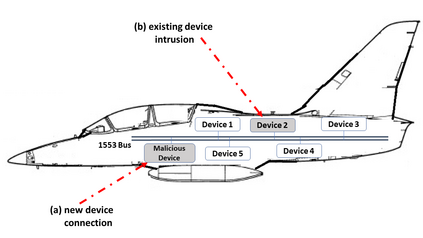
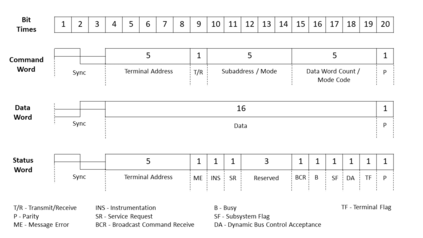
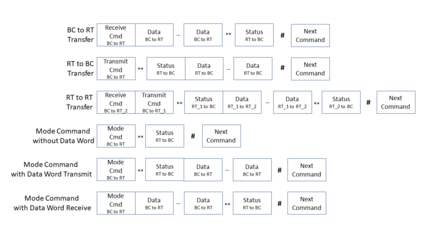
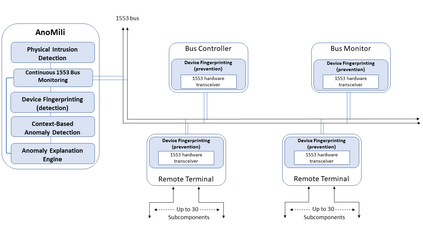
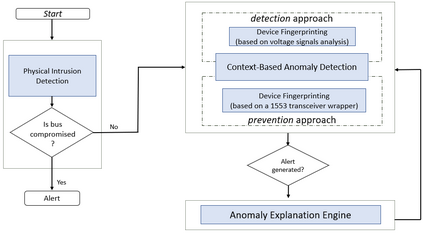
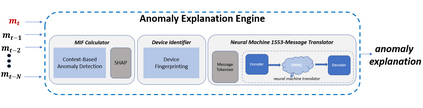
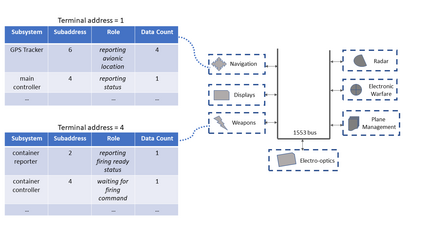
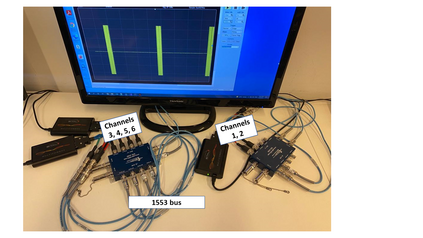
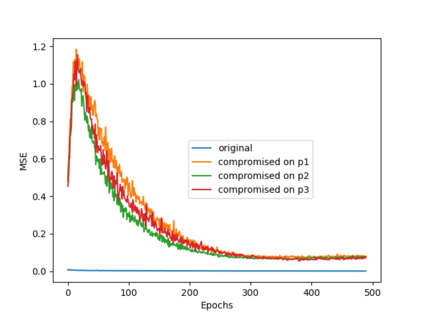
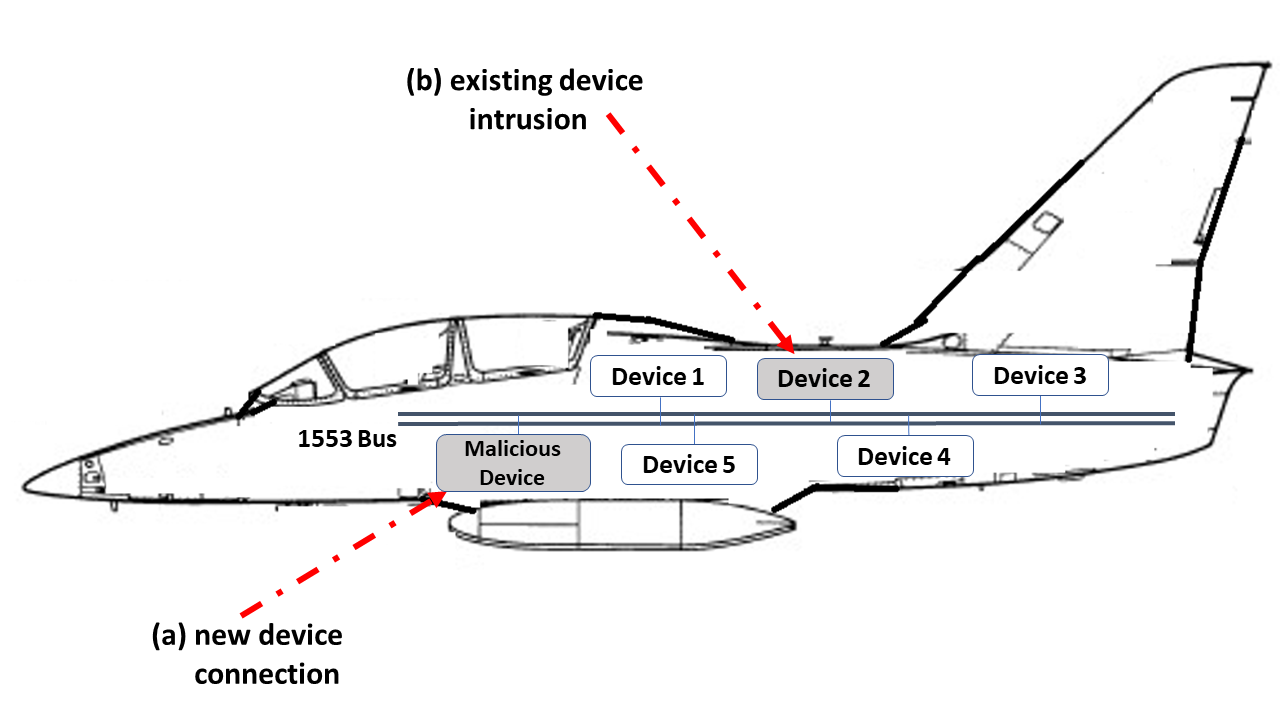
MIL-STD-1553, a standard that defines a communication bus for interconnected devices, is widely used in military and aerospace avionic platforms. Due to its lack of security mechanisms, MIL-STD-1553 is exposed to cyber threats. The methods previously proposed to address these threats are very limited, resulting in the need for more advanced techniques. Inspired by the defense in depth principle, we propose AnoMili, a novel protection system for the MIL-STD-1553 bus, which consists of: (i) a physical intrusion detection mechanism that detects unauthorized devices connected to the 1553 bus, even if they are passive (sniffing), (ii) a device fingerprinting mechanism