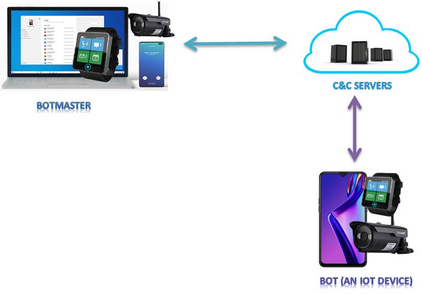
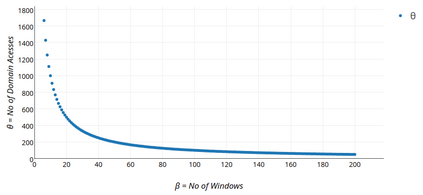
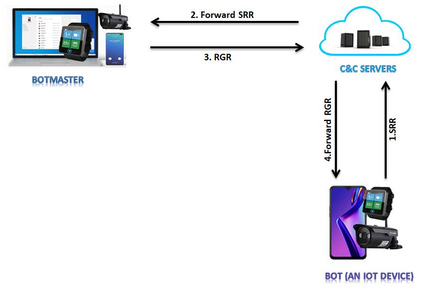
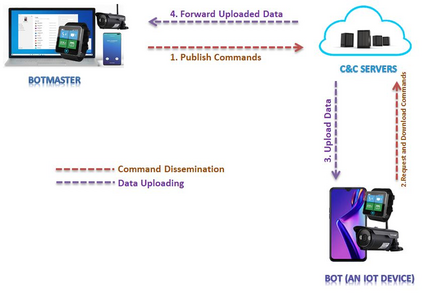
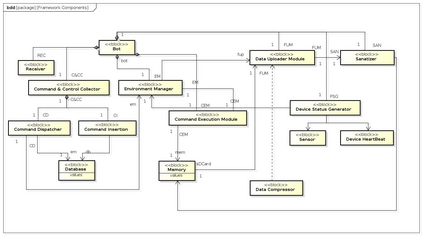
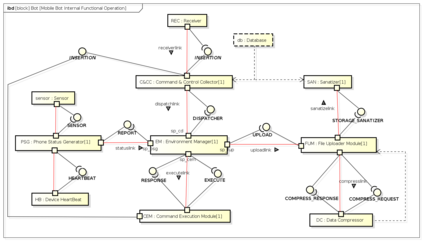
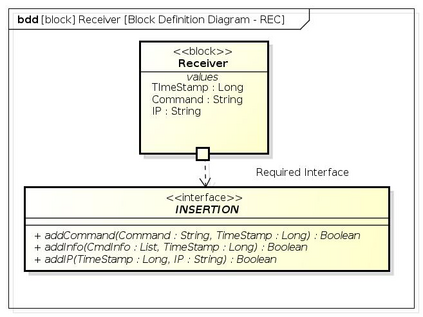
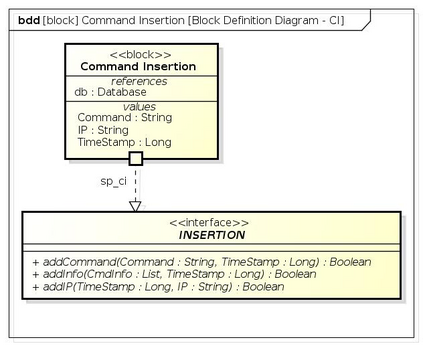
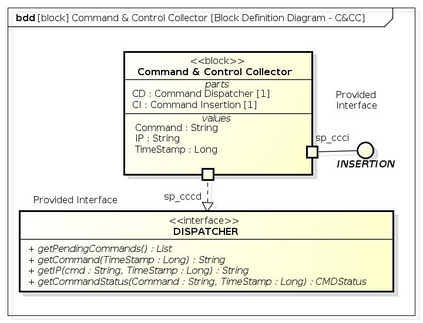
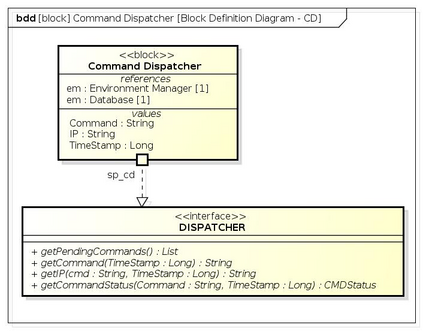
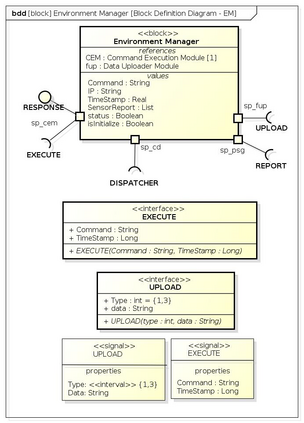
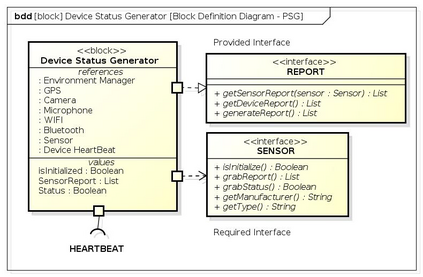
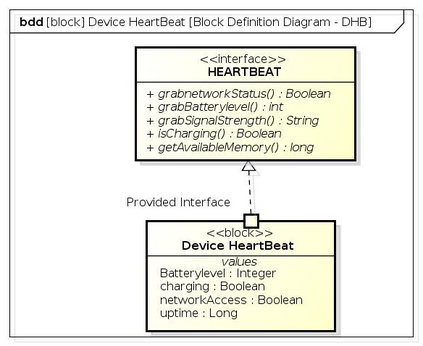
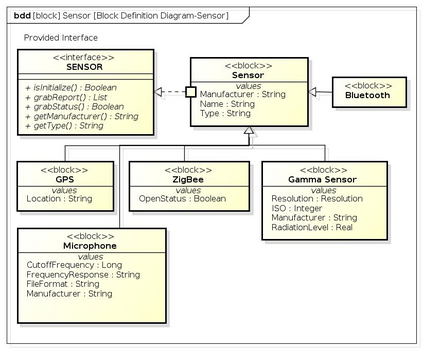
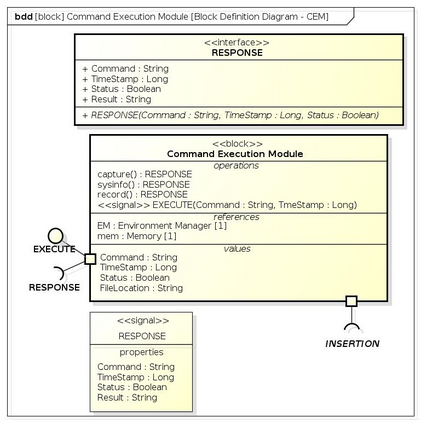
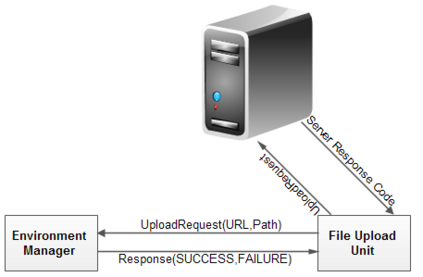
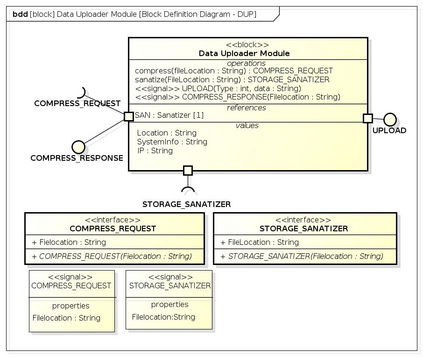
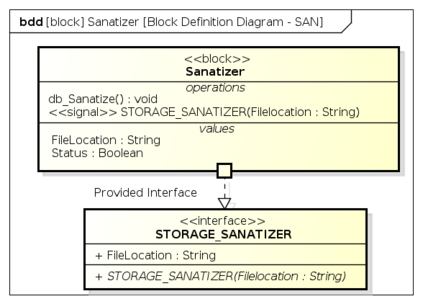
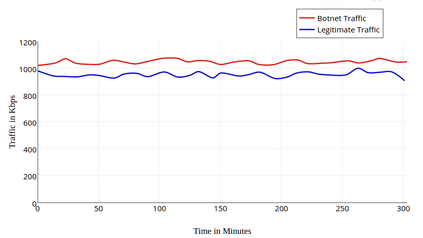
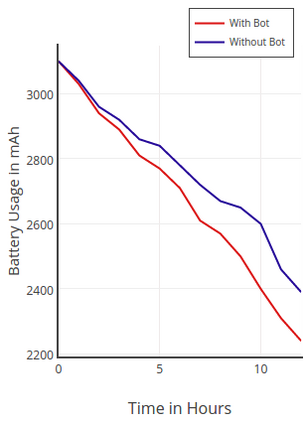
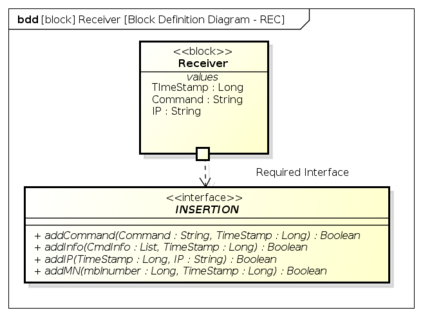
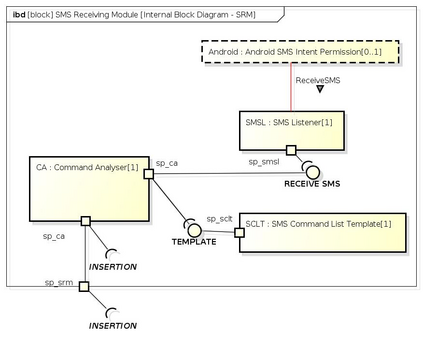
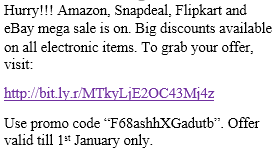
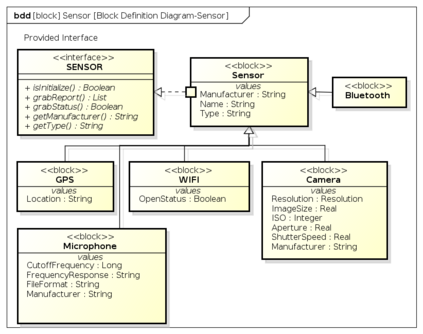
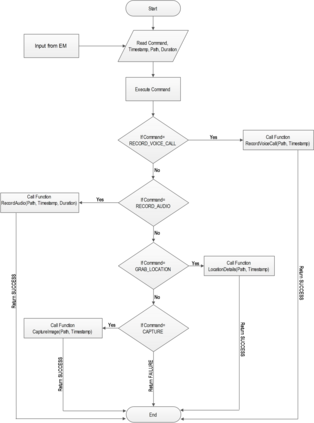
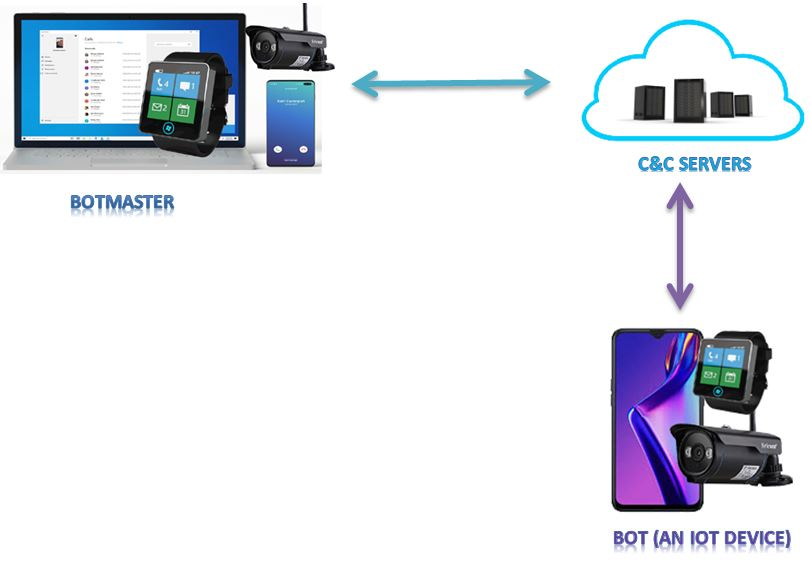
