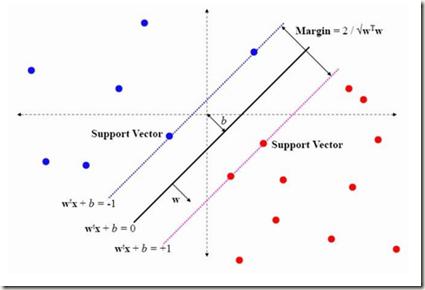
The digital transformation faces tremendous security challenges. In particular, the growing number of cyber-attacks targeting Internet of Things (IoT) systems restates the need for a reliable detection of malicious network activity. This paper presents a comparative analysis of supervised, unsupervised and reinforcement learning techniques on nine malware captures of the IoT-23 dataset, considering both binary and multi-class classification scenarios. The developed models consisted of Support Vector Machine (SVM), Extreme Gradient Boosting (XGBoost), Light Gradient Boosting Machine (LightGBM), Isolation Forest (iForest), Local Outlier Factor (LOF) and a Deep Reinforcement Learning (DRL) model based on a Double Deep Q-Network (DDQN), adapted to the intrusion detection context. The best performance was achieved by LightGBM, closely followed by SVM. Nonetheless, iForest displayed good results against unknown attacks and the DRL model demonstrated the possible benefits of employing this methodology to continuously improve the detection. Overall, the obtained results indicate that the analyzed techniques are well suited for IoT intrusion detection.
翻译:数字转换面临巨大的安全挑战,特别是越来越多的针对物联网(IoT)系统的网络攻击重申需要可靠地探测恶意网络活动,本文件比较分析了在IoT-23数据集的九种恶意捕获软件方面,对监督、不受监督和强化的学习技术进行比较分析,同时考虑到二进制和多级分类设想,开发的模型包括支持矢量机(SVM)、极端严重推动(XGBost)、轻重推引机(LightGBM)、隔离森林(IFest)、地方外层因素(LOF)和基于双深Q-网络(DDQN)的深强化学习模型,该模型适应入侵探测环境。LightGBM取得了最佳的绩效,SVM紧随其后。然而,IForest展示了对未知袭击的良好效果,DRL模型展示了利用这一方法不断改进探测的可能好处。总的来说,获得的结果表明,分析的技术非常适合IOT入侵探测。