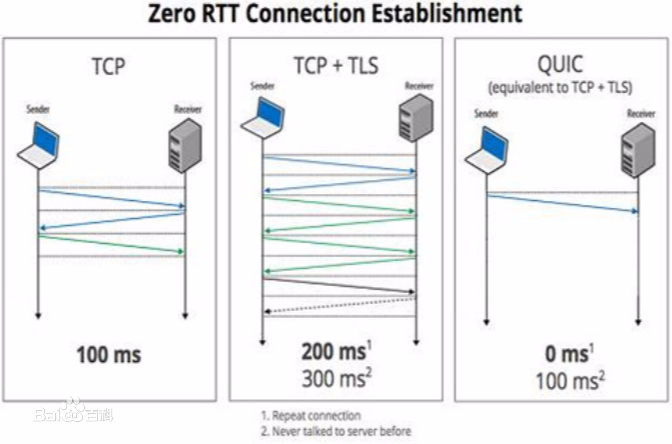
QUIC protocol is primarily designed to optimize web performance and security. However, previous research has pointed out that it is vulnerable to handshake flooding attacks. Attackers can send excessive volume of handshaking requests to exhaust the CPU resource of the server, through utilizing the large CPU amplification factor occurred during the handshake process under attack. In this paper, we introduce a novel defense mechanism by introducing the concept of crypto challenges into the handshake protocol. This enhancement involves a proposal of modifying the RETRY token to integrate a cryptographic challenge into it. The client must solve crypto challenges during the handshake process in order to receive a high priority on the server side. By properly choosing the difficulty level of the challenges, the CPU amplification can be reduced, thus the DDoS vulnerability is naturalized. We evaluated the effectiveness of our proposed solution by integrating the crypto challenges into the clients and server of \textit{aioquic}. Our experimental results demonstrate that our solution can effectively balance the resource usage between the attacker and the server during of handshake flooding attacks while maintaining a low overhead for legitimate clients.
翻译:暂无翻译