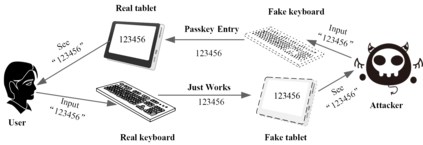
To defeat security threats such as man-in-the-middle (MITM) attacks, Bluetooth Low Energy (BLE) 4.2 and 5.x introduce the Secure Connections Only mode, under which a BLE device accepts only secure paring protocols including Passkey Entry and Numeric Comparison from an initiator, e.g., an Android mobile. However, the BLE specification does not explicitly require the Secure Connection Only mode of the initiator. Taking the Android's BLE programming framework for example, we found that it cannot enforce secure pairing, invalidating the security protection provided by the Secure Connection Only mode. The same problem applies to Apple iOS too. Specifically, we examine the life cycle of a BLE pairing process in Android and identify four severe design flaws. These design flaws can be exploited by attackers to perform downgrading attacks, forcing the BLE pairing protocols to run in the insecure mode without the users' awareness. To validate our findings, we selected and tested 18 popular BLE commercial products and our experimental results proved that downgrading attacks and MITM attacks were all possible to these products. All 3501 BLE apps from Androzoo are also subject to these attacks. For defense, we have designed and implemented a prototype of the Secure Connection Only mode on Android 8 through the Android Open Source Project (AOSP). We have reported the identified BLE pairing vulnerabilities to Bluetooth Special Interest Group (SIG), Google, Apple, Texas Instruments (TI) and all of them are actively addressing this issue. Google rated the reported security flaw a High Severity.
翻译:为了击败中途人攻击(MITM)等安全威胁,蓝牙低能(Blue牙低能)4.2和5.x引入了安全连接唯一模式,根据这一模式,破伤风装置只接受由启动者(如安纳罗尔德机动车)发出的安全分解协议,包括钥匙入口和数字比较。然而,破伤风规格没有明确要求启动者采用安全连接唯一模式。以安纳洛尔特的低能编程框架为例,我们发现它无法强制实施安全配对,使安全连接仅提供的安全保护无效。同样的问题也适用于苹果色相连接系统。具体地说,我们检查了安纳罗尔特配对流程的生命周期,并找出了四个严重的设计缺陷。攻击者可以利用这些设计缺陷来进行降级攻击,迫使混离子对齐协议以不安全的方式运行。为了验证我们的发现,我们选择并测试了18种流行的混版商业产品,我们的实验结果证明,降级攻击和MITM攻击都是这些产品的可能。同样的问题也适用于苹果。我们3501G(S)从S号搜索中, 也报告了一个特殊的SLOILO值 。我们从S 的GLILO(我们从安全安全等级到S) 做了一个S