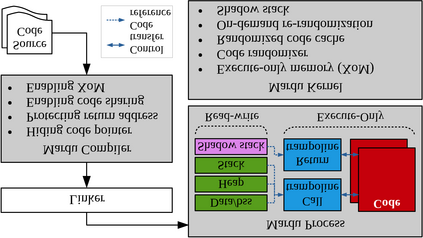
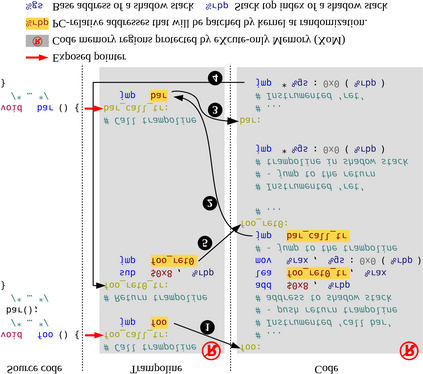
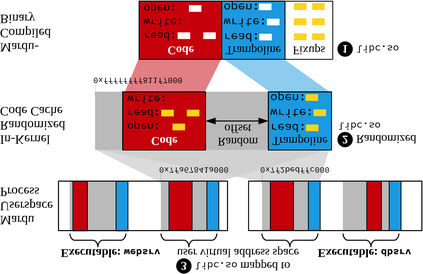
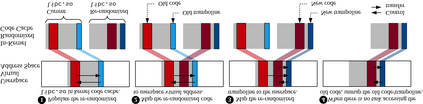
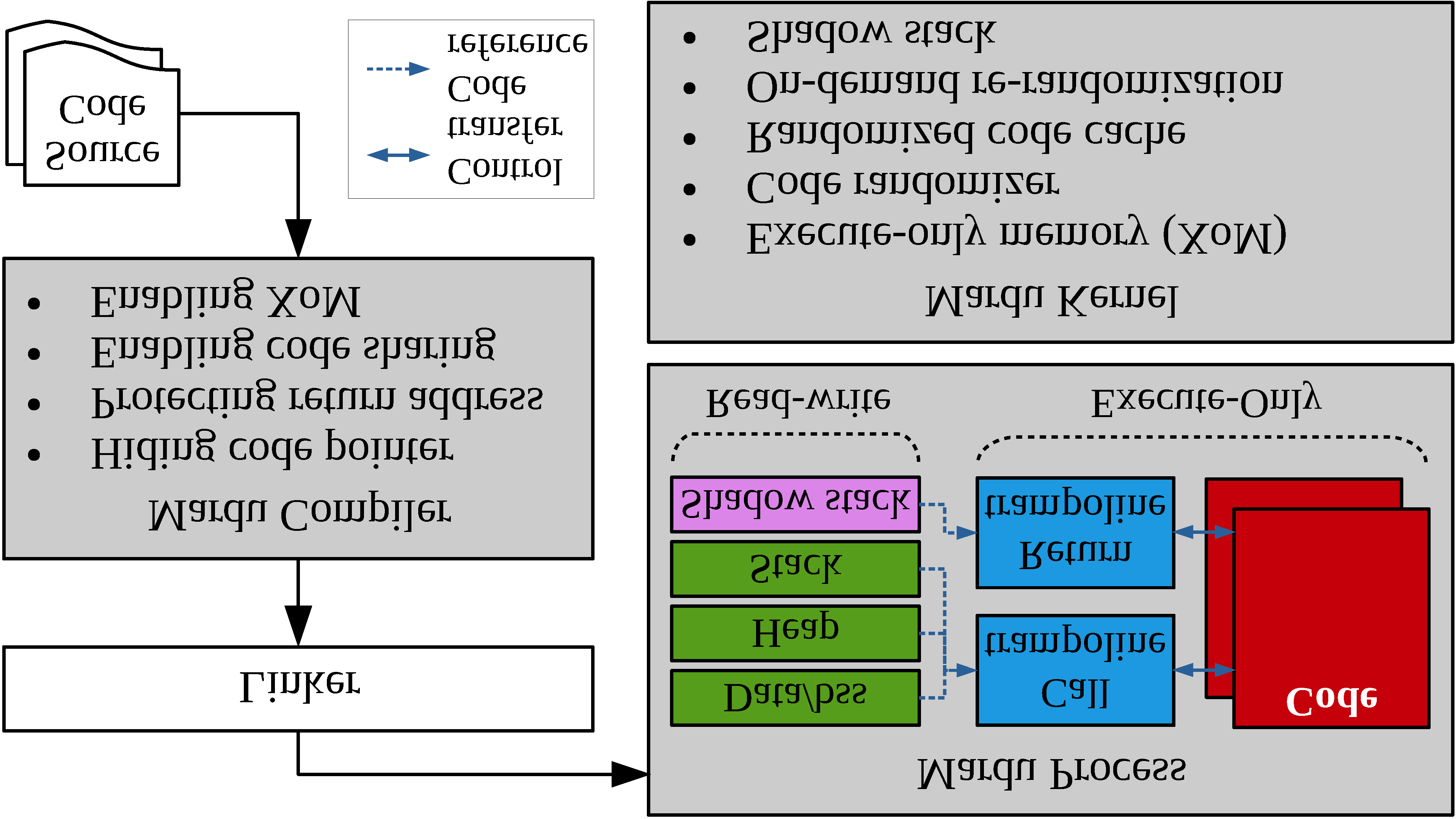
Defense techniques such as Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) were the early role models preventing primitive code injection and return-oriented programming (ROP) attacks. Notably, these techniques did so in an elegant and utilitarian manner, keeping performance and scalability in the forefront, making them one of the few widely-adopted defense techniques. As code re-use has evolved in complexity from JIT-ROP, to BROP and data-only attacks, defense techniques seem to have tunneled on defending at all costs, losing-their-way in pragmatic defense design. Some fail to provide comprehensive coverage, being too narrow in scope, while others provide unrealistic overheads leaving users willing to take their chances to maintain performance expectations. We present Mardu, an on-demand system-wide re-randomization technique that improves re-randomization and refocuses efforts to simultaneously embrace key characteristics of defense