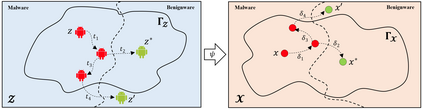
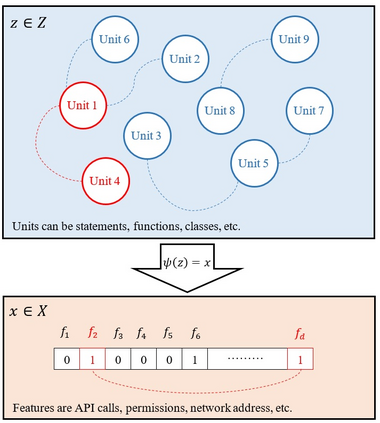
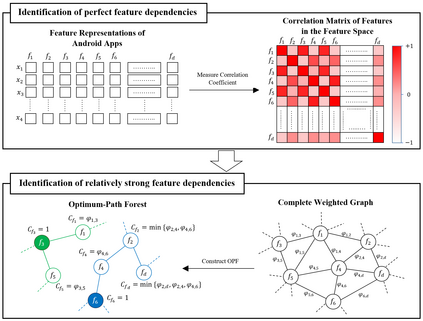
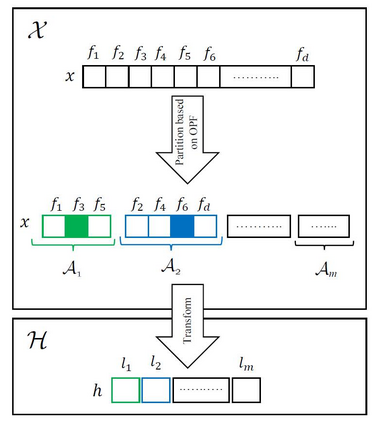
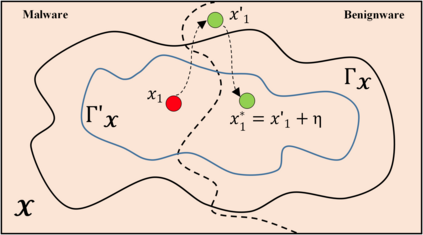
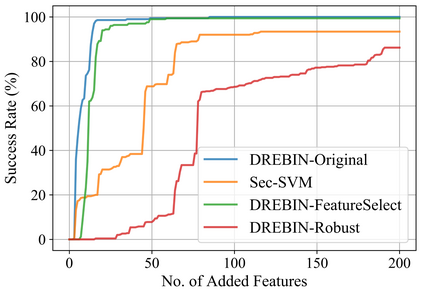
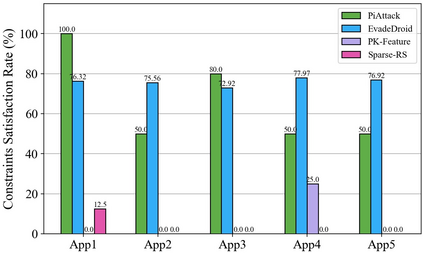
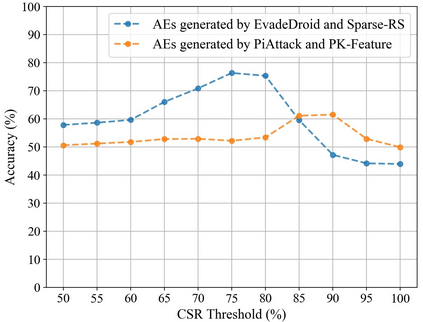
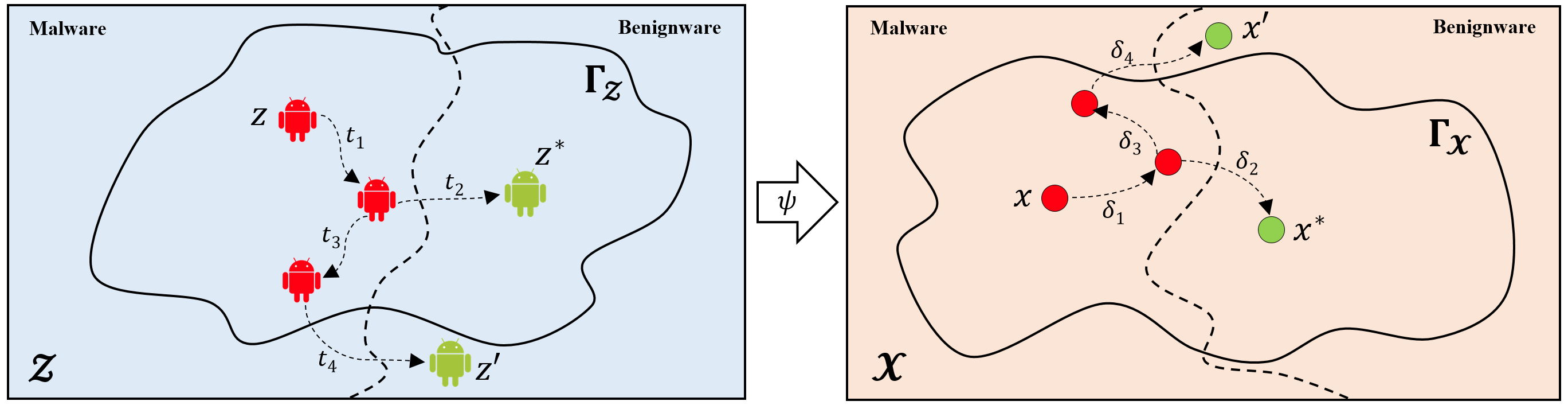
Strengthening the robustness of machine learning-based Android malware detectors in the real world requires incorporating realizable adversarial examples (RealAEs), i.e., AEs that satisfy the domain constraints of Android malware. However, existing work focuses on generating RealAEs in the problem space, which is known to be time-consuming and impractical for adversarial training. In this paper, we propose to generate RealAEs in the feature space, leading to a simpler and more efficient solution. Our approach is driven by a novel interpretation of Android malware properties in the feature space. More concretely, we extract feature-space domain constraints by learning meaningful feature dependencies from data and applying them by constructing a robust feature space. Our