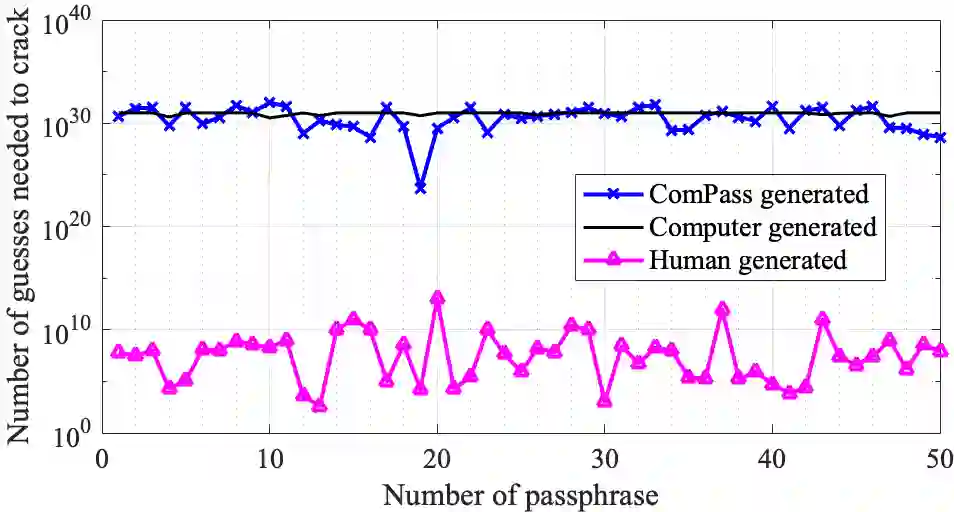
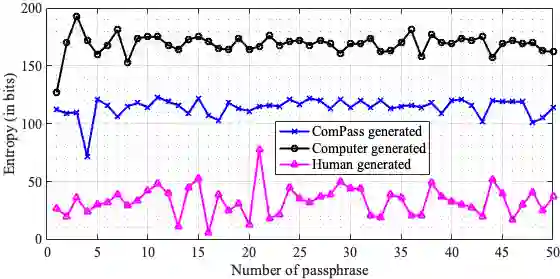
Secure and scalable device provisioning is a notorious challenge in Wi-Fi. WPA2/WPA3 solutions take user interaction and a strong passphrase for granted. However, the often weak passphrases are subject to guessing attacks. Notably, there has been a significant rise of cyberattacks on Wi-Fi home or small office networks during the COVID-19 pandemic. This paper addresses the device provisioning problem in Wi-Fi (personal mode) and proposes ComPass protocol to supplement WPA2/WPA3. ComPass replaces the pre-installed or user-selected passphrases with automatically generated ones. For this, ComPass employs Physical Layer Security and extracts credentials from common random physical layer parameters between devices. Two major features make ComPass unique and superior compared to previous proposals: First, it employs phase information (rather than amplitude or signal strength) to generate the passphrase so that it is robust, scaleable, and impossible to guess. Our analysis showed that ComPass generated passphrases have 3 times more entropy than human generated passphrases (113-bits vs. 34-bits). Second, ComPass selects parameters such that two devices bind only within a certain proximity (less than 3m), hence providing practically useful in-build PLS-based authentiation. ComPass is available as a kernel module or as full firmware.
翻译:在 Wi-Fi 中,安全和可扩缩的装置提供是一个臭名昭著的挑战。 WPA2/WPA3 解决方案需要用户互动,并有一个强大的密码句。 但是,通常薄弱的密码句会受到猜测攻击。 值得注意的是,在COVID-19大流行期间,对Wi-Fi家或小型办公室网络网络的网络攻击明显上升。 本文涉及Wi-Fi(个人模式)中的设备提供问题, 并提议ComPass 协议来补充 WPA2/WPA3. ComPass 。 ComPass 以自动生成的密码句取代预先安装或用户选择的密码句。 为此,ComPass 使用物理层安全套,并从设备之间常见的随机物理层参数中提取证书。 与先前的提议相比, 有两个主要特征使得ComPass 独特和优越性: 首先,它使用阶段信息(而不是调频度或信号强度) 来生成密码句, 以便它能够强大、 缩放、 无法猜测。 我们的分析显示, ComPass 生成的密码片段比人类生成的密码句号号(113比13位和34位)要多3倍, 因此, 只能选择一个不固定的服务器作为固定的模块。