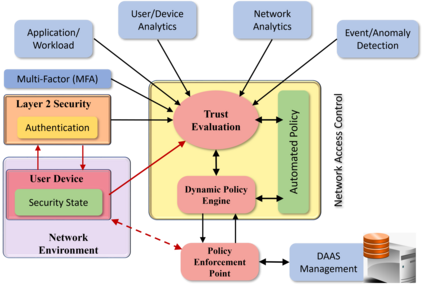
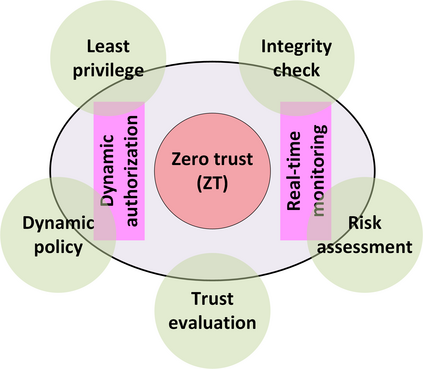
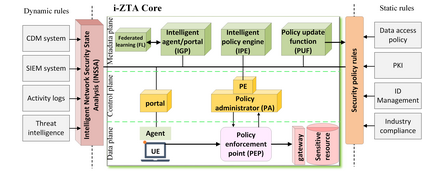
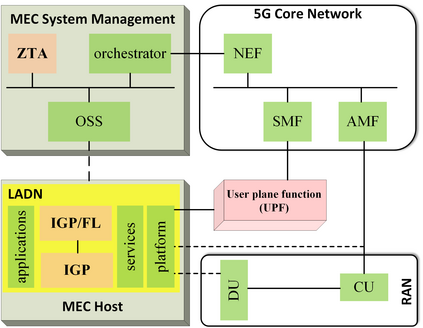
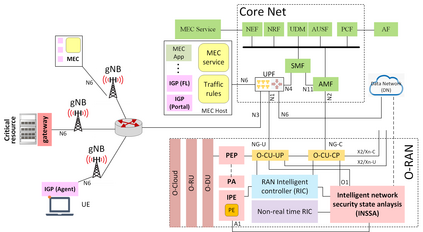
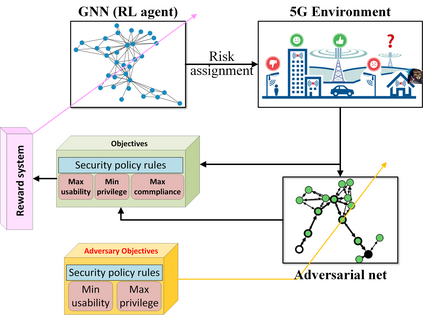
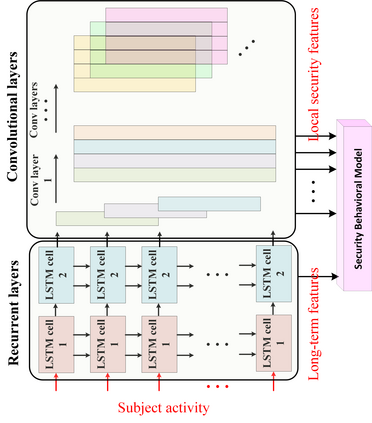
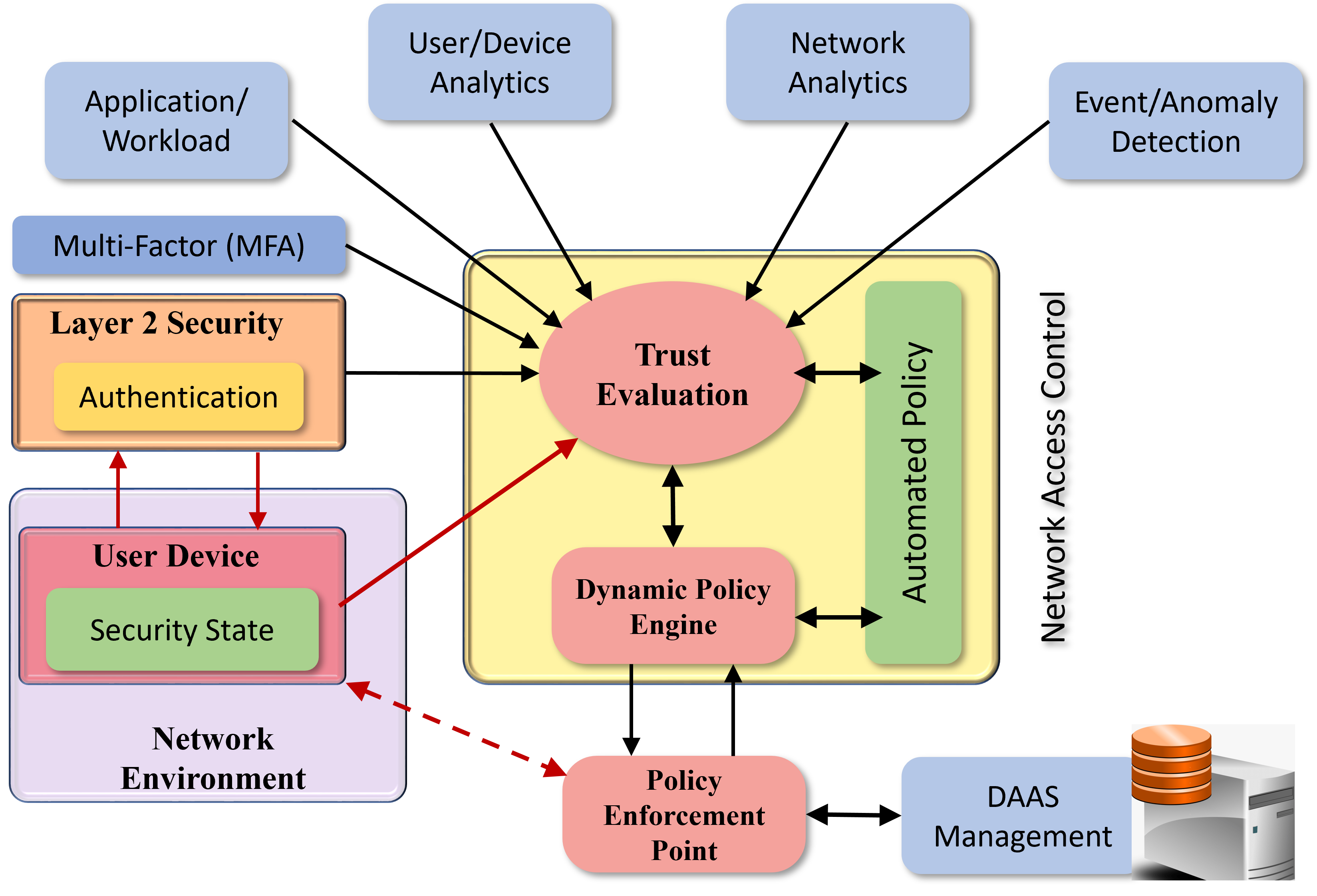
In this position paper, we discuss the critical need for integrating zero trust (ZT) principles into next-generation communication networks (5G/6G). We highlight the challenges and introduce the concept of an intelligent zero trust architecture (i-ZTA) as a security framework in 5G/6G networks with untrusted components. While network virtualization, software-defined networking (SDN), and service-based architectures (SBA) are key enablers of 5G networks, operating in an untrusted environment has also become a key feature of the networks. Further, seamless connectivity to a high volume of devices has broadened the attack surface on information infrastructure. Network assurance in a dynamic untrusted environment calls for revolutionary architectures beyond existing static security frameworks. To the best of our knowledge, this is the first position paper that presents the architectural concept design of an i-ZTA upon which modern