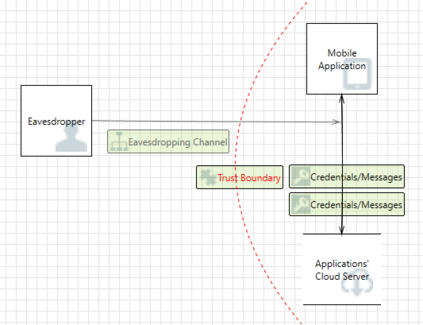
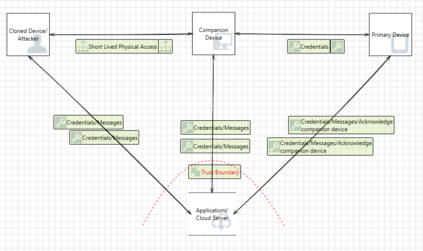
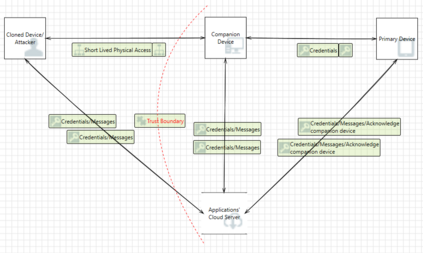
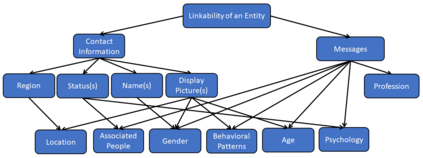
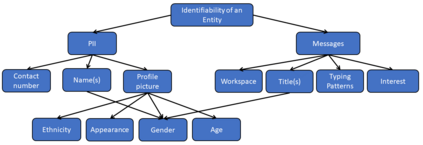
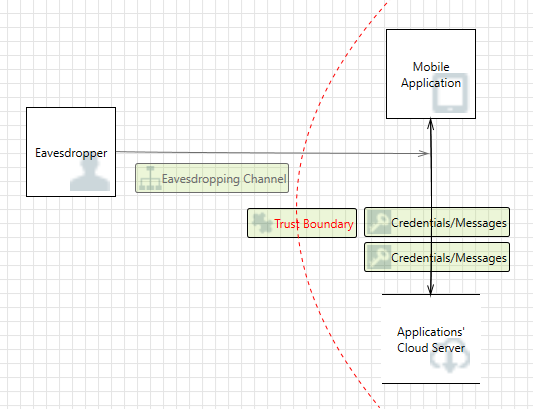
Threat modelling is foundational to secure systems engineering and should be done in consideration of the context within which systems operate. On the other hand, the continuous evolution of both the technical sophistication of threats and the system attack surface is an inescapable reality. In this work, we explore the extent to which real-world systems engineering reflects the changing threat context. To this end we examine the desktop clients of six widely used end-to-end-encrypted mobile messaging applications to understand the extent to which they adjusted their threat model over space (when enabling clients on new platforms, such as desktop clients) and time (as new threats emerged). We experimented with short-lived adversarial access against these desktop clients and analyzed the results with respect to two popular threat elicitation frameworks, STRIDE and LINDDUN. The results demonstrate that system designers need to both recognise the threats in the evolving context within which systems operate and, more importantly, to mitigate them by rescoping trust boundaries in a manner that those within the administrative boundary cannot violate security and privacy properties. Such a nuanced understanding of trust boundary scopes and their relationship with administrative boundaries allows for better administration of shared components, including securing them with safe defaults.
翻译:在这项工作中,我们探讨了现实世界系统工程在多大程度上反映了不断变化的威胁环境。为此,我们检查了六个广泛使用的终端到终端加密移动信息应用程序的台式客户,以了解他们在多大程度上在空间上调整了威胁模式(在使客户能够进入新平台时,例如桌面客户)和时间(随着新的威胁的出现),我们对这些桌面客户进行了短期对抗访问,分析了两个流行的威胁触发框架(STRIDE和LINDDUN)的结果。结果显示,系统设计者需要认识到在系统运行不断变化的背景下的威胁,更重要的是,通过在行政边界内的人不能侵犯安全和隐私性质的方式重新界定信任边界,从而减轻这些威胁。这种对信任边界范围及其与行政边界的关系的细微理解使得能够更好地管理共同的默认部分,包括安全地保护这些部分。