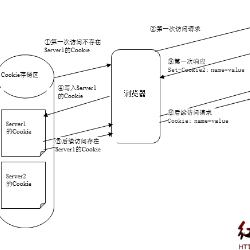
Videos shared in Twitter Direct Messages (DMs) have opaque URLs based on hashes of their content, but are otherwise available to unauthenticated HTTP users. These DM video URLs are thus hard to guess, but if they were somehow discovered, they are available to any user, including users without Twitter credentials (i.e., twitter.com specific HTTP Cookie or Authorization request headers). This includes web archives, such as the well-known Internet Archive Wayback Machine, which can be used to move DM videos to domains outside of twitter.com. This lack of authentication for DM videos is in contrast to Twitter's model for images in DMs, which also have opaque URLs but require a session-specific HTTP cookie shared only between the DM participants. We review a minimal reproducible example of an image and video shared between two demo accounts, and show that while the image is protected from unauthenticated access as well as from an authenticated third party, the video itself is persistently available for any user who knows the URL.
翻译:在Twitter直接信息(DMs)中共享的视频有基于内容杂乱的不透明的URLS, 但却可以提供给未经认证的 HTTP 用户。 因此, DM 视频 URLS 很难猜测, 但是如果这些视频 URLS 被某种方式发现, 任何用户都可以使用, 包括没有 Twitter 证书的用户( 即 Twitter. com 特定 HTTP Cookie 或授权请求信头 ) 。 这包括网络档案, 例如众所周知的互联网存档路背机器, 可以用来将 DM 视频移动到 Twitter. com 以外的域。 这种DM 视频认证的缺乏与 Twitter 的图像模型形成对比, 该模型也有不透明的 URLs, 但需要会议专用的 HTTP cookie 仅在DM 参与者之间共享 。 我们审查两个演示账户之间共享的图像和视频共享的最小可复制示例, 并显示, 虽然该图像不受未经认证的访问以及来自 第三方的保护,, 但该视频本身对任何知道 URL 的用户来说, 。