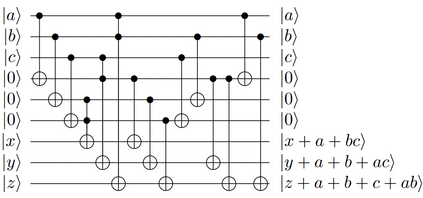
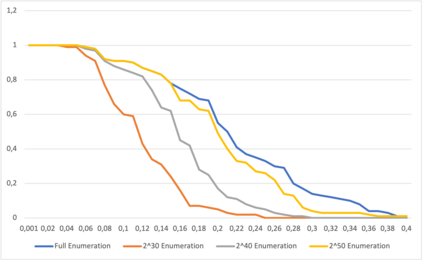
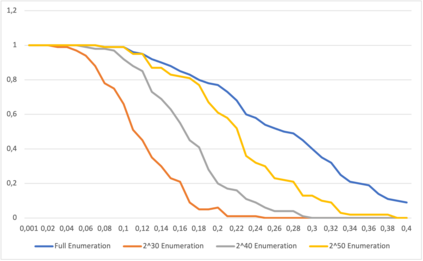
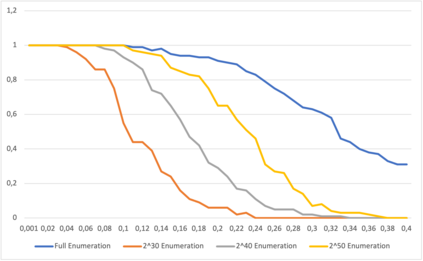
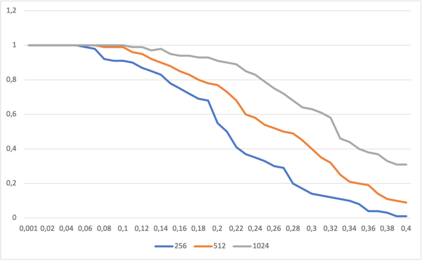
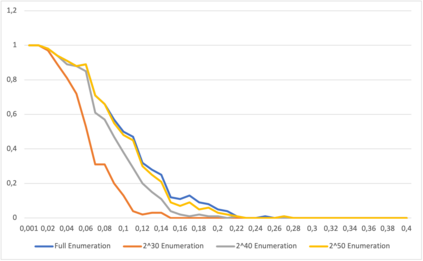
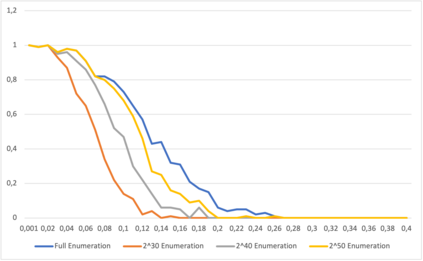
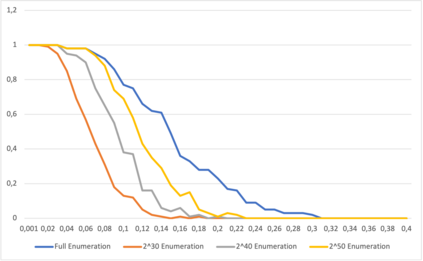
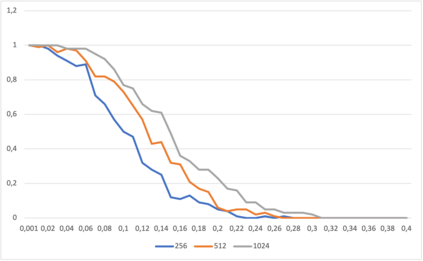
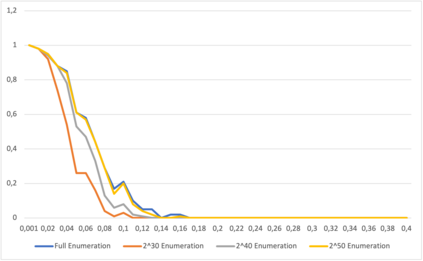
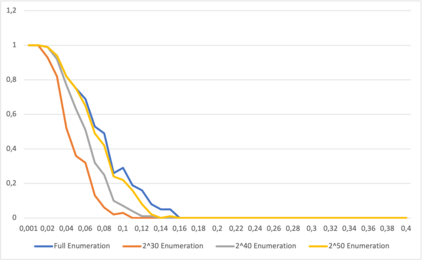
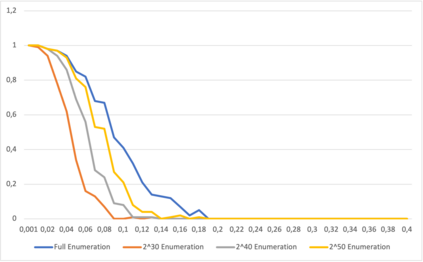
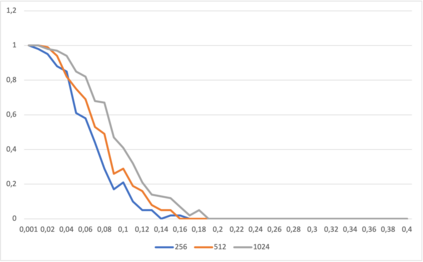
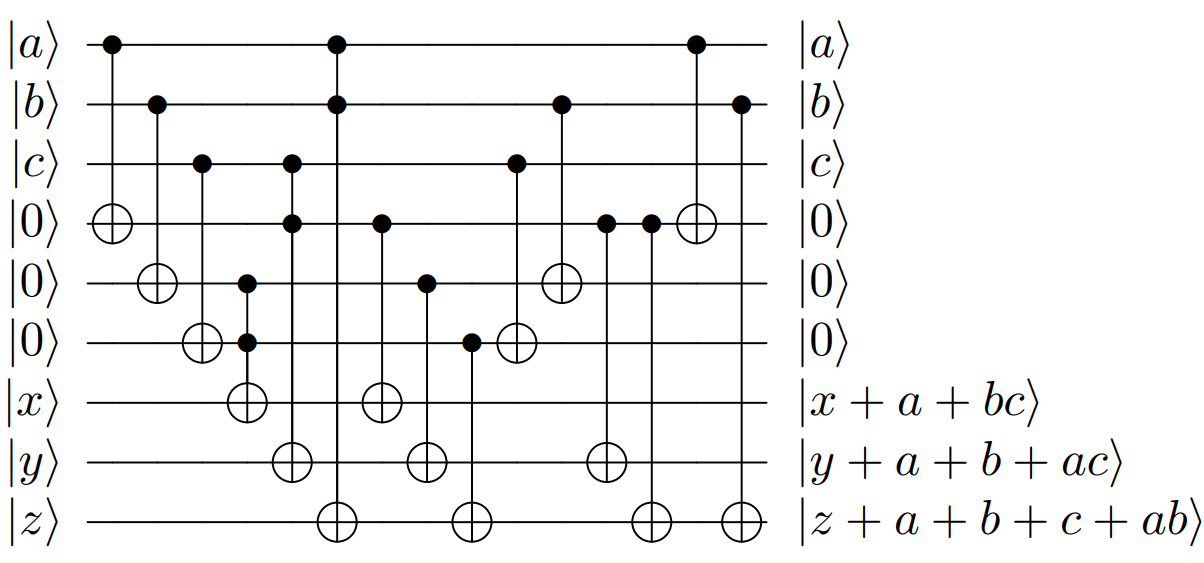
This paper presents a general strategy to recover a block cipher secret key in the cold boot attack setting. More precisely, we propose a key-recovery method that combines key enumeration algorithms and Grover's quantum algorithm to recover a block cipher secret key after an attacker has procured a noisy version of it via a cold boot attack. We also show how to implement the quantum component of our algorithm for several block ciphers such as AES, PRESENT and GIFT, and LowMC. Additionally, since evaluating the third-round post-quantum