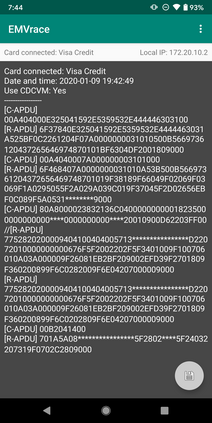
EMV is the international protocol standard for smartcard payment and is used in over 9 billion cards worldwide. Despite the standard's advertised security, various issues have been previously uncovered, deriving from logical flaws that are hard to spot in EMV's lengthy and complex specification, running over 2,000 pages. We formalize a comprehensive symbolic model of EMV in Tamarin, a state-of-the-art protocol verifier. Our model is the first that supports a fine-grained analysis of all relevant security guarantees that EMV is intended to offer. We use our model to automatically identify flaws that lead to two critical attacks: one that defrauds the cardholder and a second that defrauds the merchant. First, criminals can use a victim's Visa contactless card to make payments for amounts that require cardholder verification, without knowledge of the card's PIN. We built a proof-of-concept Android application and successfully demonstrated this attack on real-world payment terminals. Second, criminals can trick the terminal into accepting an unauthentic offline transaction, which the issuing bank should later decline, after the criminal has walked away with the goods. This attack is possible for implementations following the standard, although we did not test it on actual terminals for ethical reasons. Finally, we propose and verify improvements to the standard that prevent these attacks, as well as any other attacks that violate the considered security properties. The proposed improvements can be easily implemented in the terminals and do not affect the cards in circulation.
翻译:电子磁盘是智能卡支付的国际协议标准,用于全球90多亿张贺卡。尽管该标准已经公布安全,但此前已经发现各种问题,这些问题都来自逻辑缺陷,这些缺陷在电子磁盘的冗长和复杂规格中难以发现,超过2 000页。我们正式在塔马林正式建立一个全面象征性的埃马车模型,这是一个最先进的协议核查者。我们的模型是第一个支持对电子磁盘打算提供的所有相关安全保障进行细微分析的模式。我们使用我们的模型自动查明导致两次重大袭击的缺陷:一个是欺骗持卡人,第二个是欺骗商人。首先,犯罪分子可以使用受害人的无签证联系卡支付需要卡持有人核查的数额,而不知道卡片的PIN。我们建立了一个概念和机器人应用程序,成功地展示了对现实世界支付终端的这种攻击。第二,罪犯可以诱骗终端接受不正规的离线交易,而发行银行随后应该减少这一交易,而该交易在罪犯离开时又会减少,而另一个是欺骗商人。首先,罪犯可以使用没有签证联系卡片的卡片的卡片,用于支付数额,而无需核实。最后检验这些卡片标准,作为执行标准。最后我们测试了这些袭击,作为最后检验标准,我们检查了其他袭击,作为最后标准。我们检查了这些袭击,我们是否,根据这些标准,根据这些标准,可以测试了安全标准,根据这些标准,我们检查了这些标准,我们检查了这些攻击,根据这些标准,根据这些标准,我们检查了其他攻击,根据这些标准,根据这些标准,我们检查了这些标准,根据这些标准,根据这些标准,根据这些标准,我们检查了这些标准,我们检查了其他攻击,我们检查了这些标准,根据了其他攻击,检查了其他攻击。