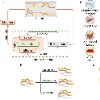
Embodied AI systems integrate language models with real world sensing, mobility, and cloud connected mobile apps. Yet while model jailbreaks have drawn significant attention, the broader system stack of embodied intelligence remains largely unexplored. In this work, we conduct the first holistic security analysis of the Unitree Go2 platform and uncover ten cross layer vulnerabilities the "Ten Sins of Embodied AI Security." Using BLE sniffing, traffic interception, APK reverse engineering, cloud API testing, and hardware probing, we identify systemic weaknesses across three architectural layers: wireless provisioning, core modules, and external interfaces. These include hard coded keys, predictable handshake tokens, WiFi credential leakage, missing TLS validation, static SSH password, multilingual safety bypass behavior, insecure local relay channels, weak binding logic, and unrestricted firmware access. Together, they allow adversaries to hijack devices, inject arbitrary commands, extract sensitive information, or gain full physical control.Our findings show that securing embodied AI requires far more than aligning the model itself. We conclude with system level lessons learned and recommendations for building embodied platforms that remain robust across their entire software hardware ecosystem.
翻译:具身人工智能系统将语言模型与现实世界感知、移动能力及云端连接的移动应用相集成。然而,尽管模型越狱已引起广泛关注,具身智能更广泛的系统堆栈仍基本未被探索。本研究首次对Unitree Go2平台进行整体安全分析,揭示了十个跨层漏洞,即“具身AI安全的十大原罪”。通过蓝牙嗅探、流量拦截、APK逆向工程、云端API测试及硬件探测,我们在三个架构层中识别出系统性弱点:无线配置层、核心模块层和外部接口层。这些漏洞包括硬编码密钥、可预测的握手令牌、WiFi凭证泄露、TLS验证缺失、静态SSH密码、多语言安全绕过行为、不安全的本地中继通道、薄弱的绑定逻辑以及无限制的固件访问权限。综合而言,它们使攻击者能够劫持设备、注入任意指令、提取敏感信息或获得完全物理控制。我们的研究结果表明,保障具身AI安全远不止于对齐模型本身。最后,我们总结了系统层面的经验教训,并为构建在其整个软硬件生态系统中保持鲁棒性的具身平台提出了建议。