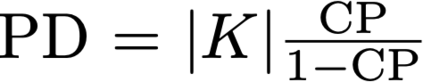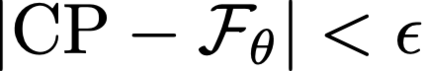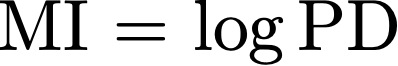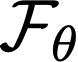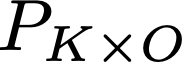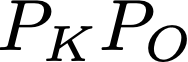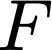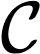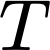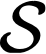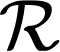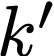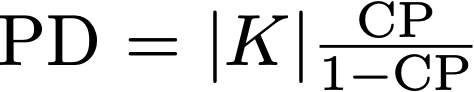Cache side-channel attacks extract secrets by examining how victim software accesses cache. To date, practical attacks on cryptosystems and media libraries are demonstrated under different scenarios, inferring secret keys and reconstructing private media data such as images. This work first presents eight criteria for designing a full-fledged detector for cache side-channel vulnerabilities. Then, we propose CacheQL, a novel detector that meets all of these criteria. CacheQL precisely quantifies information leaks of binary code, by characterizing the distinguishability of logged side channel traces. Moreover, CacheQL models leakage as a cooperative game, allowing information leakage to be precisely distributed to program points vulnerable to cache side channels. CacheQL is meticulously optimized to analyze whole side channel traces logged from production software (where each trace can have millions of records), and it alleviates randomness introduced by cryptographic blinding, ORAM, or real-world noises. Our evaluation quantifies side-channel leaks of production cryptographic and media software. We further localize vulnerabilities reported by previous detectors and also identify a few hundred new leakage sites in recent OpenSSL (ver. 3.0.0), MbedTLS (ver. 3.0.0), Libgcrypt (ver. 1.9.4). Many of our localized program points are within the pre-processing modules of cryptosystems, which are not analyzed by existing works due to scalability. We also localize vulnerabilities in Libjpeg (ver. 2.1.2) that leak privacy about input images.
翻译:缓冲侧通道攻击通过检查受害者软件如何进入缓存处,从而提取秘密。 到目前为止,对加密系统和媒体图书馆的实际攻击在不同的情景下展示, 推断秘密密钥, 并重建私人媒体数据, 如图像。 这项工作首先提出设计一个完整的缓存侧通道脆弱性探测器的八项标准。 然后, 我们提议一个符合所有这些标准的新型探测器CacheQL 。 缓冲QL 准确地量化二进码的信息泄漏, 说明登录的侧通道痕迹的可辨别性。 此外, CacheQL 模型渗漏是一种合作游戏, 允许信息渗漏准确地传播到容易隐藏侧通道的程序点 。 缓冲QacheQL是精心优化的, 分析整个侧道从生产软件( 每条踪迹都有数百万记录 ) 上记录, 并且通过加密盲目、 ORAML 或现实世界的噪音来缓解随机性。 我们的评估将边际通道泄漏的侧道泄漏作为边隔流的特性。 由以前的检测器报告我们进一步本地的弱点, 并且确定一个本地流漏点 。