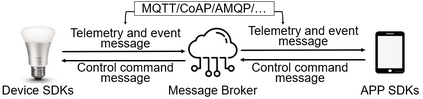
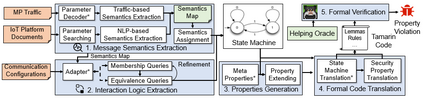
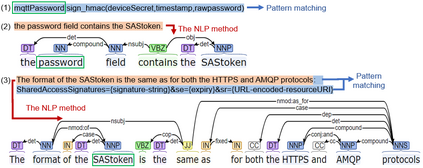
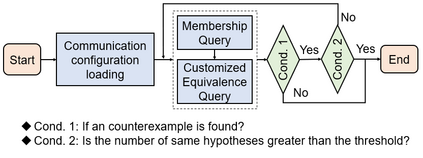
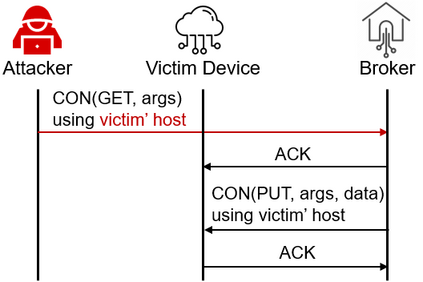
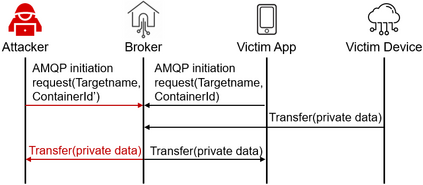
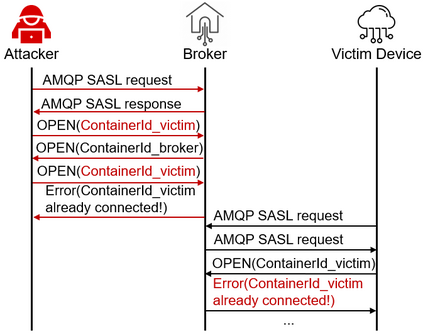
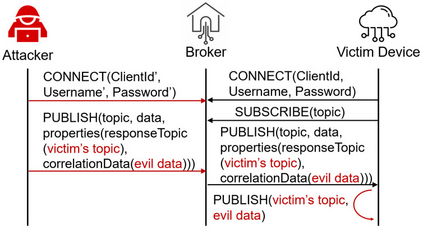
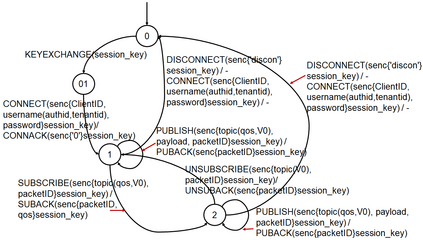
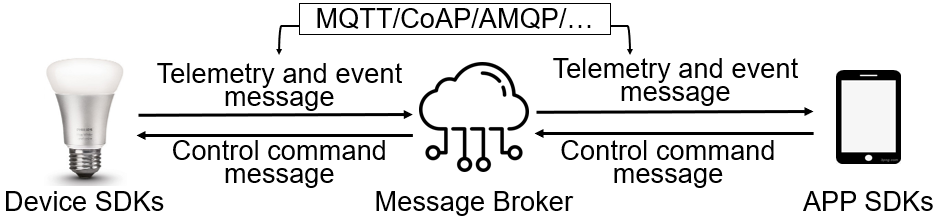
Facilitated by messaging protocols (MP), many home devices are connected to the Internet, bringing convenience and accessibility to customers. However, most deployed MPs on IoT platforms are fragmented and are not implemented carefully to support secure communication. To the best of our knowledge, there is no systematic solution to perform automatic security checks on MP implementations yet. To bridge the gap, we present MPInspector, the first automatic and systematic solution for vetting the security of MP implementations. MPInspector combines model learning with formal analysis and operates in three stages: (a) using parameter semantics extraction and interaction logic extraction to automatically infer the state machine of an MP implementation, (b) generating security properties based on meta properties and the state machine, and (c) applying automatic property based formal verification to identify property violations. We evaluate MPInspector on three popular MPs, including MQTT, CoAP and AMQP, implemented on nine leading IoT platforms. It identifies 252 property violations, leveraging which we further identify eleven types of attacks under two realistic attack scenarios. In addition, we demonstrate that MPInspector is lightweight (the average overhead of end-to-end analysis is ~4.5 hours) and effective with a precision of 100% in identifying property violations.
翻译:在信息传输协议(MP)的推动下,许多家用装置与互联网连接,给客户带来方便和方便;然而,在IoT平台上部署的大多数议员都是支离破碎的,而且没有谨慎地执行,以支持安全通信。据我们所知,尚没有系统的解决办法对执行MP进行自动安全检查。为了弥合这一差距,我们提出了MPInspecter,这是审查实施MP安全的第一个自动和系统的解决办法。MPInspecter将示范学习与正式分析结合起来,并分三个阶段运作:(a) 使用参数语义提取和互动逻辑提取,自动推断州立实施MP的机器;(b) 产生基于元属性和州立机器的安全属性;(c) 应用基于正式核查的自动财产来查明侵犯财产行为。我们评估了包括MQTT、CoAP和AMQP在内的三个受欢迎的MPP,这是在IoT九个主要平台上实施的首次自动和系统的自动和系统解决方案。它确定了252财产侵犯行为,我们进一步确定了两种现实攻击情景下的11类攻击行为。此外,我们证明MPInpector is limpress-impractal compractal apress-minal beqlightment axlight.