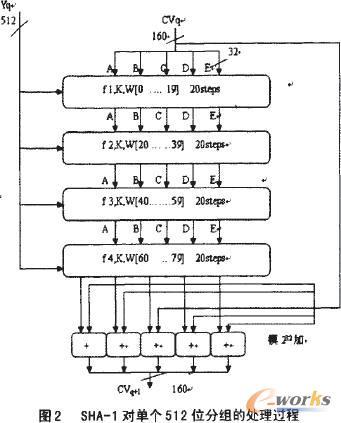
Recent cryptanalytic attacks have exposed the vulnerabilities of some widely used cryptographic hash functions like MD5 and SHA-1. Attacks in the line of differential attacks have been used to expose the weaknesses of several other hash functions like RIPEMD, HAVAL. In this paper we propose a new efficient hash algorithm that provides a near random hash output and overcomes some of the earlier weaknesses. Extensive simulations and comparisons with some existing hash functions have been done to prove the effectiveness of the BSA, which is an acronym for the name of the 3 authors.
翻译:最近的加密分析攻击暴露了诸如MD5和SHA-1等一些广泛使用的加密散列功能的脆弱性,不同攻击线上的攻击被用来暴露其他几种散列功能的弱点,如RIPEMD、HAVAL等,在本文件中,我们提出一种新的高效散列算法,提供近乎随机的散列输出,克服了早先的一些弱点,对一些现有的散列功能进行了广泛的模拟和比较,以证明BSA的有效性,BSA是3名作者名字的缩略语。