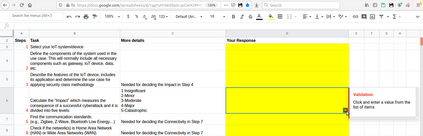
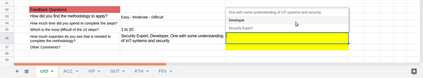
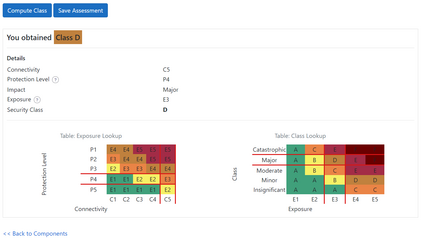
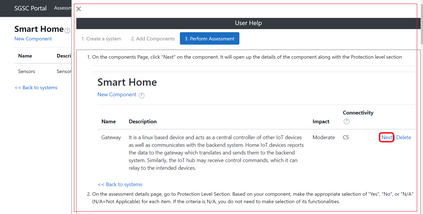
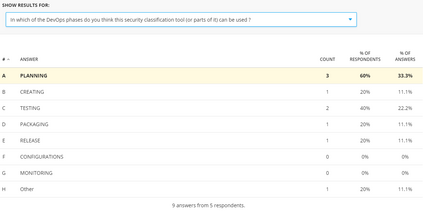
DevSecOps, as the extension of DevOps with security training and tools, has become a popular way of developing modern software, especially in the Internet of Things arena, due to its focus on rapid development, with short release cycles, involving the user/client very closely. Security classification methods, on the other hand, are heavy and slow processes that require high expertise in security, the same as in other similar areas such as risk analysis or certification. As such, security classification methods are hardly compatible with the DevSecOps culture, which to the contrary, has moved away from the traditional style of penetration testing done only when the software product is in the final stages or already deployed. In this work, we first propose five principles for a security classification to be \emph{DevOps-ready}, two of which will be the focus for the rest of the paper, namely to be tool-based and easy to use for non-security experts, such as ordinary developers or system architects. We then exemplify how one can make a security classification methodology DevOps-ready. We do this through an interaction design process, where we create and evaluate the usability of a tool implementing the chosen methodology. Since such work seems to be new within the usable security community, and even more so in the software development (DevOps) community, we extract from our process a general, three-steps `recipe' that others can follow when making their own security methodologies DevOps-ready. The tool that we build is in itself a contribution of this process, as it can be independently used, extended, and/or integrated by developer teams into their DevSecOps tool-chains. Our tool is perceived (by the test subjects) as most useful in the design phase, but also during the testing phase where the security class would be one of the metrics used to evaluate the quality of their software.
翻译:暂无翻译