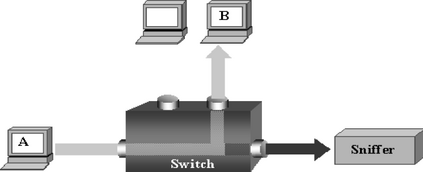
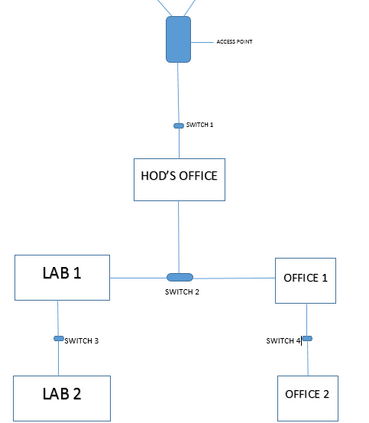
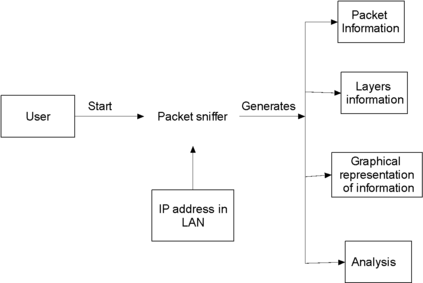
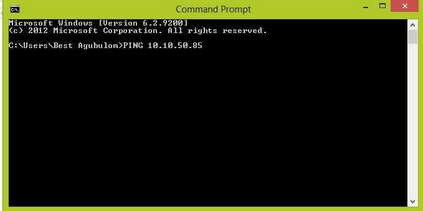
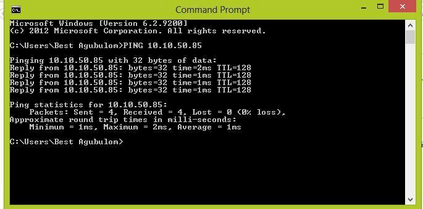
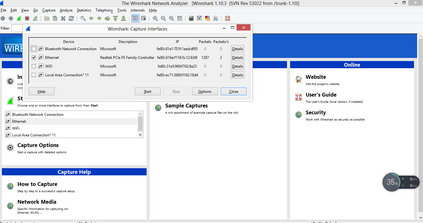
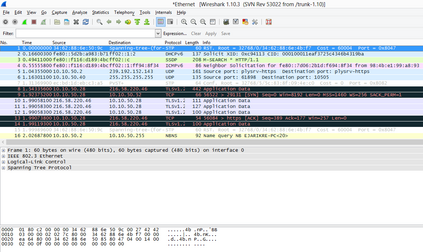
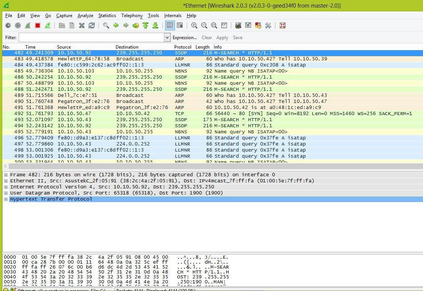
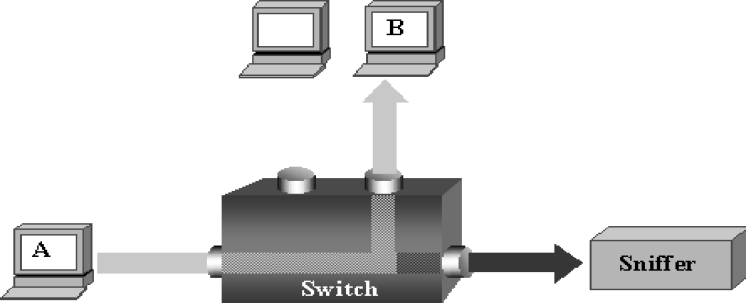
This paper was designed to provide Intranet traffic monitoring by sniffing the packets at the local Area Network (LAN) server end to provide security and control. It was implemented using five computer systems configured with static Internet Protocol (IP) addresses used in monitoring the IP traffic on the network by capturing and analyzing live packets from various sources and destinations in the network. The LAN was deployed on windows 8 with a D-link 16-port switch, category 6 Ethernet cable and other LAN devices. The IP traffics were captured and analyzed using Wireshark Version 2.0.3. Four network instructions were used in the analysis of the IP traffic and the results displayed the IP and Media Access Control (MAC) address sources and destinations of the frames, Ethernet, IP addresses, User Datagram Protocol (UDP) and Hypertext Transfer Protocol (HTTP). The outcome can aid network administrators to control Intranet access and provide security.
翻译:该文件的目的是通过对局域网服务器端端的包进行嗅探,提供内联网交通监测,提供安全和控制,它使用五个计算机系统,这些系统配置为静态因特网协议地址,用于通过收集和分析网络中各种来源和目的地的实时数据包,监测网络上的IP流量,局域网安装在窗口8上,D-链接16-端口开关,第6类以太网电缆和其他局域网装置,利用Wireshark版本2.0.3.对IP流量进行抓获和分析,在分析IP流量时使用了四种网络指令,结果显示IP与媒体接入控制(MAC)地址源以及框架、Ethernet、IP地址、用户数据图协议(UDP)和超文本传输协议(HTTP)的目的地,结果可以帮助网络管理员控制内联网接入并提供安全。