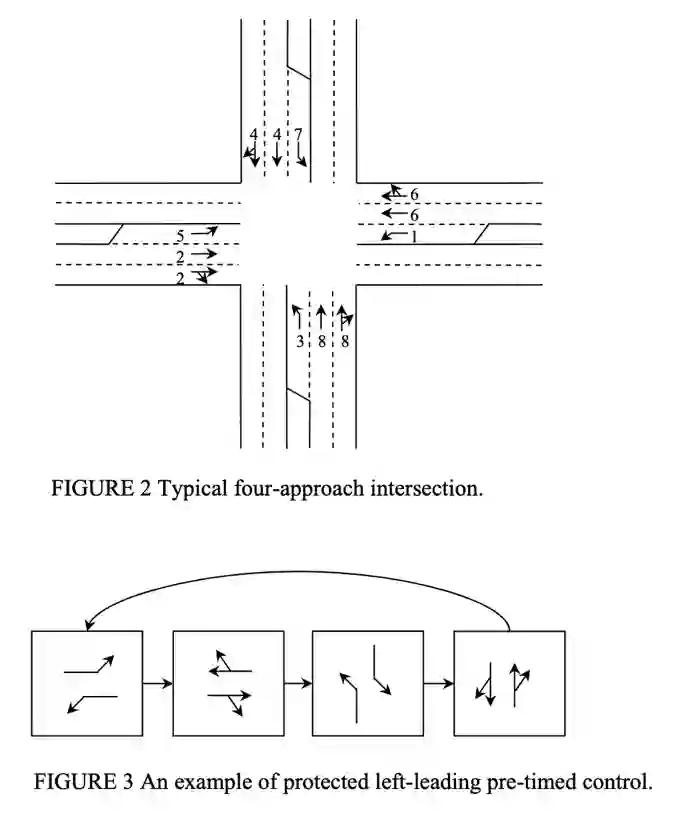
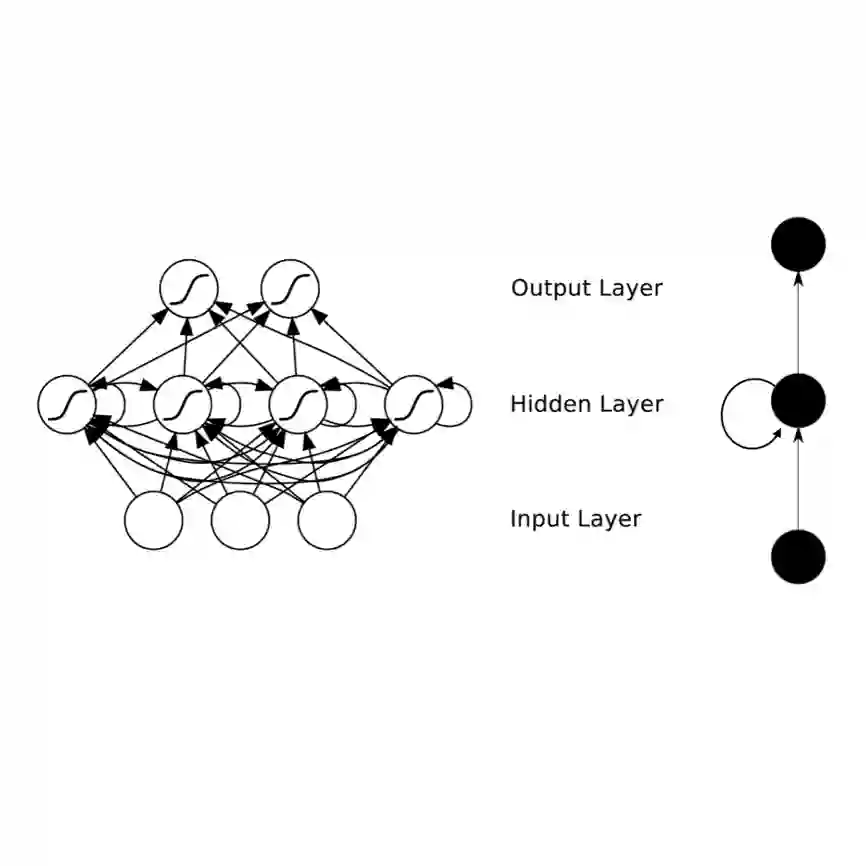
An adaptive traffic signal controller (ATSC) combined with a connected vehicle (CV) concept uses real-time vehicle trajectory data to regulate green time and has the ability to reduce intersection waiting time significantly and thereby improve travel time in a signalized corridor. However, the CV-based ATSC increases the size of the surface vulnerable to potential cyber-attack, allowing an attacker to generate disastrous traffic congestion in a roadway network. An attacker can congest a route by generating fake vehicles by maintaining traffic and car-following rules at a slow rate so that the signal timing and phase change without having any abrupt changes in number of vehicles. Because of the adaptive nature of ATSC, it is a challenge to model this kind of attack and also to develop a strategy for detection. This paper introduces an innovative "slow poisoning" cyberattack for a waiting time based ATSC algorithm and a corresponding detection strategy. Thus, the objectives of this paper are to: (i) develop a "slow poisoning" attack generation strategy for an ATSC, and (ii) develop a prediction-based "slow poisoning" attack detection strategy using a recurrent neural network -- i.e., long short-term memory model. We have generated a "slow poisoning" attack modeling strategy using a microscopic traffic simulator -- Simulation of Urban Mobility (SUMO) -- and used generated data from the simulation to develop both the attack model and detection model. Our analyses revealed that the attack strategy is effective in creating a congestion in an approach and detection strategy is able to flag the attack.
翻译:适应性交通信号控制器(ATSC)与连接车辆(CV)概念相结合,适应性交通信号控制器(ATSC)与连接车辆(CV)概念相结合,使用实时车辆轨迹数据调节绿色时间,从而能够大量减少交叉等候时间,从而在信号化走廊大大缩短旅行时间。然而,基于CV的STSC增加了可能受到潜在网络攻击的表面的“低中毒”网络攻击规模,使攻击者能够在公路网中造成灾难性交通堵塞。攻击者可以通过以缓慢的速度保持交通和汽车执行规则生成假车辆,从而利用信号性车辆数量的任何突变来控制车辆轨迹数据。由于ATSC具有适应性,因此它是一个挑战,要模拟这种攻击的模型和阶段变化不会发生任何突变。由于ATSC的适应性性质,它是一个挑战,要模拟这种攻击并同时制定探测战略。本文介绍了一种创新的“低中毒”网络攻击面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面,从而形成“低中毒”攻击攻击模型生成攻击生成模型生成模型生成式攻击战略。 (二)在SIM路面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面面上,使用一种快速探测战略 — — — — 快速探测战略 — — — 快速探测战略 — 快速路面面面面面面面面面面面面面面面面面面图路路路路路路面分析 — — — — — 快速路路路面分析 — — — — 快速路路路路路路路路路路路路路路面路路路路路路路面路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路路