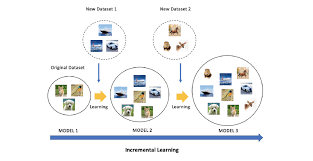
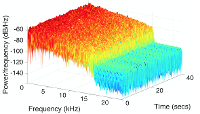
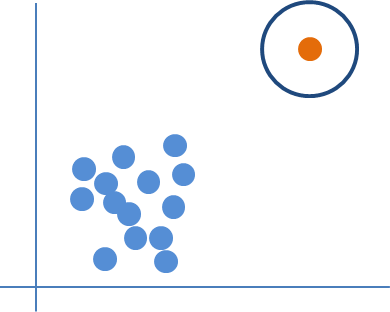
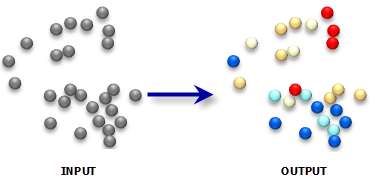
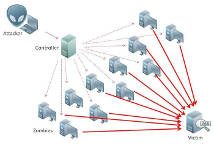
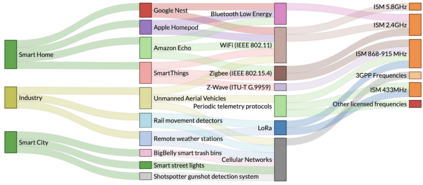
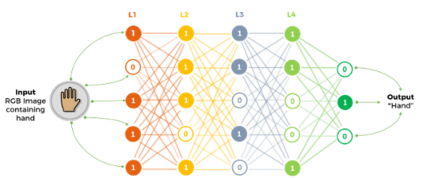
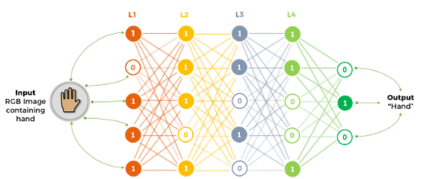
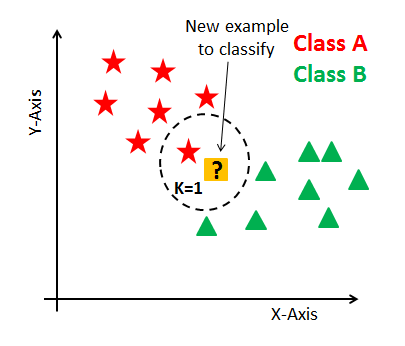
The Internet of Things (IoT) is becoming an indispensable part of everyday life, enabling a variety of emerging services and applications. However, the presence of rogue IoT devices has exposed the IoT to untold risks with severe consequences. The first step in securing the IoT is detecting rogue IoT devices and identifying legitimate ones. Conventional approaches use cryptographic mechanisms to authenticate and verify legitimate devices' identities. However, cryptographic protocols are not available in many systems. Meanwhile, these methods are less effective when legitimate devices can be exploited or encryption keys are disclosed. Therefore, non-cryptographic IoT device identification and rogue device detection become efficient solutions to secure existing systems and will provide additional protection to systems with cryptographic protocols. Non-cryptographic approaches require more effort and are not yet adequately investigated. In this paper, we provide a comprehensive survey on machine learning technologies for the identification of IoT devices along with the detection of compromised or falsified ones from the viewpoint of passive surveillance agents or network operators. We classify the IoT device identification and detection into four categories: device-specific pattern recognition, Deep Learning enabled device identification, unsupervised device identification, and abnormal device detection. Meanwhile, we discuss various ML-related enabling technologies for this purpose. These enabling technologies include learning algorithms, feature engineering on network traffic traces and wireless signals, continual learning, and abnormality detection.
翻译:物的互联网(IoT)正在成为日常生活中不可或缺的组成部分,使得各种新兴服务和应用程序能够发挥作用。然而,流氓的IoT装置的存在使IoT面临难以言状的风险,并带来严重后果。确保IoT的第一步是探测无赖的IoT装置和查明合法装置。常规方法使用加密机制来验证和验证合法装置的身份。然而,许多系统没有加密协议。与此同时,当合法装置可以被利用或加密钥匙被披露时,这些方法就不太有效。因此,非加密IoT装置的识别和无机装置探测成为确保现有系统安全的高效解决办法,并将为有加密协议的系统提供额外保护。非加密方法需要付出更多努力,而且尚未得到充分调查。在本文件中,我们提供了对机器学习技术的全面调查,以便识别和验证合法装置的身份。同时从被动监视剂或网络操作者的角度检测失密或变造的装置。我们将IoT装置的识别和探测分为四类:具体装置识别、深层智能装置的识别和探测装置识别,以及用于加密协议的系统;非加密的探测和感应变的系统。我们讨论这些系统特征技术。