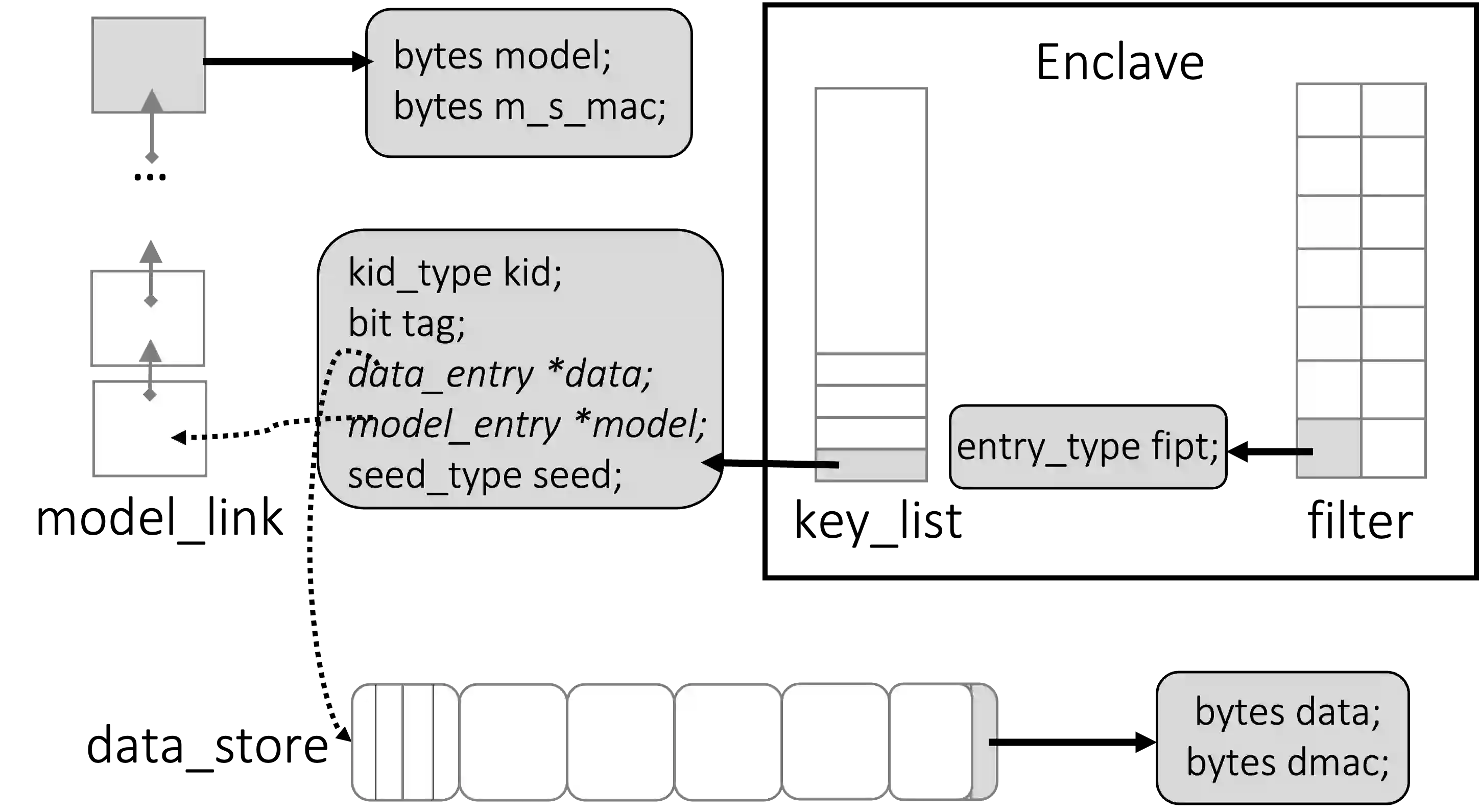
The "Right to be Forgotten" rule in machine learning (ML) practice enables some individual data to be deleted from a trained model, as pursued by recently developed machine unlearning techniques. To truly comply with the rule, a natural and necessary step is to verify if the individual data are indeed deleted after unlearning. Yet, previous parameter-space verification metrics may be easily evaded by a distrustful model trainer. Thus, Thudi et al. recently present a call to action on algorithm-level verification in USENIX Security'22. We respond to the call, by reconsidering the unlearning problem in the scenario of machine learning as a service (MLaaS), and proposing a new definition framework for Proof of Unlearning (PoUL) on algorithm level. Specifically, our PoUL definitions (i) enforce correctness properties on both the pre and post phases of unlearning, so as to prevent the state-of-the-art forging attacks; (ii) highlight proper practicality requirements of both the prover and verifier sides with minimal invasiveness to the off-the-shelf service pipeline and computational workloads. Under the definition framework, we subsequently present a trusted hardware-empowered instantiation using SGX enclave, by logically incorporating an authentication layer for tracing the data lineage with a proving layer for supporting the audit of learning. We customize authenticated data structures to support large out-of-enclave storage with simple operation logic, and meanwhile, enable proving complex unlearning logic with affordable memory footprints in the enclave. We finally validate the feasibility of the proposed instantiation with a proof-of-concept implementation and multi-dimensional performance evaluation.
翻译:机器学习(ML)实践中的“ 被遗忘的权利” 规则使得某些个人数据能够像最近开发的机器不学习技术所追求的那样,从经过训练的模式中删除。 为了真正遵守规则,自然和必要的步骤是核实个人数据是否在不学习之后确实被删除。然而,以前的参数-空间核查指标很容易被一个不信任的模型训练师所回避。 因此,Thudi等人最近呼吁在USENIX Security'22中就算法一级的核查采取行动。 我们响应了这一呼吁,重新考虑了机器学习作为一种服务(MLAAS)的假设中未学习的问题,并提出了在算法层面上证明不学习(POUL)的新定义框架。具体地说,我们的POUL定义(i)在不学习的前后阶段都能够执行正确的属性,从而防止攻击的老化状态;(ii) 以最起码的入侵性证据来突出证明和验证可承受成本的两边方的正确性要求,在不固定的服务管道和计算工作量中,在简单的逻辑定义框架内,我们最终用一个可信任的硬的系统化的存储系统数据库来验证, 将一个可追溯化的系统化的运行系统化的运行系统校正。