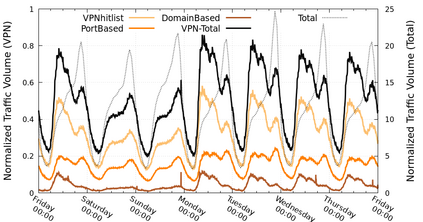
With the shift to working remotely after the COVID-19 pandemic, the use of Virtual Private Networks (VPNs) around the world has nearly doubled. Therefore, measuring the traffic and security aspects of the VPN ecosystem is more important now than ever. It is, however, challenging to detect and characterize VPN traffic since some VPN protocols use the same port number as web traffic and port-based traffic classification will not help. VPN users are also concerned about the vulnerabilities of their VPN connections due to privacy issues. In this paper, we aim at detecting and characterizing VPN servers in the wild, which facilitates detecting the VPN traffic. To this end, we perform Internet-wide active measurements to find VPN servers in the wild, and characterize them based on their vulnerabilities, certificates, locations, and fingerprinting. We find 9.8M VPN servers distributed around the world using OpenVPN, SSTP, PPTP, and IPsec, and analyze their vulnerability. We find SSTP to be the most vulnerable protocol with more than 90% of detected servers being vulnerable to TLS downgrade attacks. Of all the servers that respond to our VPN probes, 2% also respond to HTTP probes and therefore are classified as Web servers. We apply our list of VPN servers to the traffic from a large European ISP and observe that 2.6% of all traffic is related to these VPN servers.
翻译:随着在COVID-19大流行之后转向远程工作,全世界虚拟私人网络的使用几乎翻了一番,因此,测量VPN生态系统的交通和安全方面现在比以往任何时候更加重要,但检测和定性VPN交通是困难的,因为一些VPN协议使用与网络交通和港口交通分类相同的港口号码是没有帮助的。VPN用户还担心其VPN连接因隐私问题而变得脆弱。在本文中,我们的目标是探测和描述野生VPN服务器,这有利于检测VPN的交通。为此,我们进行全因特网范围的主动测量,以在野生找到VPN服务器,并根据这些服务器的脆弱性、证书、地点和指纹来描述它们的特点。我们发现,使用OpenVPN、SSTP、PPTP和IPsec在全世界分布的9.8M VPN服务器号码。我们发现SSTP是最脆弱的协议,90%以上的已检测到的服务器易受TLS下级袭击的。我们所有服务器都对VPN服务器做出响应的所有服务器。我们VPNPN服务器的流量清单中,因此,我们对这些VPPPPT服务器的大型服务器应用了2 %的互联网服务器。