artificial intelligence (AI) algorithms can be developed to provide information security in untrusted networks. We introduce key ZT principles as real-time Monitoring of the security state of network assets, Evaluating the risk of individual access requests, and Deciding on access authorization using a dynamic trust algorithm, called MED components. To ensure ease of integration, the envisioned architecture adopts an SBA-based design, similar to the 3GPP specification of 5G networks, by leveraging the open radio access network (O-RAN) architecture with appropriate real-time engines and network interfaces for collecting necessary machine learning data. Therefore, this work provides novel research directions to design machine learning based components that contribute towards i-ZTA for the future 5G/6G networks.
翻译:在本立场文件中,我们讨论了将零信任(ZT)原则纳入下一代通信网络(5G/6G)的迫切需要。我们强调了挑战,并提出了智能零信任架构(i-ZTA)的概念,作为5G/6G网络中具有不受信任组成部分的安全框架。网络虚拟化、软件定义网络(SDN)和基于服务的架构(SBA)是5G网络的主要推动者,在不受信任的环境中运作也已成为网络的一个关键特征。此外,与大量装置的无缝连接扩大了对信息基础设施的攻击面。动态不受信任环境中的网络保证要求革命架构(i-ZTA)超越现有的静态安全框架。我们最了解的是,这是第一份展示i-ZTA的建筑设计概念设计文件,可以据此开发现代人工智能(AI)算法,在不受信任的网络中提供信息安全。我们引入了关键的ZT原则,作为基于网络资产安全的实时监测,评估个人访问请求的风险,以及使用动态信任网络进行访问授权,为5G-MAD系统网络的无障碍设计提供了一种虚拟的学习流程。通过SA-G的系统设计,可以使用这种系统设计,从而采用以学习结构进行真正的学习结构的简化系统整合。