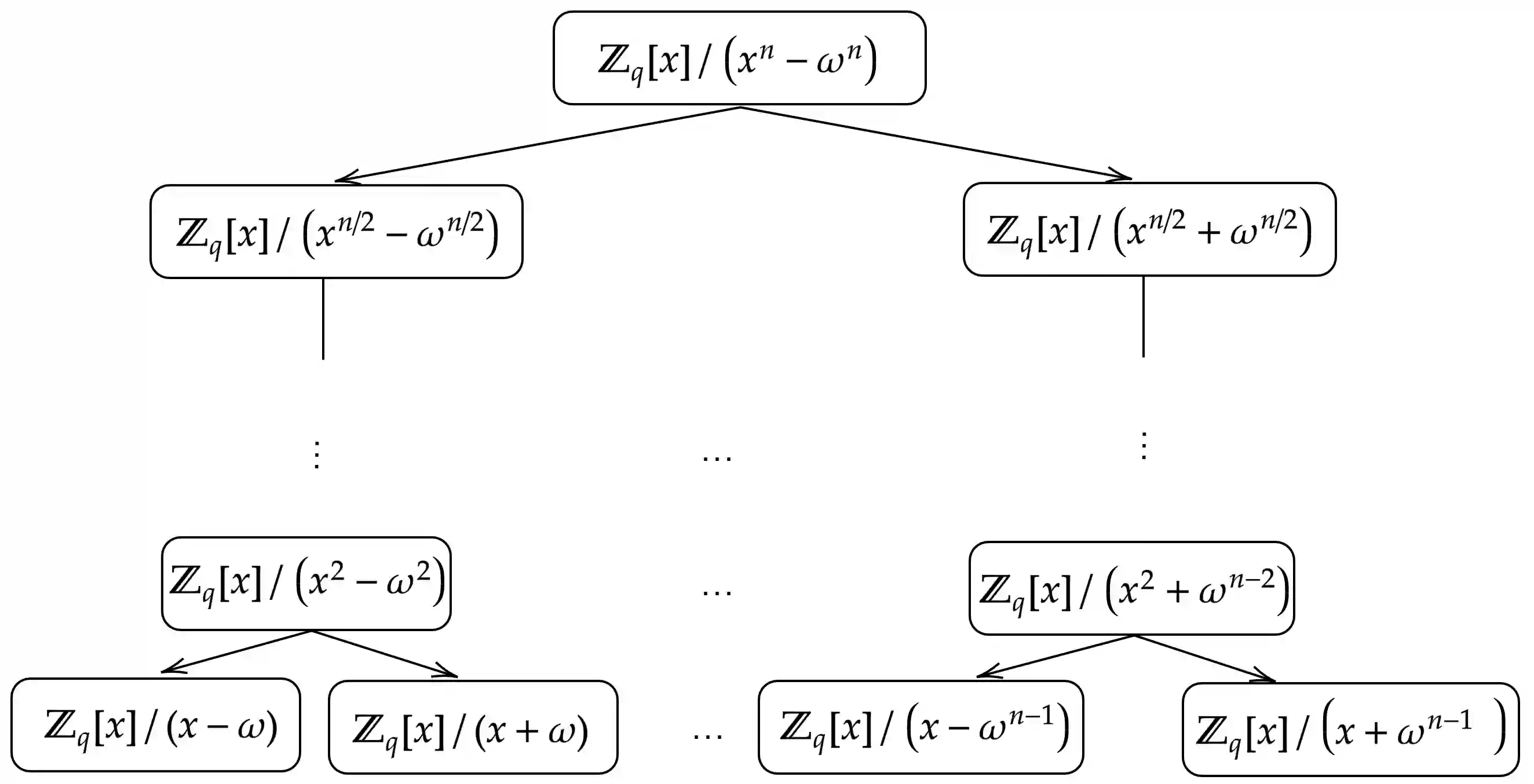
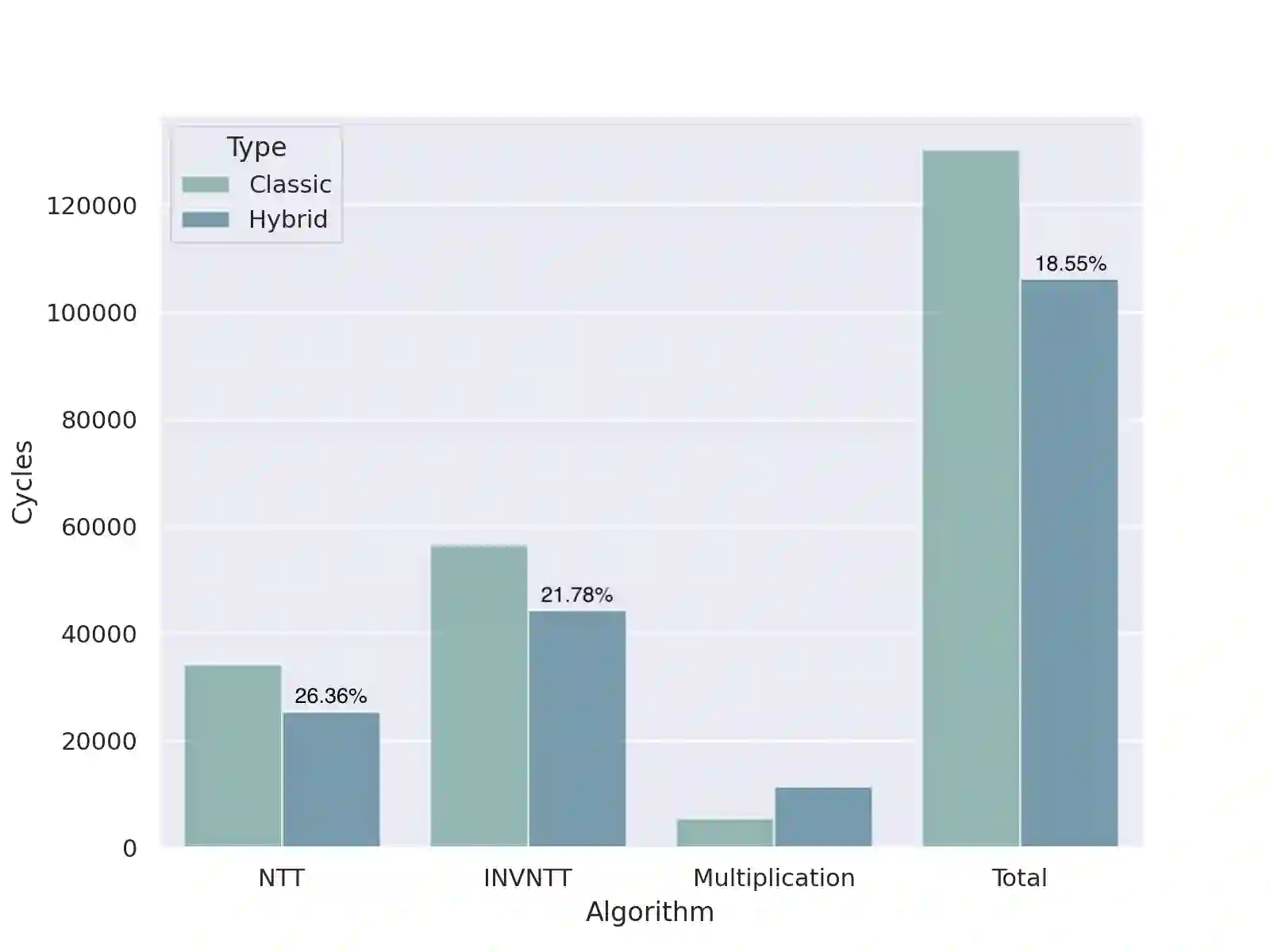
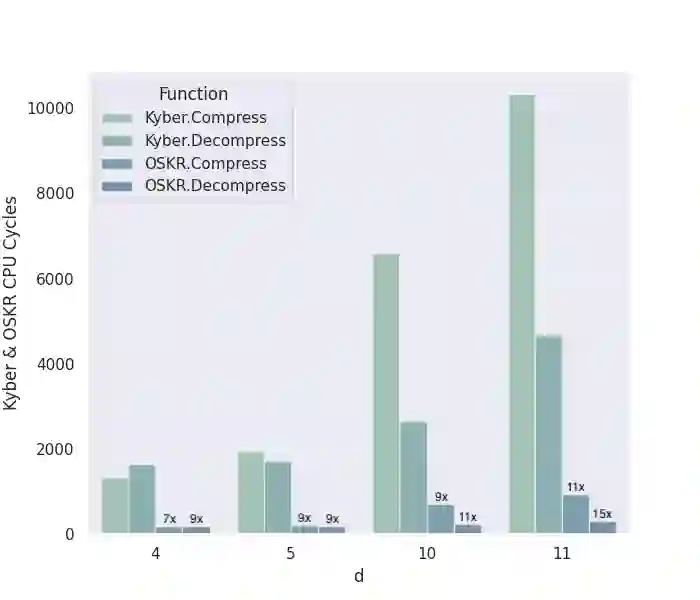
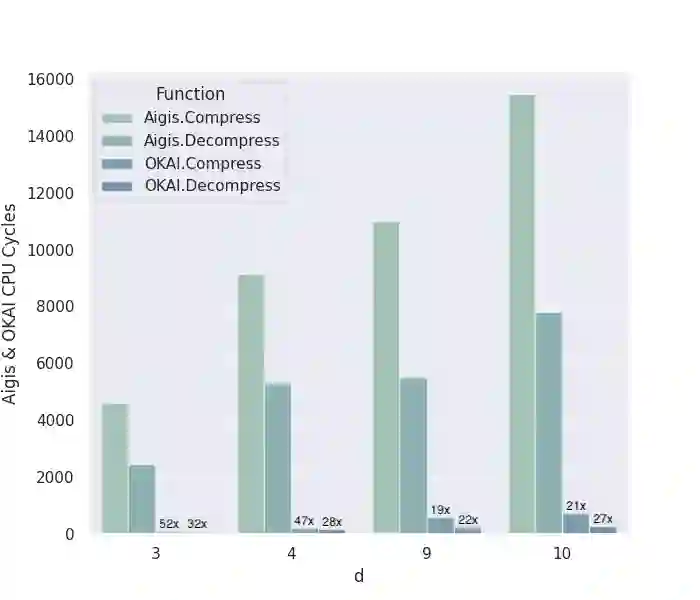
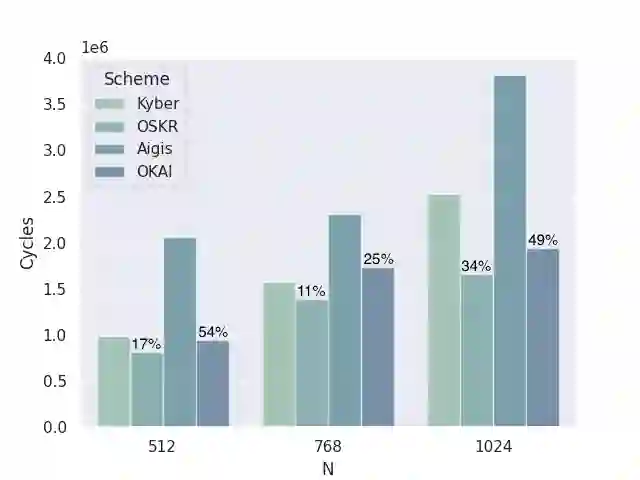
In this work, we make \emph{systematic} optimizations of key encapsulation mechanisms (KEM) based on module learning-with-errors (MLWE), covering algorithmic design, fundamental operation of number-theoretic transform (NTT), approaches to expanding encapsulated key size, and optimized implementation coding. We focus on Kyber (now in the Round-3 finalist of NIST PQC standardization) and Aigis (a variant of Kyber proposed at PKC 2020). By careful analysis, we first observe that the algorithmic design of Kyber and Aigis can be optimized by the mechanism of asymmetric key consensus with noise (AKCN) proposed