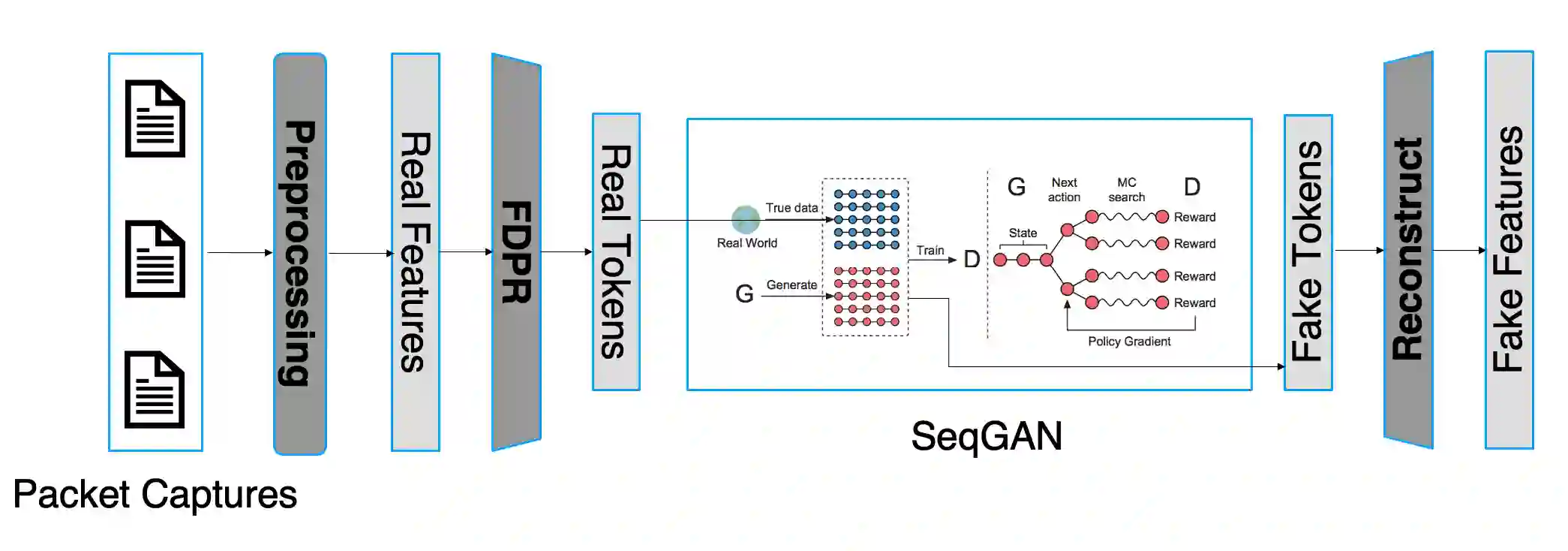
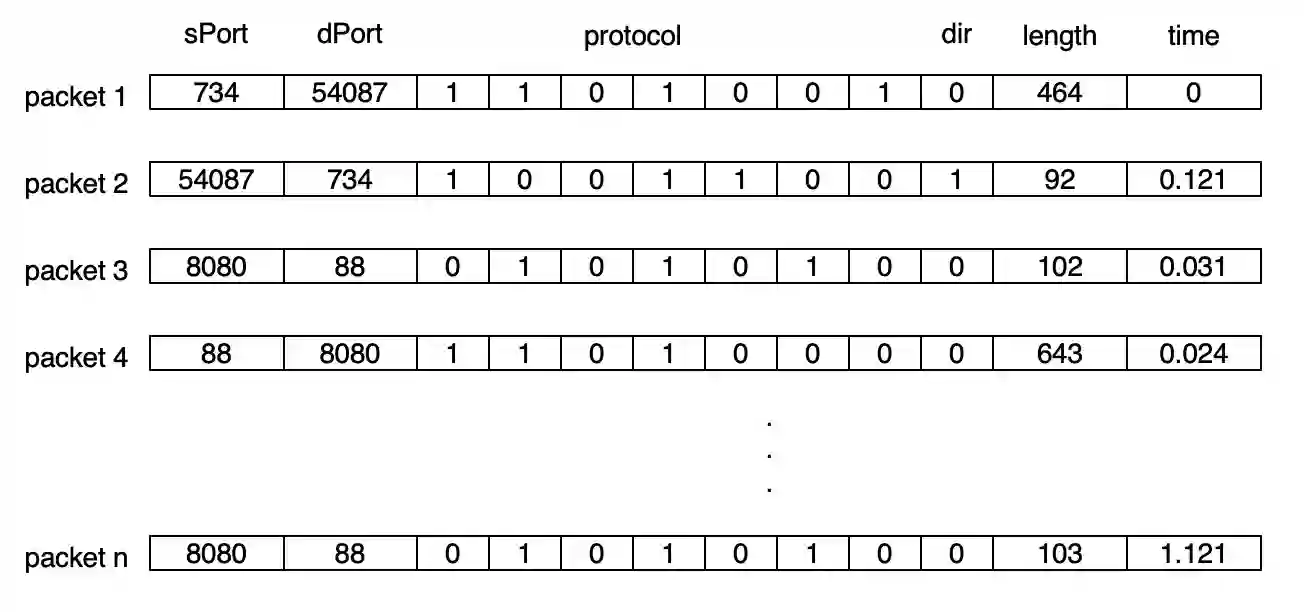
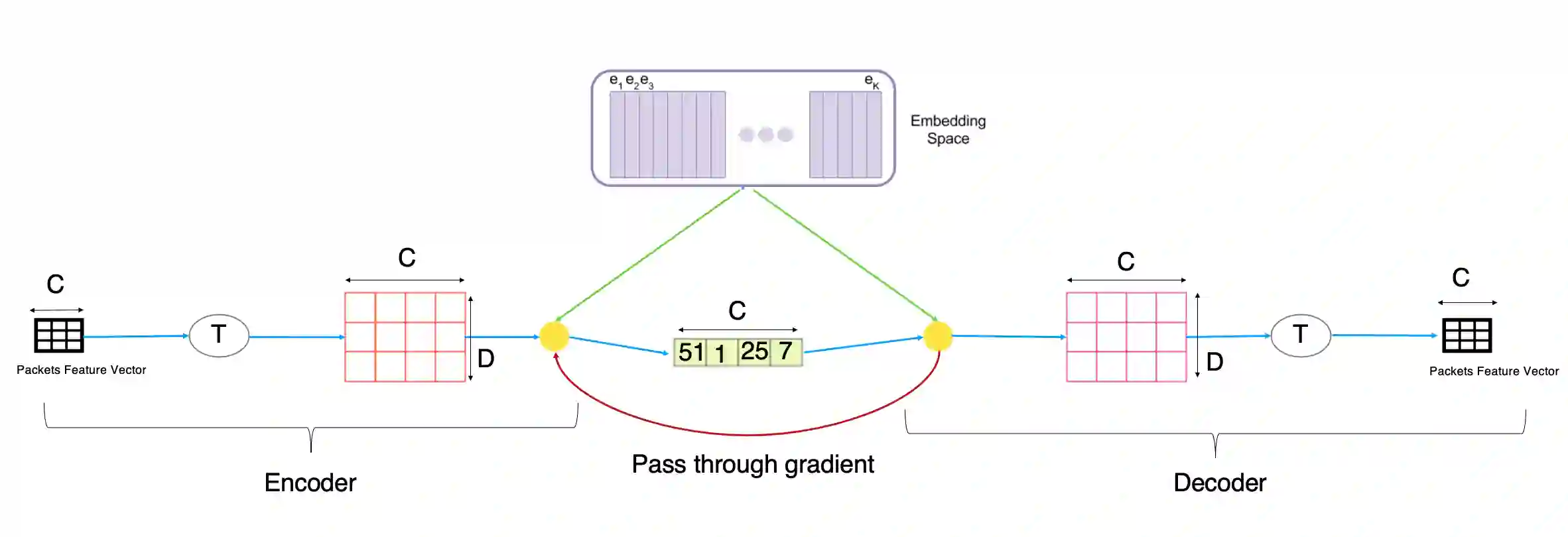
Over the years, honeypots emerged as an important security tool to understand attacker intent and deceive attackers to spend time and resources. Recently, honeypots are being deployed for Internet of things (IoT) devices to lure attackers, and learn their behavior. However, most of the existing IoT honeypots, even the high interaction ones, are easily detected by an attacker who can observe honeypot traffic due to lack of real network traffic originating from the honeypot. This implies that, to build better honeypots and enhance cyber deception capabilities, IoT honeypots need to generate realistic network traffic flows. To achieve this goal, we propose a novel deep learning based approach for generating traffic flows that mimic real network traffic due to user and IoT device interactions. A key technical challenge that