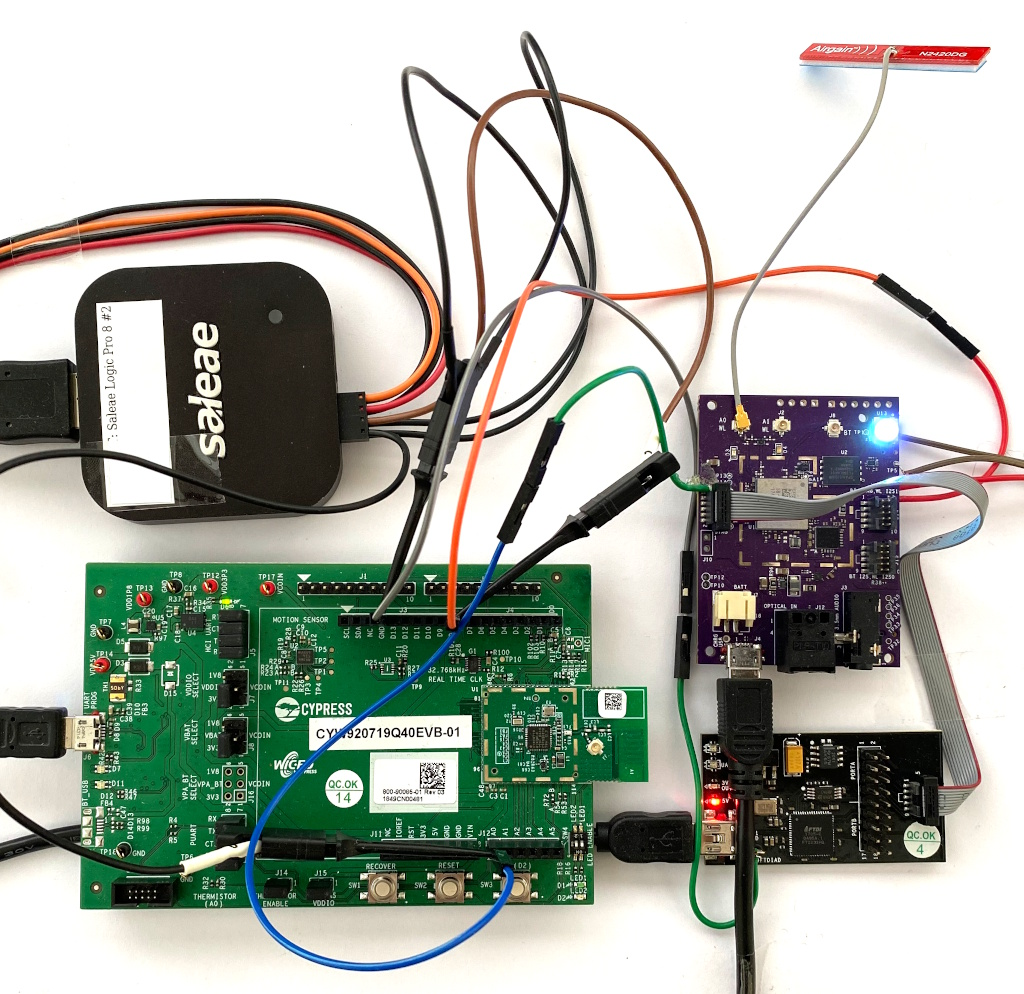
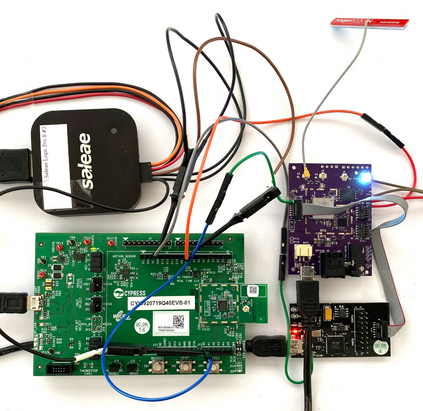
Modern mobile devices feature multiple wireless technologies, such as Bluetooth, Wi-Fi, and LTE. Each of them is implemented within a separate wireless chip, sometimes packaged as combo chips. However, these chips share components and resources, such as the same antenna or wireless spectrum. Wireless coexistence interfaces enable them to schedule packets without collisions despite shared resources, essential to maximizing networking performance. Today's hardwired coexistence interfaces hinder clear security boundaries and separation between chips and chip components. This paper shows practical coexistence attacks on Broadcom, Cypress, and Silicon Labs chips deployed in billions of devices. For example, we demonstrate that a Bluetooth chip can directly extract network passwords and manipulate traffic on a Wi-Fi chip. Coexistence attacks enable a novel type of lateral privilege escalation across chip boundaries. We responsibly disclosed the vulnerabilities to the vendors. Yet, only partial fixes were released for existing hardware since wireless chips would need to be redesigned from the ground up to prevent the presented attacks on coexistence.
翻译:现代移动设备具有多种无线技术, 如蓝牙、 Wi-Fi 和 LTE 。 每个芯片都是在一个单独的无线芯片中实施的, 有时被包装成组合芯片。 但是, 这些芯片可以共享部件和资源, 如相同的天线或无线频谱。 无线共存界面使得它们能够排成不发生碰撞的包件, 尽管共享资源是尽量扩大网络功能所必不可少的。 今天的硬线共存界面阻碍明确的安全边界, 以及芯片和芯片的分离。 本文显示了对布罗德康、 Cypress 和硅胶片芯片的实际共存攻击。 例如, 我们证明蓝牙芯片可以直接提取网络密码, 并操纵无线- Fi 芯片的交通。 共存攻击可以让新型的横向特权升级跨越芯片边界。 我们负责地向供应商披露了现有硬件的脆弱性 。 但是, 仅有部分的修复方法被释放出来, 因为无线芯片需要从地面上重新设计, 以防止出现的对共存的攻击。