in \cite{JZ16,JZ19}. Specifically, the decryption process can be simplified with AKCN, leading to a both faster and less error-prone decryption process. Moreover, the AKCN-based optimized version has perfect compatibility with the deployment of Kyber/Aigis in reality, as they can run on the same parameters, the same public key, and the same encryption process. We make a systematic study of the variants of NTT proposed in recent years for extending its applicability scope, make concrete analysis of their exact computational complexity, and in particular show their equivalence. We then present a new variant named hybrid-NTT (H-NTT), combining the advantages of existing NTT methods, and derive its optimality in computational complexity. The H-NTT technique not only has larger applicability scope but also allows for modular and unified implementation codes of NTT operations even with varying module dimensions. We analyze and compare the different approaches to expand the size of key to be encapsulated (specifically, 512-bit key for dimension of 1024), and conclude with the most economic approach. To mitigate the compatibility issue in implementations we adopt the proposed H-NTT method.
翻译:在这项工作中,我们优化了基于模块学习用传感器(MLWE)的关键封装机制(KEM),包括算法设计、数字理论变换基本操作(NTT)、扩大封装关键大小的方法和优化执行编码。我们侧重于Kyber(目前是NIST PQC标准化的第三回合决赛)和Aigis(在PKC 2020年提出了Kyber的变异版本 ) 。通过仔细分析,我们首先观察到,Kyber和Aigis的统一算法设计可以优化,通过在\\cite{JZ16,JZ19}中提议的与噪音(AKCN)的不对称关键共识(AKCN)的更大适用性(AKCN)机制。具体地说,解密过程可以简化与AKCN之间的过程,导致更快和不太易出错的解算过程。此外,基于AKCN的优化版本与现实中Kyber/Aigs的部署完全相匹配,但可以运行相同的参数、相同的公用钥匙和相同的加密过程。我们通过一个系统化的系统化范围分析其当前具体计算方法,现在的NTTTTF的计算方法也使得其目前采用新的变式变式的计算方法。