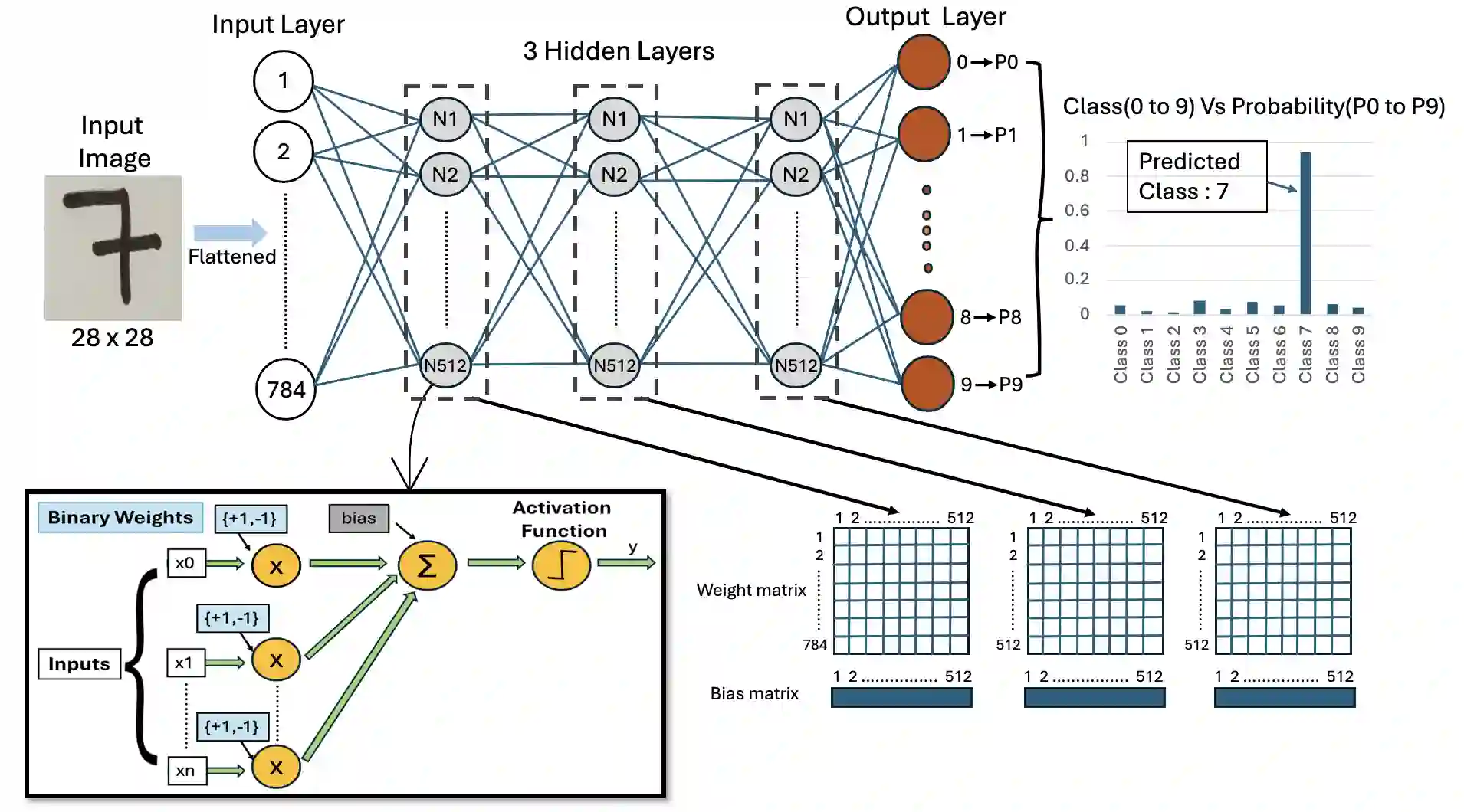
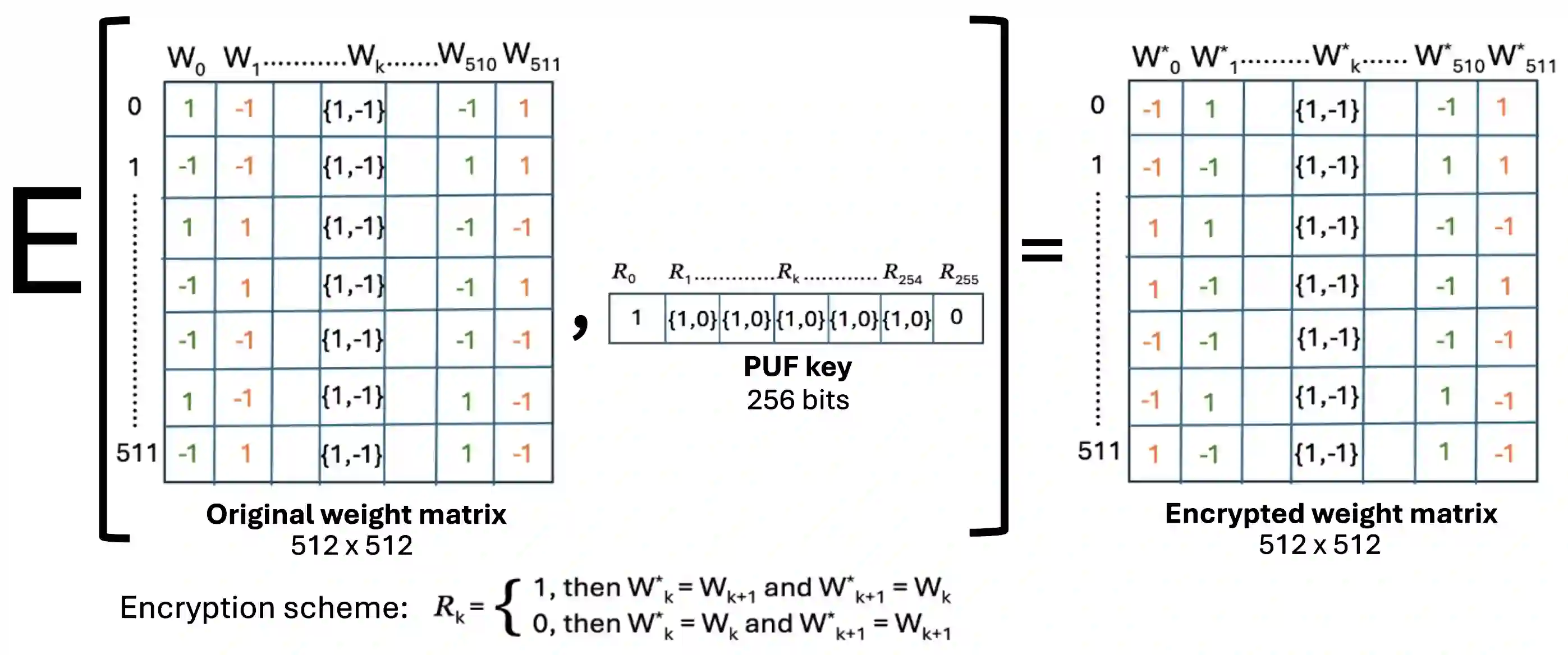
Binarized Neural Networks (BNNs) deployed on memristive crossbar arrays provide energy-efficient solutions for edge computing but are susceptible to physical attacks due to memristor nonvolatility. Recently, Rajendran et al. (IEEE Embedded Systems Letter 2025) proposed a Physical Unclonable Function (PUF)-based scheme to secure BNNs against theft attacks. Specifically, the weight and bias matrices of the BNN layers were secured by swapping columns based on device's PUF key bits. In this paper, we demonstrate that this scheme to secure BNNs is vulnerable to PUF-key recovery attack. As a consequence of our attack, we recover the secret weight and bias matrices of the BNN. Our approach is motivated by differential cryptanalysis and reconstructs