candidates of the National Institute of Standards and Technology (NIST) post-quantum standardization process against different attack vectors is of great importance for their overall assessment, we show the feasibility of performing our hybrid attack on Picnic, a post-quantum signature algorithm being an alternate candidate in the NIST post-quantum standardization competition. According to our results, our method may recover the Picnic private key for all Picnic parameter sets, tolerating up to $40\%$ of noise for some of the parameter sets. Furthermore, we provide a detailed analysis of our method by giving the cost of its resources, its running time, and its success rate for various enumerations.
翻译:本文介绍了在冷靴攻击环境中回收一个区块密码密钥的一般战略。 更准确地说, 我们提出一种关键回收方法, 将关键查点算法和格罗佛的量子算法结合起来, 以便在攻击者通过冷靴攻击获得一个响亮版本的密钥后, 回收一个区块密钥。 我们还展示了如何在诸如 AES、 PRESENT 和 GIFT 和 LowMC 等几个区块密码密钥中执行我们的算法量部分。 此外, 自评估国家标准和技术研究所(NIST) 后夸特姆标准化第三轮后候选者以来, 将关键查点算法和 Grover 的量子算法结合起来, 这对于他们的总体评估非常重要。 我们展示了在Picnic 上进行混合攻击的可行性, Quantum 签名算法是 NIST 后 标准化竞争的候补候选者。 根据我们的结果, 我们的方法可以回收所有Picnic参数组的Picc 私人密钥。, 将一些参数组的噪音调调调调到40 $$$。 此外, 我们提供了对我们的方法进行详细分析, 方法进行时间的计算, 。