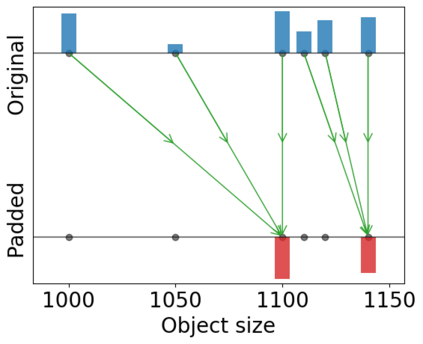
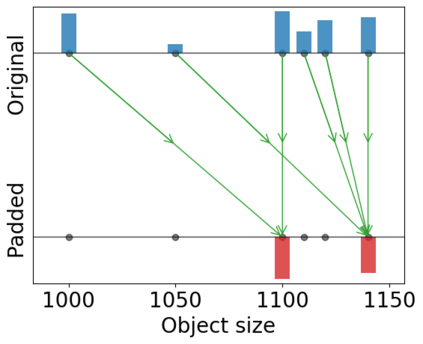
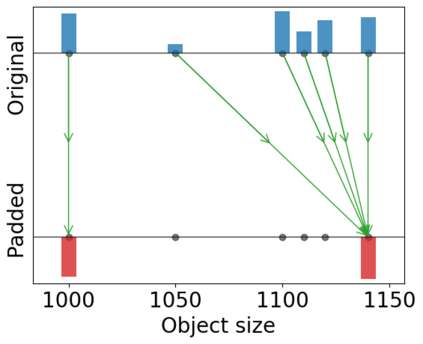
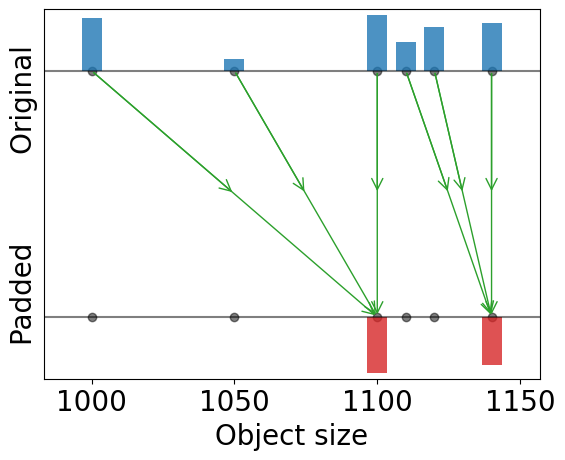
An attacker can gain information of a user by analyzing its network traffic. The size of transferred data leaks information about the file being transferred or the service being used, and this is particularly revealing when the attacker has background knowledge about the files or services available for transfer. To prevent this, servers may pad their files using a padding scheme, changing the file sizes and preventing anyone from guessing their identity uniquely. This work focuses on finding optimal padding schemes that keep a balance between privacy and the costs of bandwidth increase. We consider R\'enyi-min leakage as our main measure for privacy, since it is directly related with the success of a simple attacker, and compare our algorithms with an existing solution that minimizes Shannon leakage. We provide improvements to our algorithms in order to optimize average total padding and Shannon leakage while minimizing R\'enyi-min leakage. Moreover, our algorithms are designed to handle a more general and important scenario in which multiple servers wish to compute padding schemes in a way that protects the servers' identity in addition to the identity of the files.
翻译:攻击者可以通过分析其网络流量获取用户信息。 传输的数据的大小会泄漏关于被传输的文件或使用的服务的信息, 当攻击者对可供传输的文件或服务有背景知识时, 这一点尤其能说明问题。 为了防止这种情况, 服务器可以使用套头计划, 改变文件大小, 防止任何人单独猜测自己的身份。 这项工作的重点是寻找最佳套头计划, 保持隐私与带宽增加成本之间的平衡。 我们认为R\' enyi- min 渗漏是我们的主要隐私衡量标准, 因为它与简单的攻击者的成功直接相关, 并且将我们的算法与现有解决方案进行比较, 以最大限度地减少香农渗漏。 我们改进我们的算法, 以便优化平均套头和香农渗漏, 同时尽量减少R\ enyi-min 渗漏。 此外, 我们的算法旨在处理一个更加普遍和重要的假设, 即多个服务器希望编译套接系统的方式保护服务器的身份, 除了文件的身份之外还保护服务器的身份。