the PUF key bit-by-bit by observing the change in model accuracy, and eventually recovering the BNN model parameters. Evaluated on a BNN trained on the MNIST dataset, our attack could recover 85% of the PUF key, and recover the BNN model up to 93% classification accuracy compared to the original model's 96% accuracy. Our attack is very efficient and it takes a couple of minutes to recovery the PUF key and the model parameters.
翻译:部署在忆阻交叉阵列上的二值化神经网络(BNNs)为边缘计算提供了高能效的解决方案,但由于忆阻器的非易失性,易受物理攻击。最近,Rajendran等人(IEEE Embedded Systems Letter 2025)提出了一种基于物理不可克隆函数(PUF)的方案,以保护BNNs免受窃取攻击。具体而言,该方案通过基于设备PUF密钥位交换列来保护BNN层的权重和偏置矩阵。本文中,我们证明该保护BNN的方案易受PUF密钥恢复攻击。通过我们的攻击,我们恢复了BNN的秘密权重和偏置矩阵。我们的方法受差分密码分析的启发,通过观察模型准确率的变化逐位重构PUF密钥,最终恢复BNN模型参数。在基于MNIST数据集训练的BNN上评估,我们的攻击能够恢复85%的PUF密钥,并恢复BNN模型至93%的分类准确率(原始模型准确率为96%)。我们的攻击效率极高,仅需数分钟即可恢复PUF密钥和模型参数。