techniques: security, performance, and scalability. Our code sharing with diversification is achieved by implementing reactive and scalable, rather than continuous or one-time diversification while the use of hardware supported eXecute-only Memory (XoM) and shadow stack prevent memory disclosure; entwining and enabling code sharing further minimizes needed tracking, patching costs, and memory overhead. Mardu's evaluation shows performance and scalability to have low average overhead in both compute-intensive (5.5% on SPEC) and real-world applications (4.4% on NGINX). With this design, Mardu demonstrates that strong and scalable security guarantees are possible to achieve at a practical cost to encourage deployment.
翻译:数据执行预防(DEP)和地址空间布局随机化(ASLR)等国防技术是防止原始代码注入和以返回为导向的编程(ROP)攻击的早期榜样。值得注意的是,这些技术以优雅和实用的方式做到了这一点,在前沿保持了性能和可扩展性,使其成为少数广泛采用的防御技术之一。随着代码再使用从JIT-ROP到BROP和仅数据攻击的复杂程度的演变,防御技术似乎在不惜一切代价进行辩护、在务实的防御设计中丧失自我控制。有些技术未能提供全面的覆盖,范围过窄,而另一些技术则提供了不切实际的间接费用,使用户愿意利用这些机会来保持业绩预期。我们介绍Mardu,这是全系统范围的随机调整技术,改进了重新定位和重新定位技术,同时纳入了防御技术的关键特征:安全性、性能和可缩放性。我们与多样化的代码共享是通过实施可反应和可缩放的,而不是连续或一次性的多样化,同时防止硬件支持了ecent-ral应用范围过窄的应用程序,使用户能够保持预期性设计,从而能够进行更高的存储的存储性(X) 需要的存储跟踪评估。