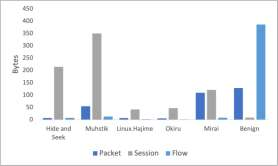
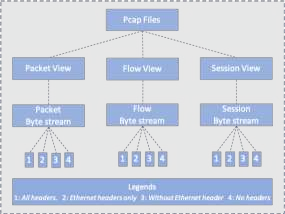
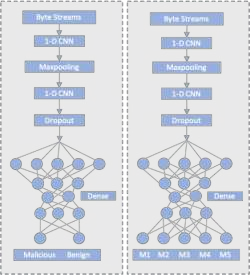
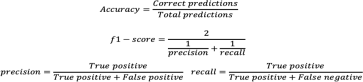
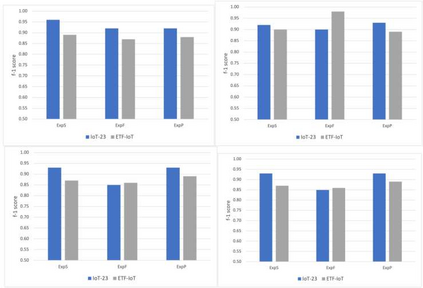
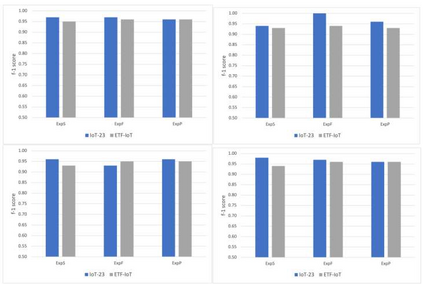
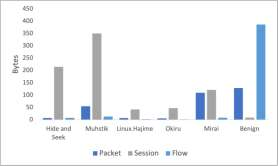
Through the generalization of deep learning, the research community has addressed critical challenges in the network security domain, like malware identification and anomaly detection. However, they have yet to discuss deploying them on Internet of Things (IoT) devices for day-to-day operations. IoT devices are often limited in memory and processing power, rendering the compute-intensive deep learning environment unusable. This research proposes a way to overcome this barrier by bypassing feature engineering in the deep learning pipeline and using raw packet data as input. We introduce a feature engineering-less machine learning (ML) process to perform malware detection on IoT devices. Our proposed model, "Feature engineering-less-ML (FEL-ML)," is a lighter-weight detection algorithm that expends no extra computations on "engineered" features. It effectively accelerates the low-powered IoT edge. It is trained on unprocessed byte-streams of packets. Aside from providing better results, it is quicker than traditional feature-based methods. FEL-ML facilitates resource-sensitive network traffic security with the added benefit of eliminating the significant investment by subject matter experts in feature engineering.
翻译:通过普及深层学习,研究界应对了网络安全领域的重大挑战,如恶意软件识别和异常检测,然而,研究界尚未讨论在日常操作Times(IoT)装置的互联网上部署这些装置的问题。 IoT装置的记忆和处理能力往往有限,使得计算密集的深层学习环境无法使用。这项研究提出了克服这一障碍的方法,在深层学习管道中绕过特征工程和使用原始包数据作为投入。我们引入了一个无特征工程设备学习(ML)程序,以对IoT装置进行恶意软件检测。我们提议的模型“Fatural工程-Nel-ML(FEL-ML)”是一种较轻的检测算法,在“工程设计”特性上不增加任何额外的计算。它有效地加快了低功率IoT边缘。它接受未经处理的包流技术培训。除了提供更好的结果之外,它比传统的基于特征的方法更快。FEL-ML便利对资源敏感的网络交通安全,并增加了消除专题专家对地貌工程进行重大投资的好处。