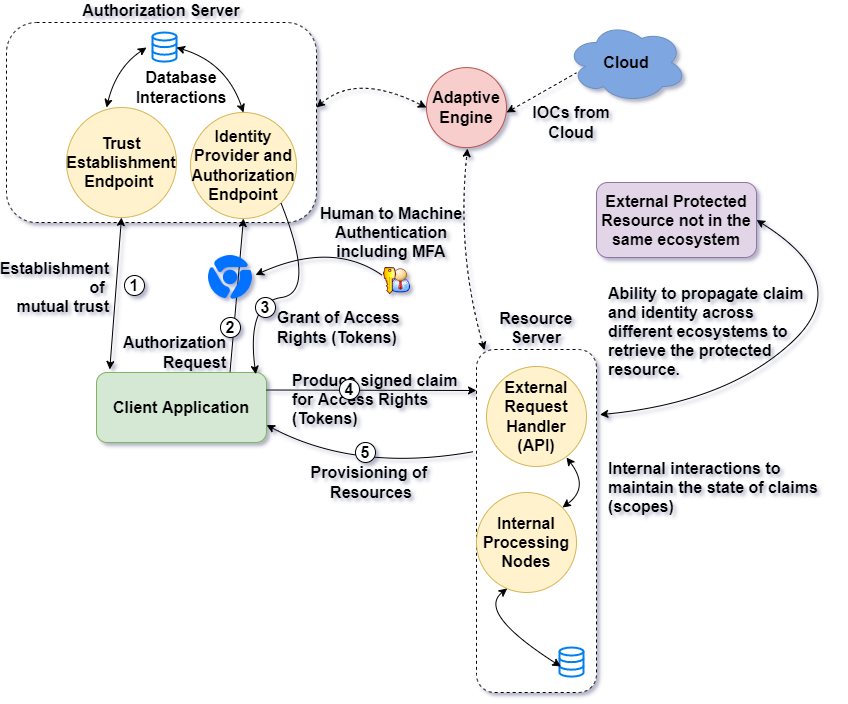
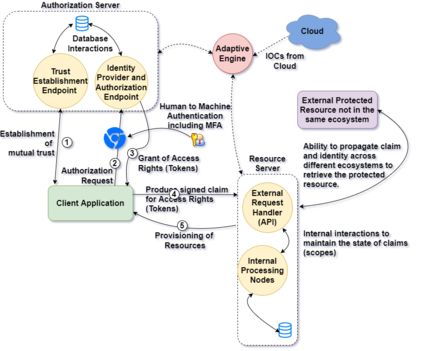
A strong cyber attack is capable of degrading the performance of any Information Technology (IT) or Operational Technology (OT) system. In recent cyber attacks, credential theft emerged as one of the primary vectors of gaining entry into the system. Once, an attacker has a foothold in the system, they use token manipulation techniques to elevate the privileges and access protected resources. This makes authentication and authorization a critical component for a secure and resilient cyber system. In this paper we consider the design considerations for such a secure and resilient authentication and authorization framework capable of self-adapting based on the risk scores and trust profiles. We compare this design with the existing standards such as OAuth 2.0, OpenID Connect and SAML 2.0. We then study popular threat models such as STRIDE and PASTA and summarize the resilience of the proposed architecture against common and relevant threat vectors. We call this framework Resilient Risk-based Adaptive Authentication and Authorization (RAD-AA). The proposed framework excessively increases the cost for an adversary to launch any cyber attack and provides much-needed strength to critical infrastructure.
翻译:强大的网络攻击能够降低任何信息技术(IT)或操作技术(OT)系统的性能。在最近的网络攻击中,身份盗窃成为进入系统的主要矢量之一。一旦攻击者在系统中有一个立足点,他们就使用象征性操纵技术来提升特权和使用受保护的资源。这使得认证和授权成为安全和具有复原力的网络系统的关键组成部分。在本文件中,我们考虑设计这样一个安全和有复原力的认证和授权框架,能够根据风险分数和信任情况进行自我适应。我们将这一设计与OAuth 2.0、OOOID 连接和SAML 2.0等现有标准进行比较。我们随后研究流行的威胁模型,如STIDE和PASTA, 并总结拟议架构对共同和相关威胁矢量的复原力。我们称之为这个具有弹性的基于风险的适应性适应性验证和授权框架(RAD-AAA)。拟议框架过分增加了对手发起任何网络攻击和提供关键基础设施急需的力量的成本。