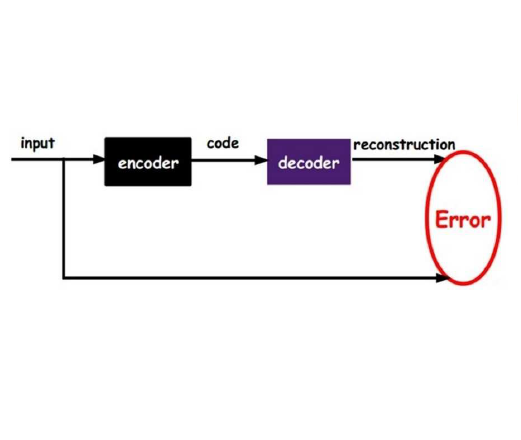
The rapidly increasing number of smart devices on the Internet necessitates an efficient inspection system for safeguarding our networks from suspicious activities such as Address Resolution Protocol (ARP) probes. In this research, we analyze sequence data of ARP traffic on LAN based on the numerical count and degree of its packets. Moreover, a dynamic threshold is employed to detect underlying suspicious activities, which are further converted into feature vectors to train an unsupervised autoencoder neural network. Then, we leverage K-means clustering to separate the extracted latent features of suspicious activities from the autoencoder into various patterns. Besides, to evaluate the performance, we collect and adopt a real-world network traffic dataset from five different LANs. At last, we successfully detect suspicious ARP patterns varying in scale, lifespan, and regularity on the LANs.
翻译:互联网上的智能装置数量迅速增加,这就需要一个高效的检查系统来保护我们的网络不受可疑活动的影响,例如地址解析协议(ARP)探测器;在这项研究中,我们根据数据数数和数据包的大小,分析局域网内ARP通信量的序列数据;此外,还使用动态阈值来查明潜在的可疑活动,这些可疑活动进一步转化为特性矢量,以训练一个不受监督的自动读数神经网络;然后,我们利用K手段集成,将可疑活动的隐含特征从自动解码器中分离出来,分为不同的模式;此外,我们从五个不同的局域网收集并采用真实世界网络通信数据集,最后,我们成功地检测了在规模、寿命和正常性方面各不相同的可疑的ARP模式。