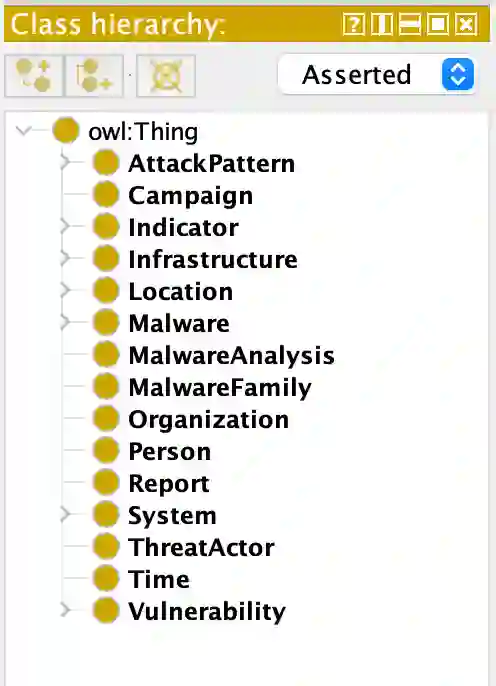
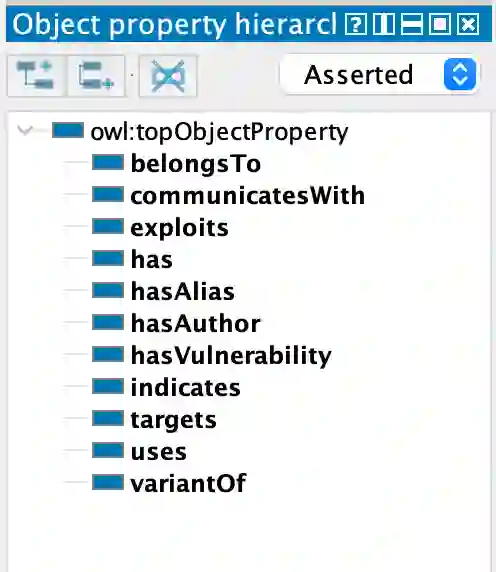
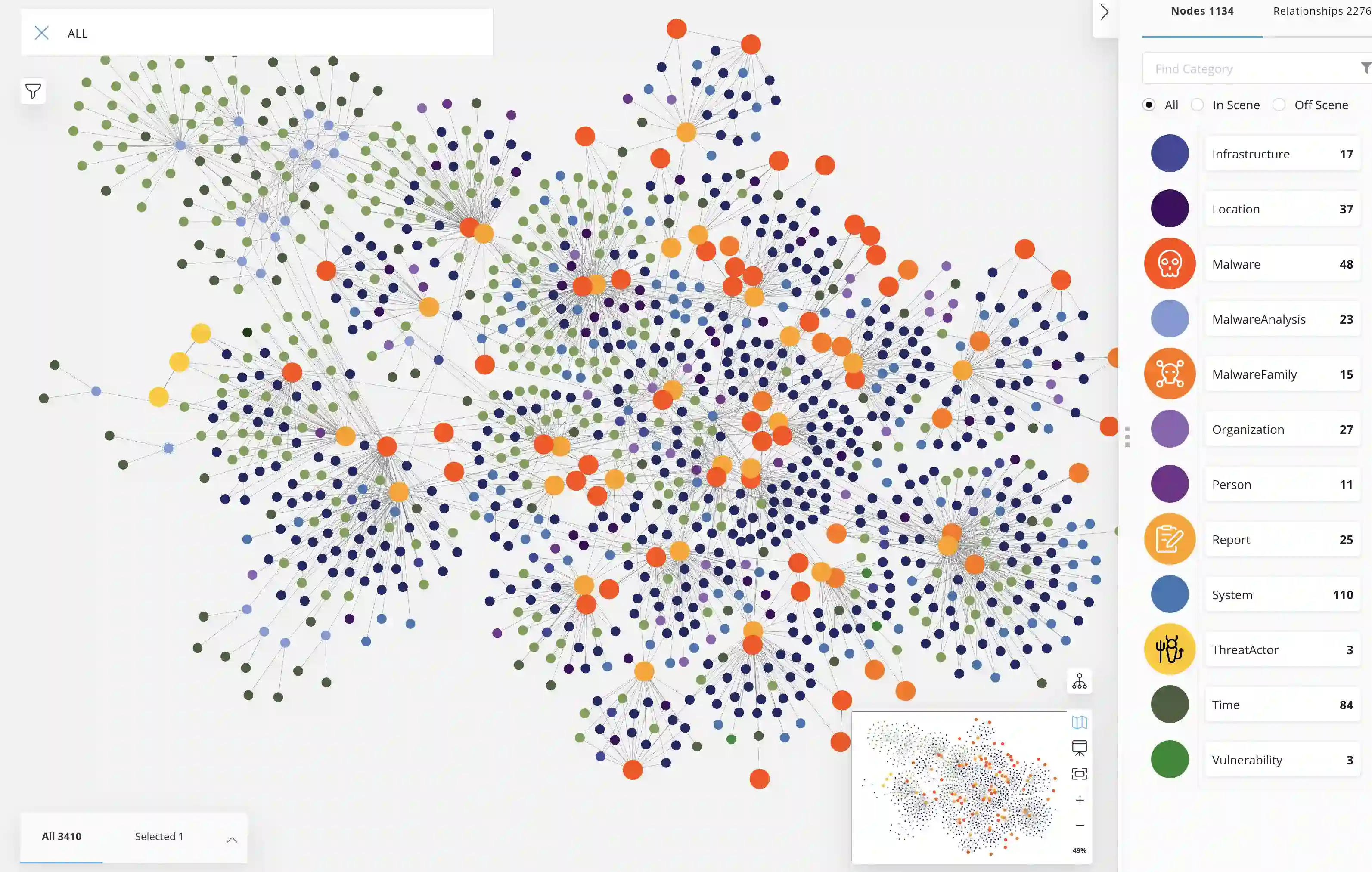
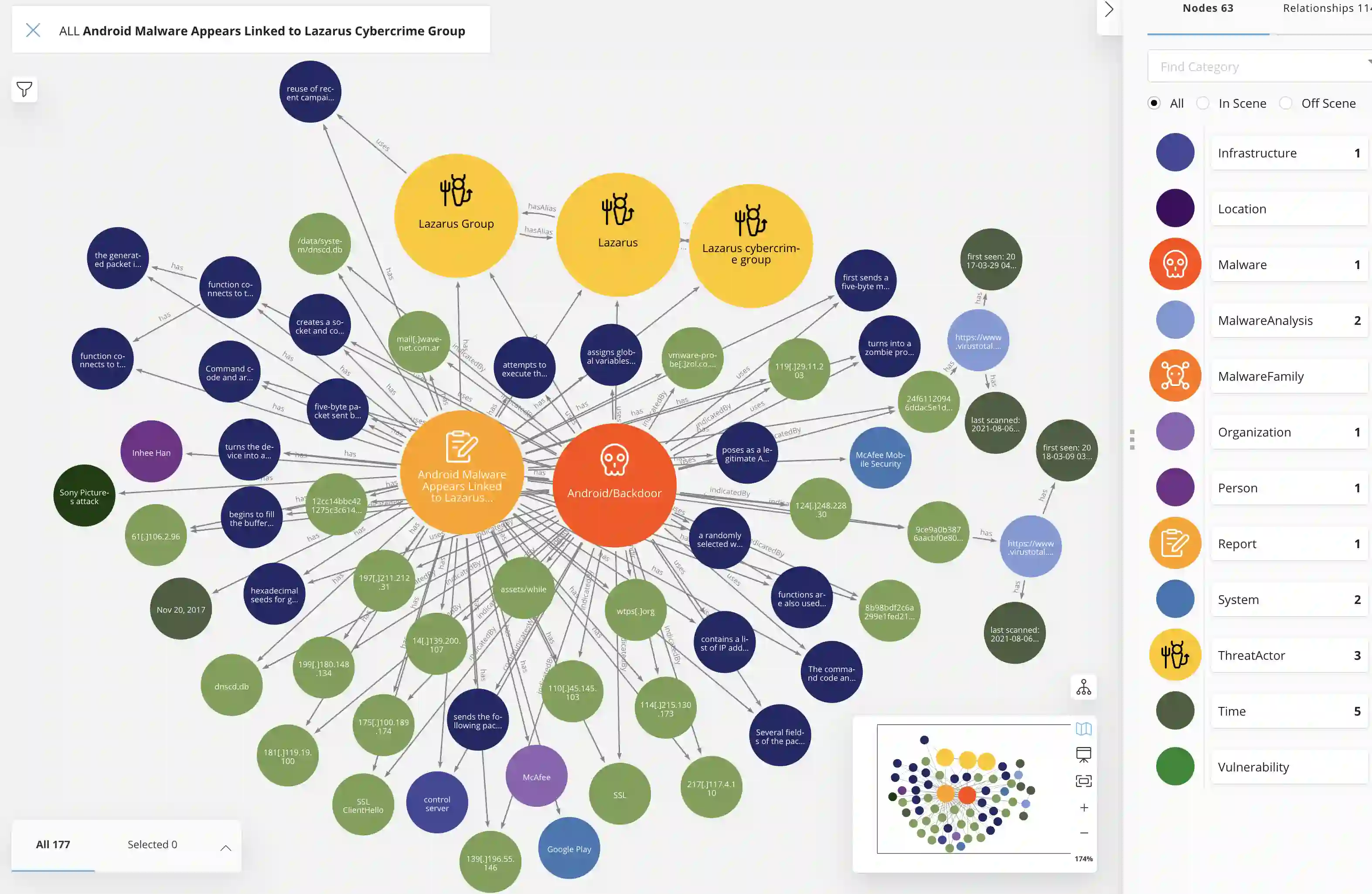
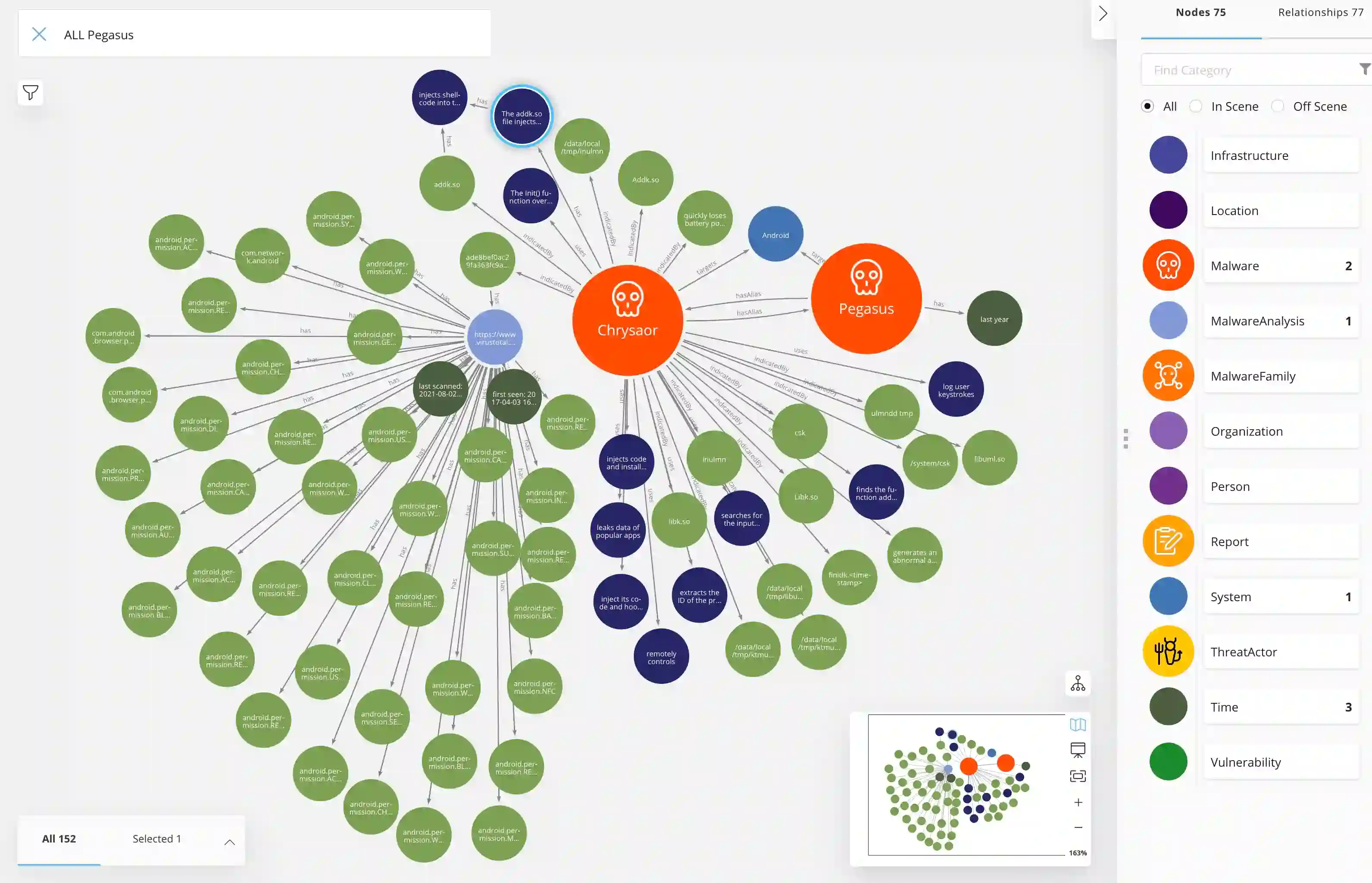
We present MalONT2.0 -- an ontology for malware threat intelligence \cite{rastogi2020malont}. New classes (attack patterns, infrastructural resources to enable attacks, malware analysis to incorporate static analysis, and dynamic analysis