our approach overcomes is scarcity of device-specific IoT traffic data to effectively train a generator. We address this challenge by leveraging a core generative adversarial learning algorithm for sequences along with domain specific knowledge common to IoT devices. Through an extensive experimental evaluation with 18 IoT devices, we demonstrate that the proposed synthetic IoT traffic generation tool significantly outperforms state of the art sequence and packet generators in remaining indistinguishable from real traffic even to an adaptive attacker.
翻译:多年来,蜜罐已成为了解攻击者意图并欺骗攻击者花费时间和资源的重要安全工具。最近,蜜罐被部署在物联网(IoT)设备上,以诱骗攻击者并了解他们的行为。然而,大多数现有的IoT蜜罐,甚至是高交互蜜罐,都很容易被攻击者发现,因为缺乏从蜜罐发出的真实网络流量。这意味着,为建立更好的蜜罐和增强网络欺骗能力,IoT蜜罐需要生成真实的网络流量。为了实现这个目标,我们提出了一种基于深度学习的方法,用于生成由用户和IoT设备交互引起的类似真实网络流量的流量。我们的方法克服了一个关键的技术难题,即缺乏特定设备IoT流量数据以有效地训练生成器。我们通过利用适用于序列的核心生成对抗式学习算法以及IoT设备的通用领域知识来解决这个难题。通过与18个IoT设备的广泛实验评估,我们证明了所提出的合成IoT流量生成工具在保持对适应性攻击者甚至是对真实流量都无法区分方面,明显优于现有的序列和数据包生成器。