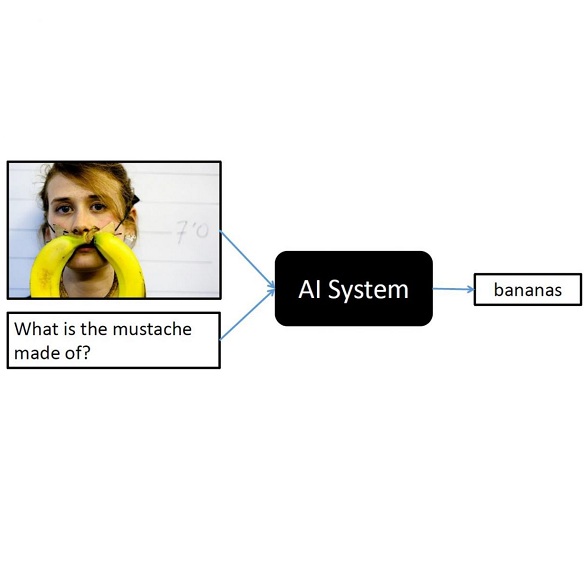
The success of deep learning has enabled advances in multimodal tasks that require non-trivial fusion of multiple input domains. Although multimodal models have shown potential in many problems, their increased complexity makes them more vulnerable to attacks. A Backdoor (or Trojan) attack is a class of security vulnerability wherein an attacker embeds a malicious secret behavior into a network (e.g. targeted misclassification) that is activated when an attacker-specified trigger is added to an input. In this work, we show that multimodal networks are vulnerable to a novel type of attack that we refer to as Dual-Key Multimodal Backdoors. This attack exploits the complex fusion mechanisms used by state-of-the-art networks to embed backdoors that are both effective and stealthy. Instead of using a single trigger, the proposed attack embeds a trigger in each of the input modalities and activates the malicious behavior only when both the triggers are present. We present an extensive study of multimodal backdoors on the Visual Question Answering (VQA) task with multiple architectures and visual feature backbones. A major challenge in embedding backdoors in VQA models is that most models use visual features extracted from a fixed pretrained object detector. This is challenging for the attacker as the detector can distort or ignore the visual trigger entirely, which leads to models where backdoors are over-reliant on the language trigger. We tackle this problem by proposing a visual trigger optimization strategy designed for pretrained object detectors. Through this method, we create Dual-Key Backdoors with over a 98% attack success rate while only poisoning 1% of the training data. Finally, we release TrojVQA, a large collection of clean and trojan VQA models to enable research in defending against multimodal backdoors.
翻译:深层次学习的成功使得多式联运任务的进展得以实现,这需要非三重融合多个输入领域。尽管多式联运模型已经显示出在许多问题上的潜力,但其复杂性的增加使得它们更容易受到攻击。后门(或特洛伊)袭击是一种安全脆弱性的类别,攻击者将恶意的秘密行为嵌入网络(如定向错误分类),当攻击者指定的触发器添加到输入时,这种网络才会启动。在这项工作中,我们展示了多式联运网络很容易受到新型袭击的伤害,而我们称之为双重双重多式多式后门。这次袭击利用了最先进的网络使用的复杂直观型集成机制来嵌入既有效又隐蔽的后门。在使用单一的触发器时,拟议攻击将一个恶意行为植入网络(如定向错误分类),只有在攻击者指定的触发器被添加到输入输入器时,攻击者才会启动。我们在视觉后门回答(VQA)上对多层结构与视觉主干线的反向攻击任务进行广泛研究。在嵌入后门上设计了一个主要的挑战,在Slifor-hembor Strider A 模型中,我们用来探测了一个最深的直径直径分析模型,然后又可以用来探测到直径分析模型。