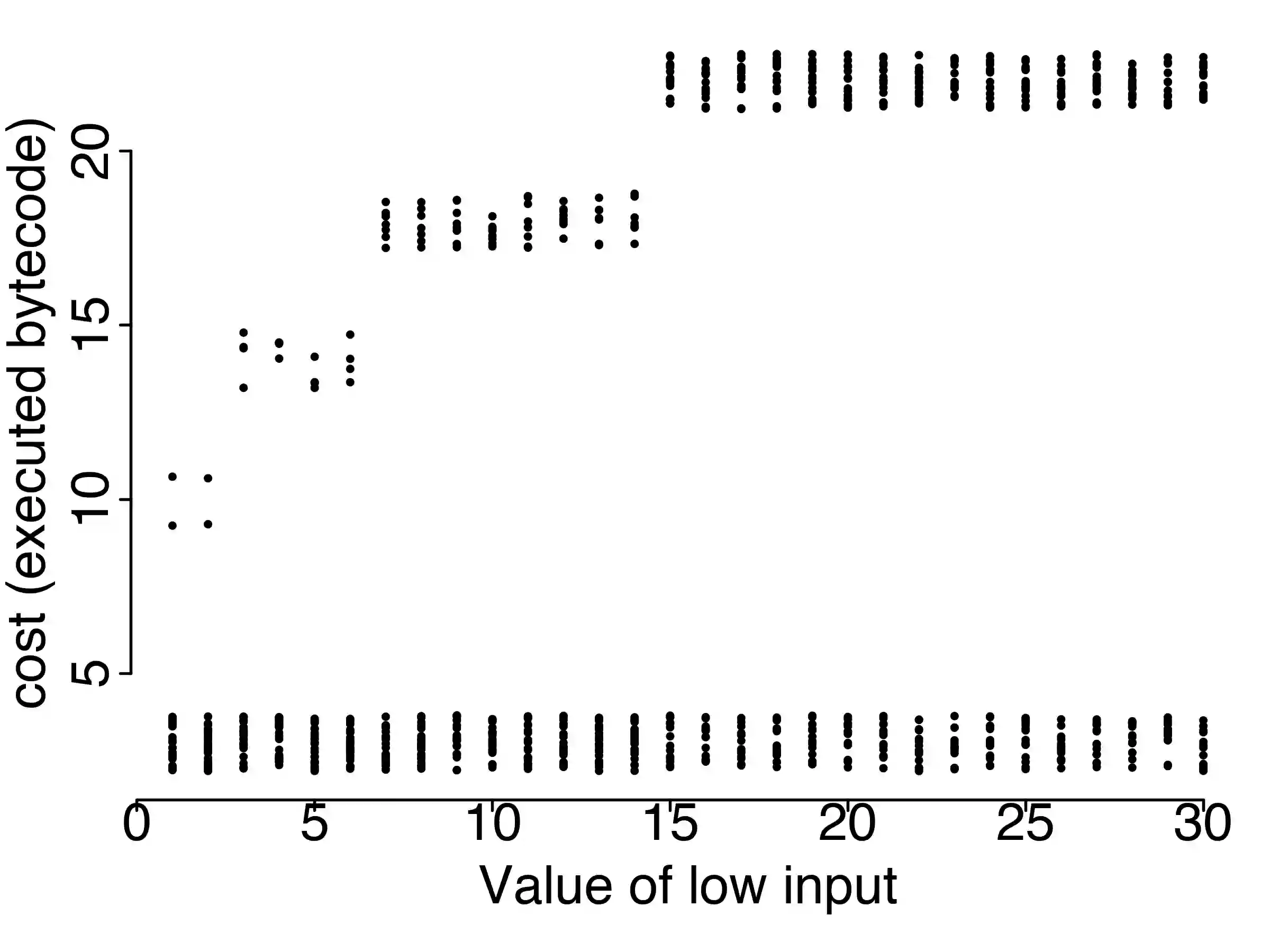
Information leaks through side channels are a pervasive problem, even in security-critical applications. Functional side channels arise when an attacker knows that a secret value of a server stays fixed for a certain time. Then, the attacker can observe the server executions on a sequence of different public inputs, each paired with the same secret input. Thus for each secret, the attacker observes a function from public inputs to execution time, for instance, and she can compare these functions for different secrets. First, we introduce a notion of noninterference for functional side channels. We focus on the case of noisy observations, where we demonstrate with examples that there is a practical functional side channel in programs that would be deemed information-leak-free or be underestimated using the standard definition. Second, we develop a framework and techniques for debugging programs for functional side channels. We extend evolutionary fuzzing techniques to generate inputs that exploit functional dependencies of response times on public inputs. We adapt existing results and algorithms in functional data analysis to model the functions and discover the existence of side channels. We use a functional extension of standard decision tree learning to pinpoint the code fragments causing a side channel if there is one. We empirically evaluate the performance of our tool FUCHSIA on a series of micro-benchmarks and realistic Java programs. On the set of benchmarks, we show that FUCHSIA outperforms the state-of-the-art techniques in detecting side channel classes. On the realistic programs, we show the scalability of FUCHSIA in analyzing functional side channels in Java programs with thousands of methods. Also, we show the usefulness of FUCHSIA in finding side channels including a zero-day vulnerability in OpenJDK and another vulnerability in Jetty that was since fixed by the developers.
翻译:通过侧渠道泄露信息是一个普遍的问题,即使是在安全关键应用程序中也是如此。 当攻击者知道服务器的秘密价值在一定时间内固定下来时, 功能侧渠道就会出现。 然后, 攻击者可以在不同的公共投入序列上观察服务器的处决, 每个输入都配有相同的秘密输入。 因此, 对于每一个秘密, 攻击者都会看到从公共投入到执行时间的功能, 比如说, 攻击者可以将这些功能从公共投入到执行时间的函数比较为不同的秘密。 首先, 我们引入了一个不干预功能侧渠道的概念。 我们集中关注一个吵闹的观测案例, 我们用实例来证明在程序中有实用的功能侧端端渠道, 这个程序将被视为无功能端渠道或被低估。 其次, 我们开发了一个框架和技术来解密程序。 我们推广了进化的模糊技术, 利用对公众投入的响应时间的功能依赖时间来生成投入。 我们调整了功能性数据分析中的现有结果和算法, 模拟功能侧端渠道的存在。 我们使用标准决定树的扩展功能, 来定位侧端端端端的侧端端渠道, 导致侧端端渠道的代码断断断断, 导致边端渠道的侧渠道的软弱点, 如果在运行轨道上显示一个常规程序, 我们的路径, 将显示了直路, 显示了我们的一个边端点,, 直路, 直路。