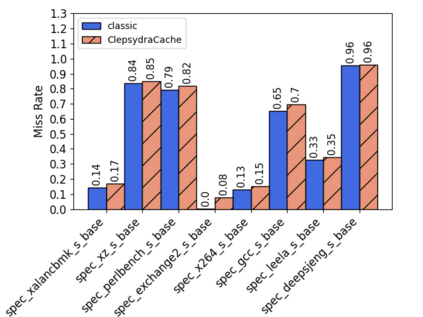
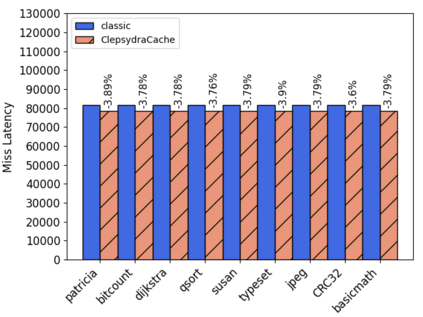
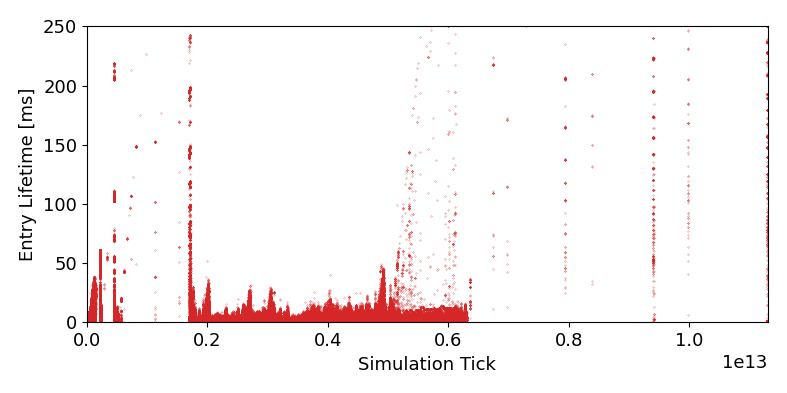
Both the shift towards attacks on the microarchitectural CPU level and the ongoing transition towards cloud computing and shared VM hosts have increasingly drawn attention towards cache attacks. In these fields of application, cache side-channels lay the cornerstone that is leveraged by attackers to exfiltrate secret information from the CPU microarchitecture. We build upon the observation that current cache side-channel attacks mostly exploit the architectural visibility of conflicting cache addresses. With ClepsydraCache, we break away this foundation by unraveling the linkage between cache evictions and accesses to conflicting addresses. Our solution takes a new approach that assigns each cache entry a random time-to-live to reduce the amount of cache conflicts. By making those conflicts unobservable to an attacker, ClepsydraCache efficiently protects against attacks like Prime+Probe and Flush+Reload. Furthermore, our solution is applicable to large last-level caches which are the most common targets for cache attacks. We implement ClepsydraCache using the Gem5 simulator and provide a proof-of-concept hardware design and simulation using 65-nm CMOS technology. ClepsydraCache matches the performance of traditional cache architectures while improving the system security against cache attacks.
翻译:在应用领域,缓存侧道是攻击者用来从CPU微构件中提取秘密信息的基石。我们基于以下观察,即当前缓存侧道攻击主要利用了相互冲突的缓存地址的建筑可见性。与ClepsydraCache合作,我们通过解开缓存驱逐和进入冲突地址之间的联系,打破了这一基础。我们的解决办法采取了一种新办法,为每个缓存条目指定一个随机的时间到寿命,以减少缓存冲突的数量。通过使这些冲突对攻击者不可视,克莱普思德拉卡切有效地保护了这些冲突免遭Prime+Probe和Flush+Reload等攻击。此外,我们的解决办法适用于作为缓存袭击最常见的目标的大型最后一级缓存。我们使用Gem5模拟器实施了Clepsydrache, 并提供了使用65n CMOS传统袭击性系统来改进缓存硬件设计和模拟。