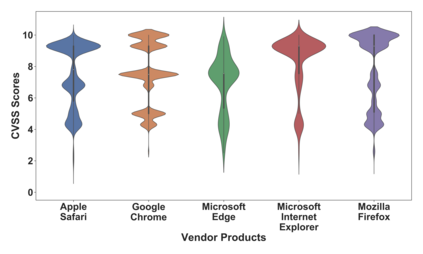
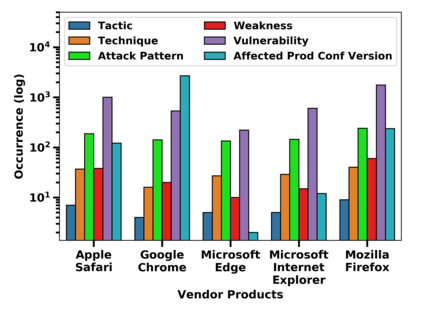
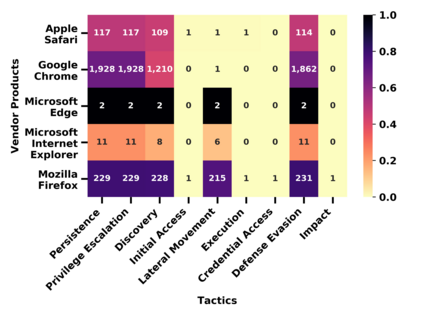
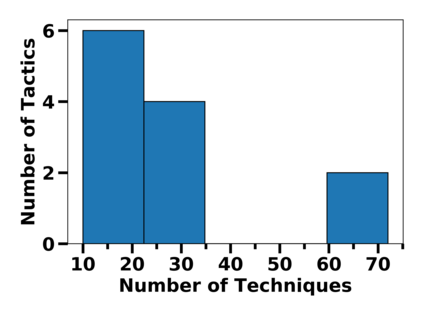
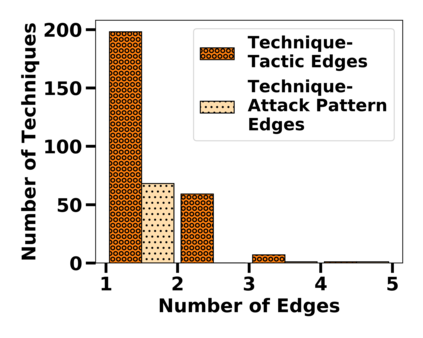
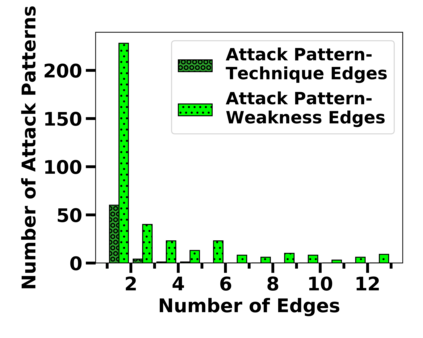
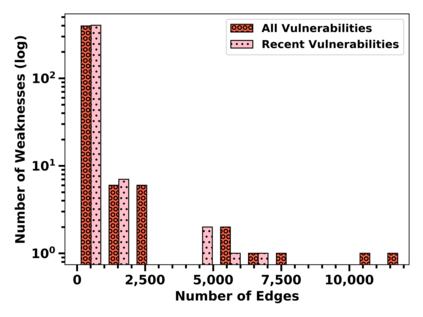
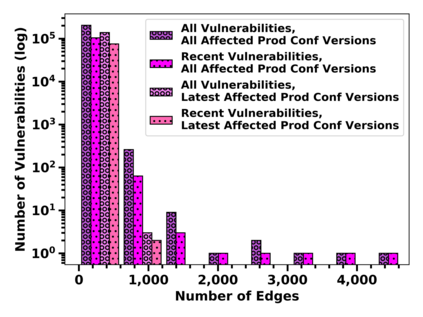
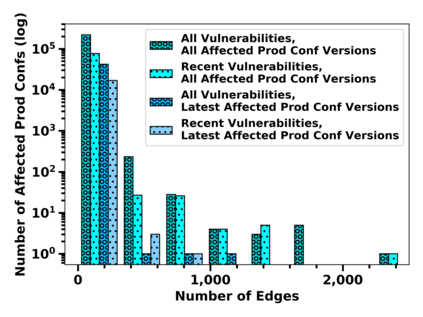
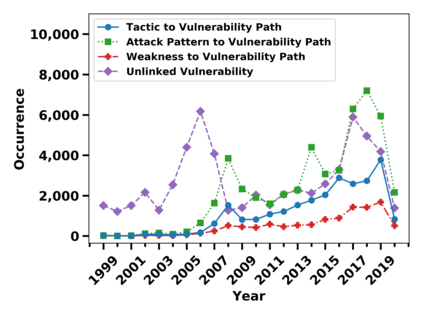
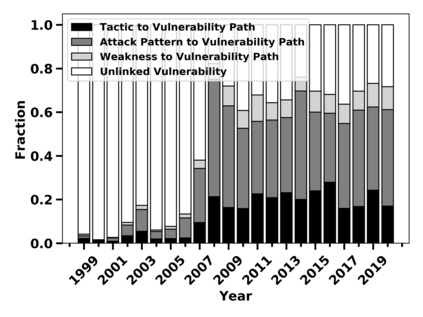
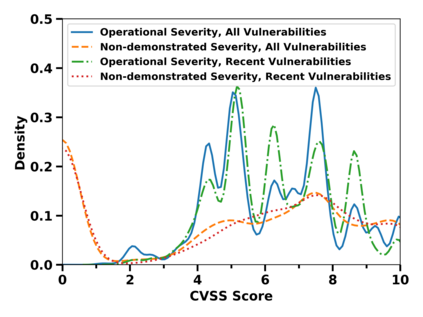
Many public sources of cyber threat and vulnerability information exist to help defend cyber systems. This paper links MITRE's ATT&CK MATRIX of Tactics and Techniques, NIST's Common Weakness Enumerations (CWE), Common Vulnerabilities and Exposures (CVE), and Common Attack Pattern Enumeration and Classification list (CAPEC), to gain further insight from alerts, threats and vulnerabilities. We preserve all entries and relations of the sources, while enabling bi-directional, relational path tracing within an aggregate data graph called BRON. In one example, we use BRON to enhance the information derived from a list of the top 10 most frequently exploited CVEs. We identify attack patterns, tactics, and techniques that exploit these CVEs and also uncover a disparity in how much linked information exists for each of these CVEs. This prompts us to further inventory BRON's collection of sources to provide a view of the extent and range of the coverage and blind spots of public data sources.
翻译:本文链接了麻省理工学院的战术和技术的ATT&CK MATRIX、NIST的常见弱点统计(CWE)、共同脆弱性和暴露(CVE)和共同攻击模式统计和分类清单(CAPEC),以便从警报、威胁和脆弱性中进一步了解有关网络威胁和脆弱性的信息。我们保存了所有来源的条目和关系,同时在称为BRON的汇总数据图中进行双向、关联路径追踪。举例来说,我们利用BRON加强从最经常被利用的十大关键变量清单中获取的信息。我们查明了利用这些关键变量的模式、战术和技术,并找出了这些关键变量中每个变量存在多少关联信息方面的差异。这促使我们进一步清查BRON收集的来源,以便了解公共数据来源的范围和范围。