of binaries) and relations have been added following a broadened scope of core competency questions. MalONT2.0 allows researchers to extensively capture all requisite classes and relations that gather semantic and syntactic characteristics of an android malware attack. This ontology forms the basis for the malware threat intelligence knowledge graph, MalKG, which we exemplify using three different, non-overlapping demonstrations. Malware features have been extracted from CTI reports on android threat intelligence shared on the Internet and written in the form of unstructured text. Some of these sources are blogs, threat intelligence reports, tweets, and news articles. The smallest unit of information that captures malware features is written as triples comprising head and tail entities, each connected with a relation. In the poster and demonstration, we discuss MalONT2.0, MalKG, as well as the dynamically growing knowledge graph, TINKER.
翻译:我们介绍了麦隆图2.0 -- -- 恶意威胁情报的本体学 。新的类别(攻击模式、允许攻击的基础设施资源、采用攻击手段的基础设施资源、纳入静态分析的恶意软件分析以及对二进制的动态分析)和关系在核心能力问题范围扩大后又增加了。马伦图2.0使研究人员能够广泛捕捉所有必要的类别和关系,这些类别和关系收集了一种恶意和机器人恶意攻击的语义和合成特征。这种本体学构成恶意威胁情报知识图(MalKG)的基础,我们用三种不同的非重叠的演示来举例说明。从CTI关于恶意威胁情报的报告以及在因特网上共享的机器人威胁情报中提取了一些特征,并以非结构化文本的形式写成。其中一些来源是博客、威胁情报报告、推特和新闻文章。捕捉恶意软件特征的最小信息单位是由头部和尾部实体组成的三部实体,每个实体都与关系有关。在海报和演示中,我们讨论了MalONT2.0、MalKG,以及动态增长的知识图表。