Botnets have become a serious security threat not only to the Internet but also to the devices connected to it. Factors like the exponential growth of IoT, the COVID-19 pandemic that's sweeping the planet, and the ever-larger number of cyber-criminals who now have access to or have developed increasingly more sophisticated tools are incentivizing the growth of botnets in this domain. The recent outbreak of botnets like Dark Nexus (derived from Qbot and Mirai), Mukashi, LeetHozer, Hoaxcalls, etc. shows the alarming rate at which this threat is converging. The botnets have attributes that make them an excellent platform for malicious activities in IoT devices. These IoT devices are used by organizations that need to both innovate and safeguard the personal and confidential data of their customers, employees, and business partners. The IoT devices have built-in sensors or actuators which can be exploited to monitor or control the physical environment of the entities connected to them thereby violating the fundamental concept of privacy-by-design of these devices. In this paper, we design and describe a modular botnet framework for IoT. Our framework is communication channel independent because it utilizes various available communication channels for command and control of an IoT device. The framework uses an enhanced centralized architecture associated with a novel Domain Fluxing Technique. The proposed framework will provide insights into how privacy in IoT devices can be incorporated at design time to check the sensors and actuators in these devices against malicious exploitation consequently preserving privacy. This paper includes design considerations, command and control structures, characteristics, capabilities, intrusion, and other related work. Furthermore, proof of concept Botnet is implemented and explained using the developed framework.
翻译:网络网络不仅对互联网,而且对与之相连的装置也构成了严重的安全威胁。 诸如互联网的指数增长、正在席卷地球的COVID-19大流行以及越来越多的网络罪犯现在能够进入或已经开发了日益先进的工具,这些网络罪犯现在越来越多地进入或开发了更多的网络犯罪工具,激励了该领域的肉网增长。 Dark Nexus(来自Qbot和Mirai)、Mukashi、LeetHozer、HoaxCalls等网络最近爆发的肉网(来自Dark Nexus(来自Qbot和Mirai)、Meakshi、LeetHozer、Hoaxcalls等,都表明了这种威胁正在凝聚的惊人速度。 肉网的特性使得它们成为IOT设备恶意活动的极好平台。 在本文中,我们设计并描述一个强化的通信框架, 使用各种通信框架, 将这些传感器的传感器或操作器可以用来监测或控制与它们相关的实体的物理环境。