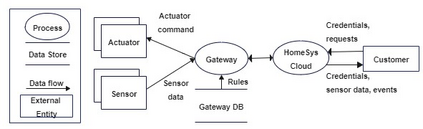
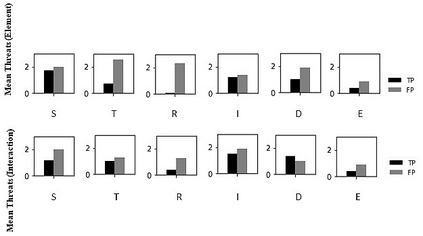
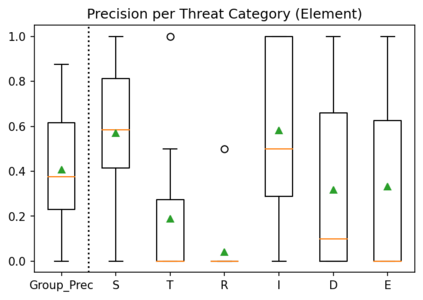
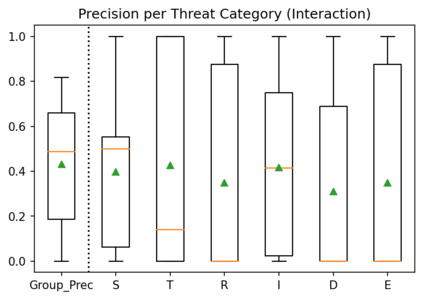
To avoid costly security patching after software deployment, security-by-design techniques (e.g., STRIDE threat analysis) are adopted in organizations to root out security issues before the system is ever implemented. Despite the global gap in cybersecurity workforce and the high manual effort required for performing threat analysis, organizations are ramping up threat analysis activities. However, past experimental results were inconclusive regarding some performance indicators of threat analysis techniques thus practitioners have little evidence for choosing the technique to adopt. To address this issue, we replicated a controlled experiment with STRIDE. Our study was aimed at measuring and comparing the performance indicators (productivity and precision) of two STRIDE variants (element and interaction). We conclude the paper by comparing our results to the original study.
翻译:为了避免软件部署后费用高昂的安全补丁,各组织采用逐个设计的安全技术(例如,STRIDE威胁分析),以便在系统实施之前根除安全问题。尽管全球网络安全工作人员队伍存在差距,而且进行威胁分析需要大量人工工作,但各组织正在加紧威胁分析活动。然而,过去关于威胁分析技术的一些业绩指标的实验结果没有定论,因此,从业人员没有多少证据选择采用这种技术。为了解决这一问题,我们复制了STRIDE的受控实验。我们的研究旨在衡量和比较STRIDE两个变异(要素和互动)的业绩指标(生产率和精确度)。我们通过将我们的结果与最初的研究进行比较来结束该文件。