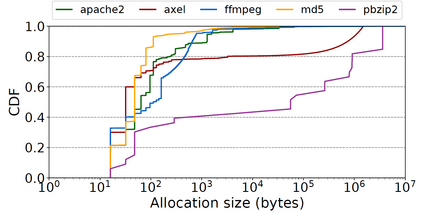
ARM recently introduced a security feature called Memory Tagging Extension or MTE, which is designed to defend against common memory safety vulnerabilities, such as buffer overflow and use after free. In this paper, we examine three aspects of MTE. First, we survey how modern software systems, such as Glibc, Android, Chrome, Linux, and LLVM, use MTE. We identify some common weaknesses and propose improvements. Second, we develop and experiment with an architectural improvement to MTE that improves its memory efficiency. Our design enables longer memory tags, which improves the accuracy of MTE. Finally, we discuss a number of enhancements to MTE to improve its security against certain memory safety attacks.
翻译:ARM最近推出了一个名为“记忆拖累扩展”或“MTE”的安全特征,其目的是防范共同记忆安全脆弱性,例如缓冲溢出和免费使用。在本文中,我们研究了MTE的三个方面。首先,我们调查了现代软件系统,如Glibc、Android、Chrome、Linux和LLLVM如何使用MTE。我们找出了一些共同的弱点并提出了改进建议。第二,我们开发和试验了MTE的建筑改进,以提高其记忆效率。我们的设计使得存储标记更长,提高了MTE的准确性。最后,我们讨论了对MTE的一些改进措施,以提高其防范某些记忆安全攻击的安全性。
相关内容
- Today (iOS and OS X): widgets for the Today view of Notification Center
- Share (iOS and OS X): post content to web services or share content with others
- Actions (iOS and OS X): app extensions to view or manipulate inside another app
- Photo Editing (iOS): edit a photo or video in Apple's Photos app with extensions from a third-party apps
- Finder Sync (OS X): remote file storage in the Finder with support for Finder content annotation
- Storage Provider (iOS): an interface between files inside an app and other apps on a user's device
- Custom Keyboard (iOS): system-wide alternative keyboards
Source: iOS 8 Extensions: Apple’s Plan for a Powerful App Ecosystem