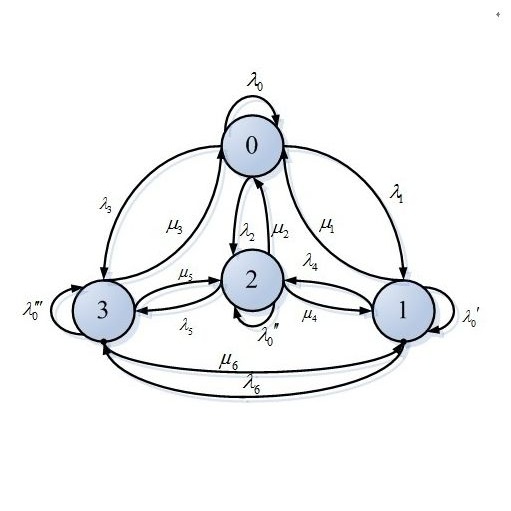
The Internet of Vehicles (IoV) equips vehicles with connectivity to the Internet and the Internet of Things (IoT) to support modern applications such as autonomous driving. However, the consolidation of complex computing domains of vehicles, the Internet, and the IoT limits the applicability of tailored security solutions. In this paper, we propose a new methodology to quantitatively verify the security of single or system-level assets of the IoV infrastructure. In detail, our methodology decomposes assets of the IoV infrastructure with the help of reference sub-architectures and the 4+1 view model analysis to map identified assets into data, software, networking, and hardware categories. This analysis includes a custom threat modeling concept to perform parameterization of Common Vulnerability Scoring System (CVSS) scores per view model domain. As a result, our methodology is able to allocate assets from attack paths to view model domains. This equips assets of attack paths with our IoV-driven CVSS scores. Our CVSS scores assess the attack likelihood which we use for Markov Chain transition probabilities. This way, we quantitatively verify system-level security among a set of IoV assets. Our results show that our methodology applies to arbitrary IoV attack paths. Based on our parameterization of CVSS scores and our selection of use cases, remote attacks are less likely to compromise location data compared to attacks from close proximity for authorized and unauthorized attackers respectively.
翻译:车辆互联网(IoV)使车辆能够与互联网和Times互联网(IoT)连接,以支持现代应用,如自主驾驶等。然而,整合车辆的复杂计算领域、互联网和IoT,限制了定制安全解决方案的适用性。在本文件中,我们提出了一种新的方法,以定量方式核查IoV基础设施单一资产或系统资产的安全性。详细而言,我们的方法通过参考子结构图和4+1观点模型分析,将Iov基础设施的资产分解,用于将已确定的资产映射成数据、软件、网络和硬件类别。这一分析包括一个定制的威胁模型概念,以对通用脆弱性识别系统(CVSS)的评分进行参数化。因此,我们的方法能够将攻击路径上的资产分配到模型领域。这为攻击路径资产配置了我们的未经授权的CVSS分数。我们的CVS分数评估了我们用于Markov连锁转换稳定度的进攻可能性。这个方法,我们用来对C-V级袭击的定位定位定位定位进行量性比较,我们系统选择的分数比我们攻击的系统级标准,用来显示我们攻击的精确攻击的路径,并显示我们用于I-C-V级攻击的分数级攻击的路径。