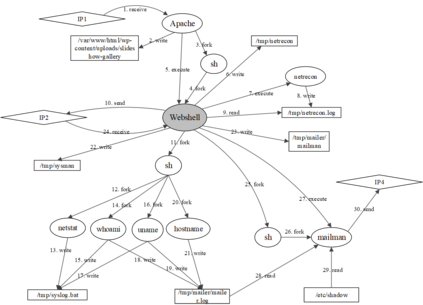
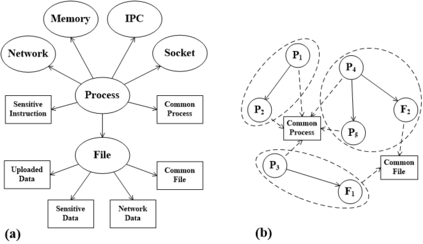
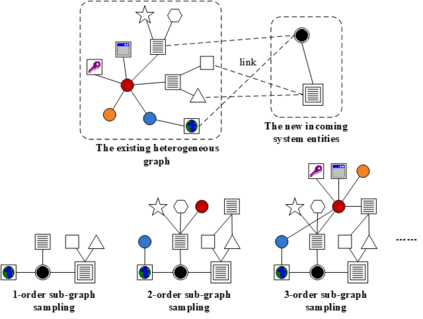
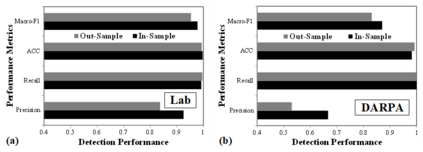
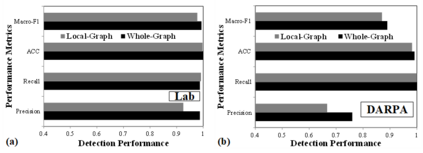
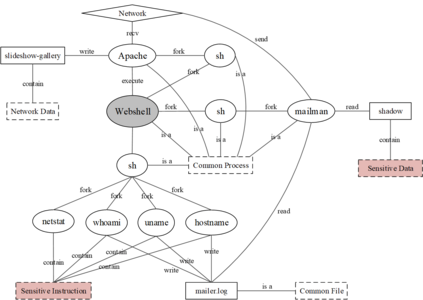
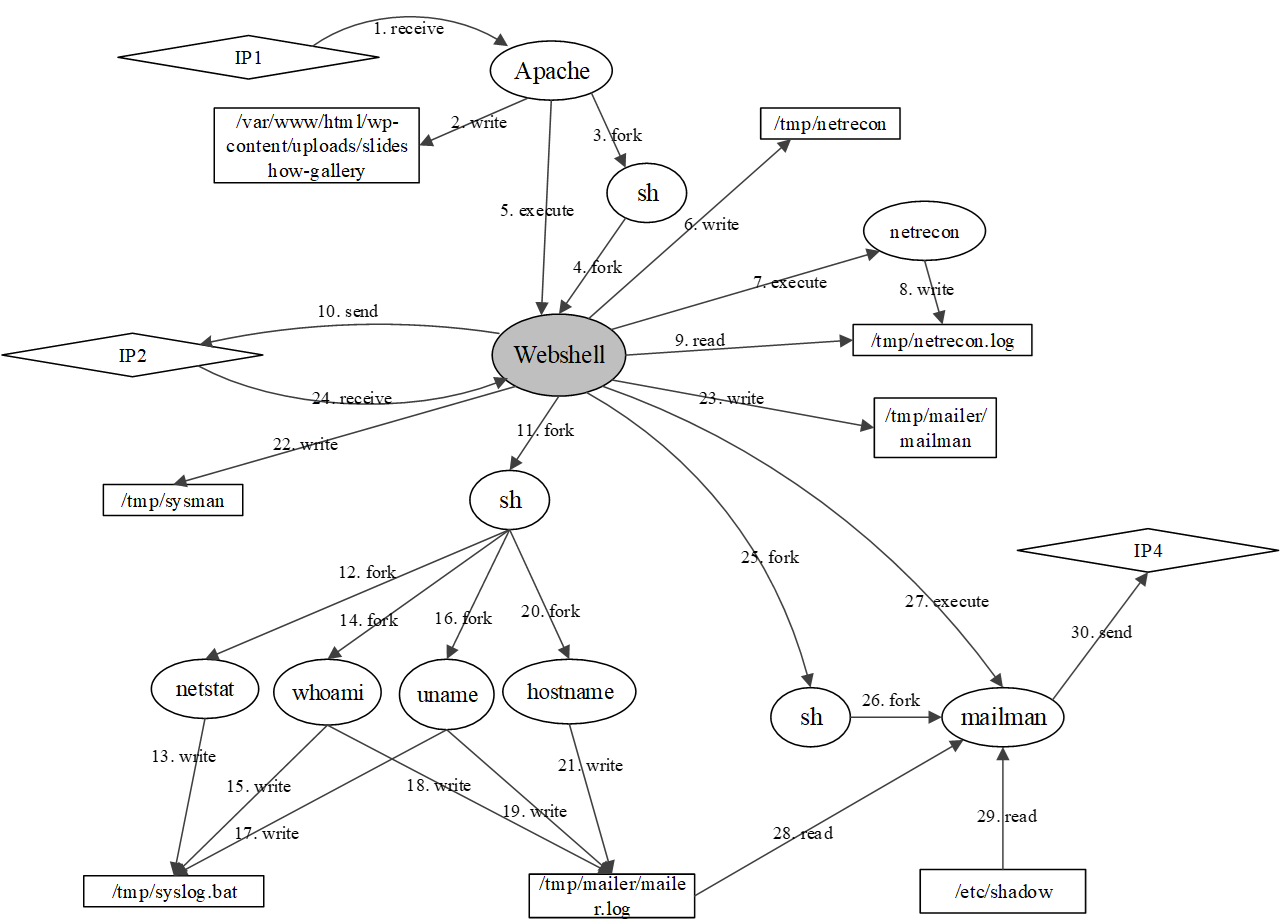
A cyber-attack is a malicious attempt by experienced hackers to breach the target information system. Usually, the cyber-attacks are characterized as hybrid TTPs (Tactics, Techniques, and Procedures) and long-term adversarial behaviors, making the traditional intrusion detection methods ineffective. Most existing cyber-attack detection systems are implemented based on manually designed rules by referring to domain knowledge (e.g., threat models, threat intelligences). However, this process is lack of intelligence and generalization ability. Aiming at this limitation, this paper proposes an intelligent cyber-attack detection method based on provenance data. To effective and efficient detect cyber-attacks from a huge number of system events in the provenance data, we firstly model the provenance data by a