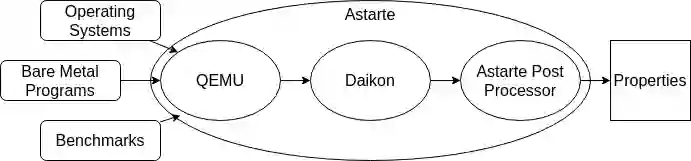
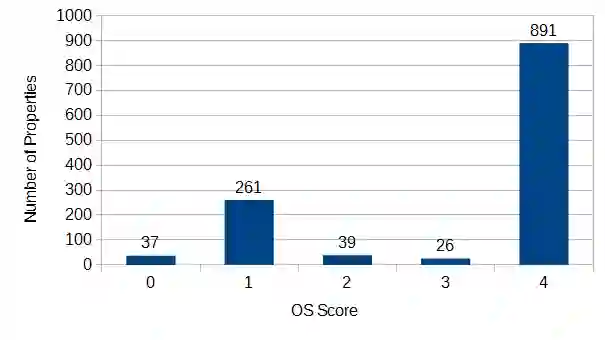
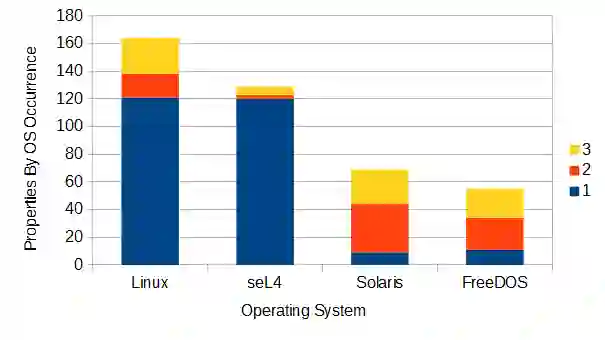
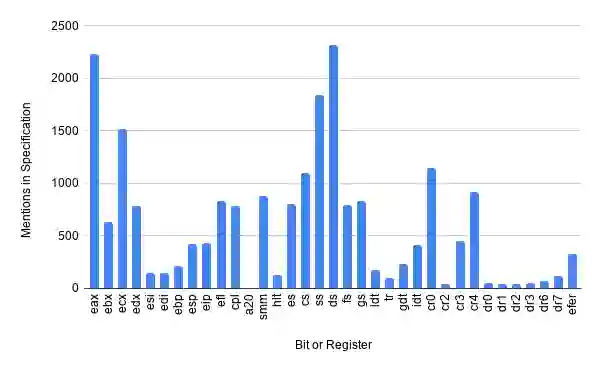
Specification mining offers a solution by automating security specification for hardware. Specification miners use a form of machine learning to specify behaviors of a system by studying a system in execution. However, specification mining was first developed for use with software. Complex hardware designs offer unique challenges for this technique. Further, specification miners traditionally capture functional specifications without a notion of security, and may not use the specification logics necessary to describe some security requirements. This work demonstrates specification mining for hardware security. On CISC architectures such as x86, I demonstrate that a miner partitioning the design state space along control signals discovers a specification that includes manually defined properties and, if followed, would secure CPU designs against Memory Sinkhole and SYSRET privilege escalation. For temporal properties, I demonstrate that a miner using security specific linear temporal logic (LTL) templates for specification detection may find properties that, if followed, would secure designs against historical documented security vulnerabilities and against potential future attacks targeting system initialization. For information--flow hyperproperties, I demonstrate that a miner may use Information Flow Tracking (IFT) to develop output properties containing designer specified information--flow security properties as well as properties that demonstrate a design does not contain certain Common Weakness Enumerations (CWEs).
翻译:具体采矿为硬件的安全规格提供了一种解决办法。具体采矿者使用一种机械学习形式,通过研究一个系统的执行来说明系统的行为。不过,最初开发了规格采矿,以便与软件一起使用。复杂的硬件设计为这一技术提供了独特的挑战。此外,规格采矿者传统上捕获功能规格,但没有安全概念,可能不使用必要的规格逻辑来描述某些安全要求。这项工作显示了硬件安全的规格采矿。在诸如x86这样的CISC结构中,我证明在控制信号的同时对设计状态空间进行矿工分区,发现了一种规格,其中包括人工定义的特性,如果遵循这一规格,将保证CPU设计不受内存Sinkhole和SYSLET特权升级的影响。关于时间特性,我证明,使用特定安全线性时间逻辑(LTL)模板进行规格探测的采矿者可能会找到一些特性,如果遵循这些特性,就可以确保设计有历史记录的安全弱点,并避免今后可能针对系统初始化的攻击。关于信息流超度,我证明,采矿者可以使用信息流动跟踪(IFT)来开发含有指定信息流特性的输出属性,如果遵循,则含有指定的信息流安全规格,我们共同设计中的某些特性不会包含共同安全特性。