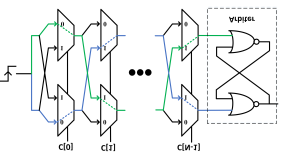
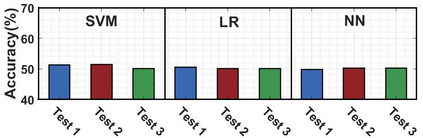
In most PUF-based authentication schemes, a central server is usually engaged to verify the response of the device's PUF to challenge bit-streams. However, the server availability may be intermittent in practice. To tackle such an issue, this paper proposes a new protocol for supporting distributed authentication while avoiding vulnerability to information leakage where CRPs could be retrieved from hacked devices and collectively used to model the PUF. The main idea is to provision for scrambling the challenge bit-stream in a way that is dependent on the verifier. The scrambling pattern varies per authentication round for each device and independently across devices. In essence, the scrambling function becomes node- and packet-specific and the response received by two verifiers of one device for the same challenge bit-stream could vary. Thus, neither the scrambling function can be reverted, nor the PUF can be modeled even by a collusive set of malicious nodes. The validation results using data of an FPGA-based implementation demonstrate the effectiveness of our approach in thwarting PUF modeling attacks by collusive actors. We also discuss the approach resiliency against impersonation, Sybil, and reverse engineering attacks.
翻译:在大多数基于PUF的认证方案中,通常使用一个中央服务器来核查设备PUF对挑战位流的反应,然而,服务器的可用性实际上可能时断时续。为了解决这样一个问题,本文件提议了一个新的协议,支持分散的认证,同时避免容易出现信息泄漏,因为从黑客设备中回收CRP,并共同用来模拟PUF。主要想法是提供一种取决于核查者的方式来冲淡挑战位流。每个设备每个设备每个认证回合的扭曲模式各不相同,而且各装置之间独立。实质上,滚动的功能变得节点和包包特,两个核查者对同一挑战流的一个设备的反应也可能有所不同。因此,无法恢复悬浮功能,即使通过串通的恶意节点组合也能模拟PUF。使用基于FPGA的执行数据来验证结果表明我们的方法在阻止腐蚀性行为者进行PUF模型攻击方面的有效性。我们还讨论反向性攻击的方法,我们讨论了反向性攻击的方法。