heterogeneous graph to capture the rich context information of each system entities (e.g., process, file, socket, etc.), and learns a semantic vector representation for each system entity. Then, we perform online cyber-attack detection by sampling a small and compact local graph from the heterogeneous graph, and classifying the key system entities as malicious or benign. We conducted a series of experiments on two provenance datasets with real cyber-attacks. The experiment results show that the proposed method outperforms other learning based detection models, and has competitive performance against state-of-the-art rule based cyber-attack detection systems.
翻译:网络攻击是有经验的黑客恶意地试图破坏目标信息系统的网络攻击。通常,网络攻击被定性为混合TTP(战术、技术和程序)和长期对抗行为,使传统的入侵探测方法无效。大多数现有的网络攻击探测系统是根据人工设计的规则,参照域知识(例如威胁模型、威胁情报等)实施的。然而,这一过程缺乏情报和概括性能力。为了达到这一限制,本文提议根据来源数据,采用智能网络攻击探测方法。为了切实有效地探测出处数据中大量系统事件造成的网络攻击,我们首先用一个混合图来模拟出处数据,以捕捉每个系统实体的丰富背景信息(例如流程、档案、套接头等),并学习每个系统实体的语义性矢量代表。然后,我们通过取样一个小型和紧凑的本地图表进行网络攻击探测,并将关键系统实体分类为恶意或良性。我们首先用一个混合图来模拟出源数据数据数据数据数据数据数据数据数据数据数据,以获取基于两种网络探测方法的测试结果。我们根据两个网络探测模型进行了一系列实验。我们用两个网络探测模型来试验,以测试了基于其他实验方法的测试结果学习。