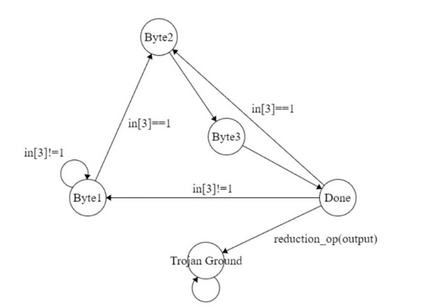
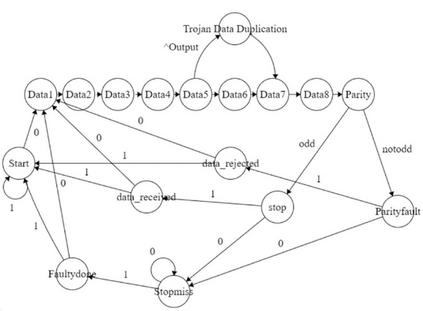
In this paper, we will demonstrate Hardware Trojan Attacks on four different digital designs implemented on FPGA. The hardware trojan is activated based on special logical and reduction-based operations on vectors which makes the trojan-activity as silent and effective as possible. In this paper, we have introduced 5 novel trojan attack methodologies.
翻译:在本文中,我们将展示对在FPGA上实施的四种不同数字设计的硬件Trojan攻击。硬件Trojan是根据对矢量的特殊逻辑和减少操作启动的,这种操作使天体活动尽可能安静和有效。在本文中,我们引入了5种新型的天体攻击方法。
相关内容
Arxiv
11+阅读 · 2021年9月3日