experiments on DREBIN, a well-known Android malware detector, demonstrate that our approach outperforms the state-of-the-art defense, Sec-SVM, against realistic gradient- and query-based attacks. Additionally, we demonstrate that generating feature-space RealAEs is faster than generating problem-space RealAEs, indicating its high applicability in adversarial training. We further validate the ability of our learned feature-space domain constraints in representing the Android malware properties by showing that (i) re-training detectors with our feature-space RealAEs largely improves model performance on similar problem-space RealAEs and (ii) using our feature-space domain constraints can help distinguish RealAEs from unrealizable AEs (unRealAEs).
翻译:在现实世界中,加强机器学习和机器人的恶意软件探测器的稳健性要求纳入可实现的对抗性实例(RealAEs),即满足安卓恶意软件领域限制的AEs,然而,现有工作的重点是在问题空间生成RealAEs,据知这对对抗性培训来说既费时又不切实际。在本文中,我们提议在特征空间生成RealAEs,从而导致一个更简单、更高效的解决方案。我们的方法是由对功能空间中的安卓恶意软件特性的新解释驱动的。更具体地说,我们通过从数据中学习有意义的特征依赖性能,并通过构建一个强大的特性空间软件空间来应用这些特性。我们关于问题空间的实验,众所周知,对于对抗性能探测器来说是费时且不切实际的。我们的方法超越了在功能空间上的状态防御性能,Sec-SVM,从而导致一种现实的梯度和以查询为基础的攻击。此外,我们证明生成地空空间ReAE的帮助性区分比产生问题要快得多,从不易产生问题空间ReAEs,表明其在空间领域限制中的高度适用性能性能。