that protects against spoofing attacks (two approaches are proposed: prevention and detection), (iii) a context-based anomaly detection mechanism, and (iv) an anomaly explanation engine responsible for explaining the detected anomalies in real time. We evaluate AnoMili's effectiveness and practicability in two real 1553 hardware-based testbeds. The effectiveness of the anomaly explanation engine is also demonstrated. All of the detection and prevention mechanisms employed had high detection rates (over 99.45%) with low false positive rates. The context-based anomaly detection mechanism obtained perfect results when evaluated on a dataset used in prior work.
翻译:MIL-STD-1553是界定连接装置通信总线的标准,在军用和航空航天航空平台中广泛使用。由于缺乏安全机制,MIL-STD-1553面临网络威胁。以前提出的应对这些威胁的方法非常有限,导致需要更先进的技术。在深入原则的启发下,我们提议AnoMili,这是MIL-STD-1553总线的新的保护系统,包括:(一) 物理入侵探测机制,探测与1553年总线相连的未经授权装置,即使这些装置是被动的(吸入);(二) 设备指纹识别机制,保护免受潜伏攻击(提出了两种办法:预防和检测);(三) 基于背景的异常探测机制,以及(四) 异常解释引擎,负责实时解释所检测到的异常。我们评估AnoMili在两个真实的1553年硬基试床中的有效性和可行性。还演示了异常解释引擎的有效性。所有探测和预防机制在使用之前的检测率方面都采用了一种精确的检测率(9-945年),使用了一种精确的数据。所有探测和预防机制都使用了一种精确的精确率。