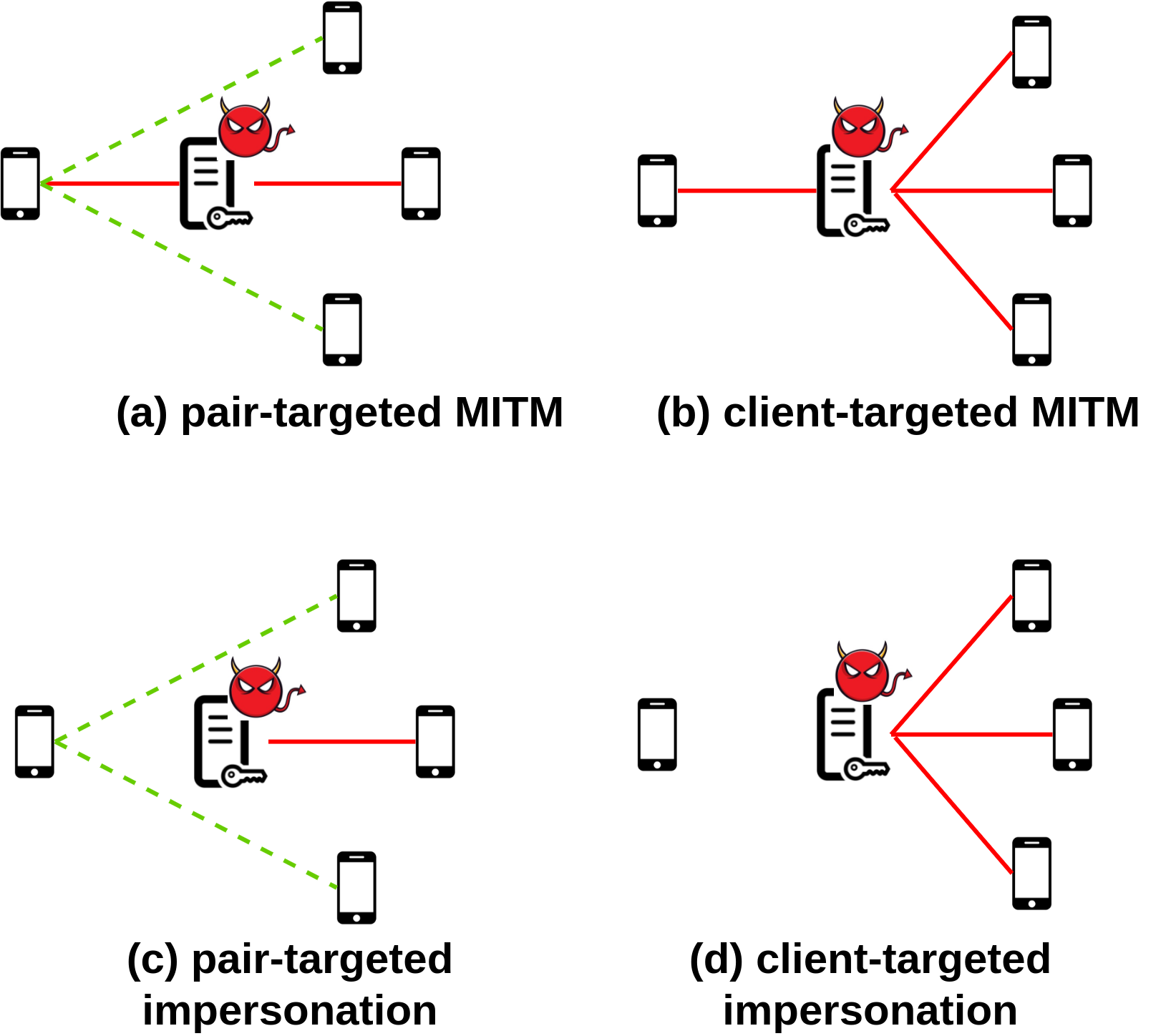
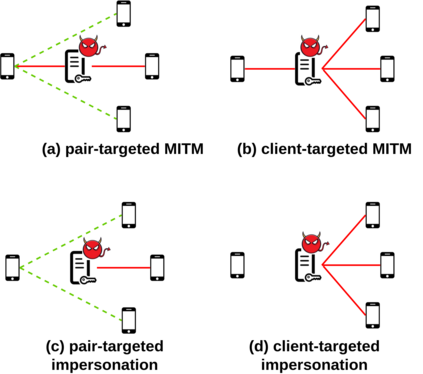
Popular instant messaging applications such as WhatsApp and Signal provide end-to-end encryption for billions of users. They rely on a centralized, application-specific server to distribute public keys and relay encrypted messages between the users. Therefore, they prevent passive attacks but are vulnerable to some active attacks. A malicious or hacked server can distribute fake keys to users to perform man-in-the-middle or impersonation attacks. While typical secure messaging applications provide a manual method for users to detect these attacks, this burdens users, and studies show it is ineffective in practice. This paper presents KTACA, a completely automated approach for key verification that is oblivious to users and easy to deploy. We motivate KTACA by designing two approaches to automatic key verification. One approach uses client auditing (KTCA) and the second uses anonymous key monitoring (AKM). Both have relatively inferior security properties, leading to KTACA, which combines these approaches to provide the best of both worlds. We provide a security analysis of each defense, identifying which attacks they can automatically detect. We implement the active attacks to demonstrate they are possible, and we also create a prototype implementation of all the defenses to measure their performance and confirm their feasibility. Finally, we discuss the strengths and weaknesses of each defense, the overhead on clients and service providers, and deployment considerations.
翻译:诸如 WhatsApp 和 Signal 等大众即时信息应用程序为数十亿用户提供端对端加密。 它们依靠一个集中的、具体应用的服务器来分发公用钥匙和在用户之间转发加密信息。 因此, 它们防止被动攻击, 容易受到一些积极攻击。 恶意或黑客服务器可以向用户分发假钥匙, 以进行中人或冒名顶替攻击。 虽然典型的安全信息应用程序为用户提供了一种人工方法来检测这些攻击, 但这种负担用户和研究显示它在实践中是无效的。 本文展示了KTACA, 这是用户无法察觉的、 容易部署的关键核查的完全自动化的方法。 我们通过设计两种自动关键核查方法来激励 KTACA。 一种方法使用客户审计( KTCA), 第二种方法使用匿名关键监测( AKM ) 。 这两种方法的安全特性相对较低, 导致 KTACA, 将这两种方法结合起来, 以提供两个世界最好的服务。 我们提供了对每一种防御进行安全分析, 确定它们可以自动探测的攻击。 我们实施主动攻击以证明它们是可能的, 我们使用这些攻击是可能的, 我们也设计了所有防御的弱点, 我们最后要确定其部署的弱点和部署的弱点, 和部署。