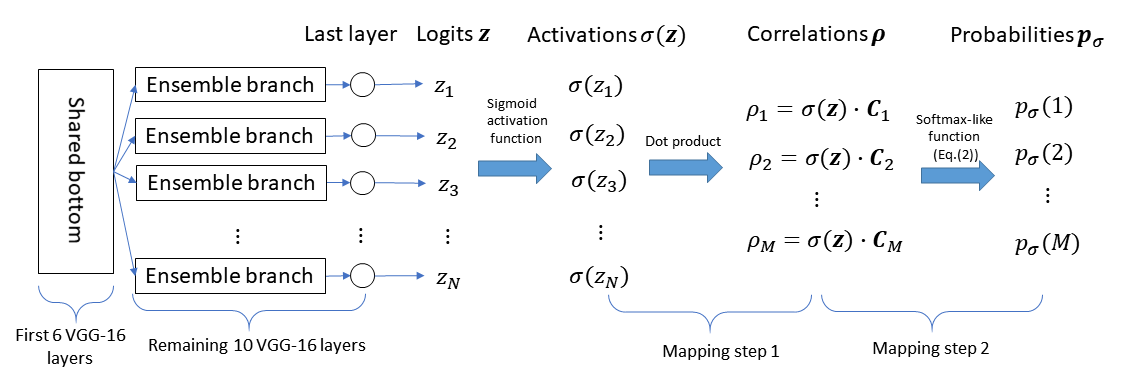
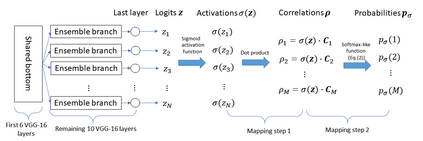
Adversarial examples represent a great security threat for deep learning systems, pushing researchers to develop suitable defense mechanisms. The use of networks adopting error-correcting output codes (ECOC) has recently been proposed to deal with white-box attacks. In this paper, we carry out an in-depth investigation of the security achieved by the ECOC approach. In contrast to previous findings, our analysis reveals that, when the attack in the white-box framework is carried out properly, the ECOC scheme can be attacked by introducing a rather small perturbation. We do so by considering both the popular adversarial attack proposed by Carlini and Wagner (C&W) and a new variant of C&W attack specifically designed for multi-label classification architectures, like the ECOC-based structure. Experimental results regarding different classification tasks demonstrate that ECOC networks can be successfully attacked by both the original C&W attack and the new attack.
翻译:反对立实例对深层学习系统构成了巨大的安全威胁,迫使研究人员开发适当的防御机制。最近有人提议使用采用错误校正产出代码的网络来对付白箱袭击。在本文件中,我们深入调查了ECO方法所取得的安全性。与以前的调查结果相反,我们的分析表明,当白箱框架中的攻击进行得当时,EEC计划可以通过引入相当小的干扰来攻击。我们这样做是因为考虑到Carlini和Wagner(C&W)提出的流行对抗性攻击,以及专门为多标签分类结构设计的新的C&W攻击变种,如ECOC结构。关于不同分类任务的实验结果表明,EEC网络可以成功地受到原C&W攻击和新攻击的打击。