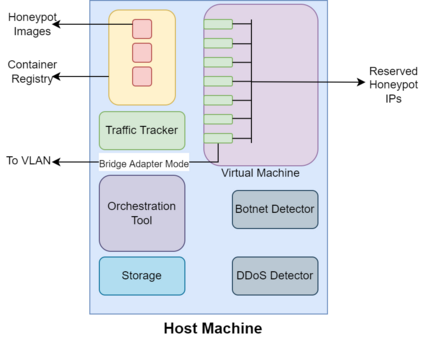
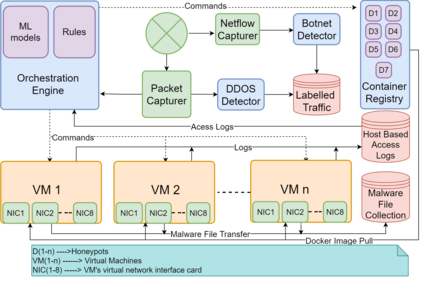
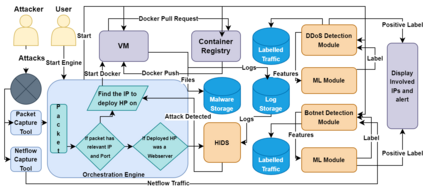
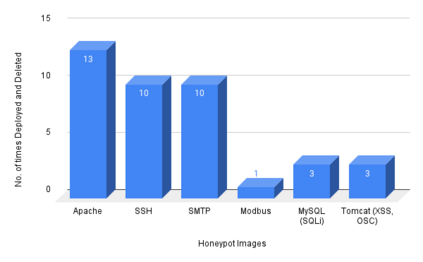
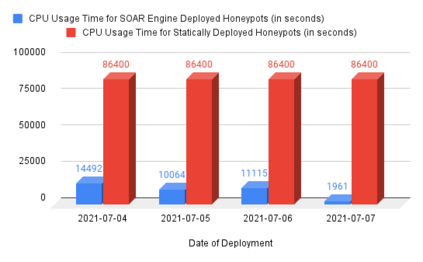
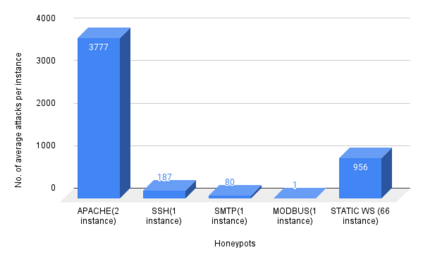
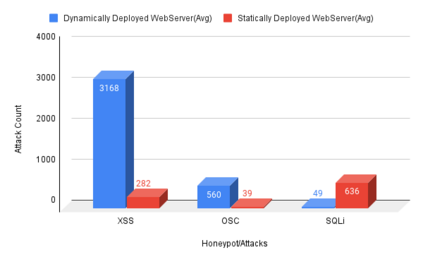
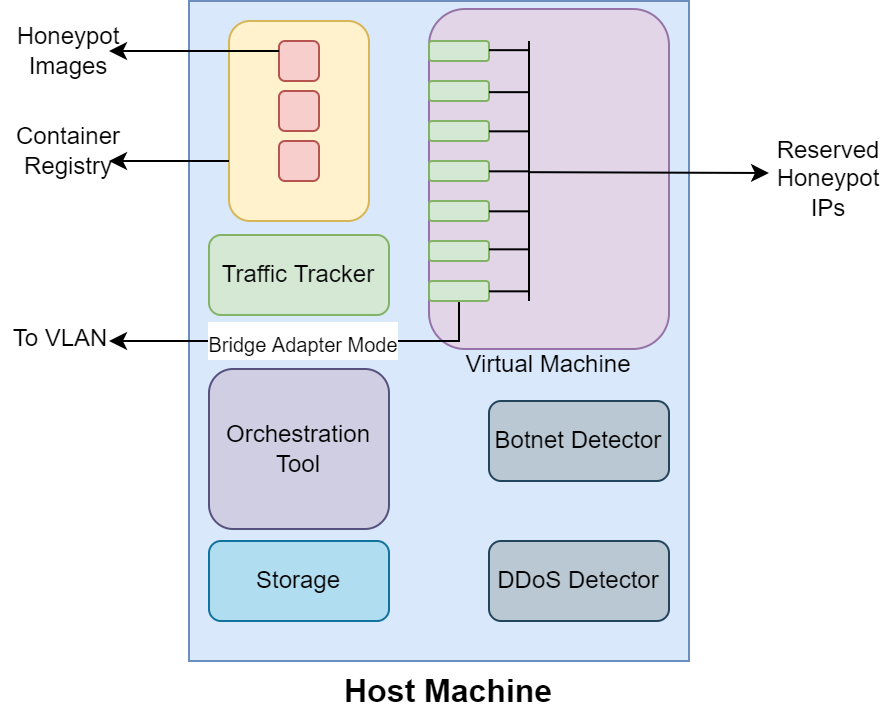
Cyber Security is a critical topic for organizations with IT/OT networks as they are always susceptible to attack, whether insider or outsider. Since the cyber landscape is an ever-evolving scenario, one must keep upgrading its security systems to enhance the security of the infrastructure. Tools like Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), Threat Intelligence Platform (TIP), Information Technology Service Management (ITSM), along with other defensive techniques like Intrusion Detection System (IDS), Intrusion Protection System (IPS), and many others enhance the cyber security posture of the infrastructure. However, the proposed protection mechanisms have their limitations, they are insufficient to ensure security, and the attacker penetrates the network. Deception technology, along with Honeypots, provides a false sense of vulnerability in the target systems to the attackers. The attacker deceived reveals threat intel about their modus operandi. We have developed a Security Orchestration, Automation, and Response (SOAR) Engine that dynamically deploys custom honeypots inside the internal network infrastructure based on the attacker's behavior. The architecture is robust enough to support multiple VLANs connected to the system and used for orchestration. The presence of botnet traffic and DDOS attacks on the honeypots in the network is detected, along with a malware collection system. After being exposed to live traffic for four days, our engine dynamically orchestrated the honeypots 40 times, detected 7823 attacks, 965 DDOS attack packets, and three malicious samples. While our experiments with static honeypots show an average attacker engagement time of 102 seconds per instance, our SOAR Engine-based dynamic honeypots engage attackers on average 3148 seconds.
翻译:对于拥有IT/OT网络的组织来说,网络安全是一个重要的主题,因为它们总是容易受到攻击,无论是内部还是外部。由于网络景观是一个不断演化的情景,我们必须不断更新其安全系统,以加强基础设施的安全。安全信息和事件管理、端点探测和反应、威胁情报平台、信息技术服务管理等工具,以及入侵探测系统、入侵保护系统等其他防御技术,以及许多其他技术,它们总是容易受到攻击。然而,拟议的保护机制有其局限性,不足以确保安全,攻击者渗透到网络中。安全信息和事件管理、端点探测和反应(EDD)、威胁情报平台、信息技术服务管理(ITM)以及其他防御技术,如入侵探测系统、入侵保护系统、入侵保护系统和其他许多技术,它们都会加强基础设施的网络安全态势。然而,拟议的保护机制有其局限性,不足以确保安全,而攻击者也不足以确保安全,攻击者渗透到网络中的安全系统中。 攻击系统中已经使用了多盘点的SOD网络, 系统中已经使用了多盘运行的服务器服务器, 运行系统中已经足够坚固地使用了多时间 。